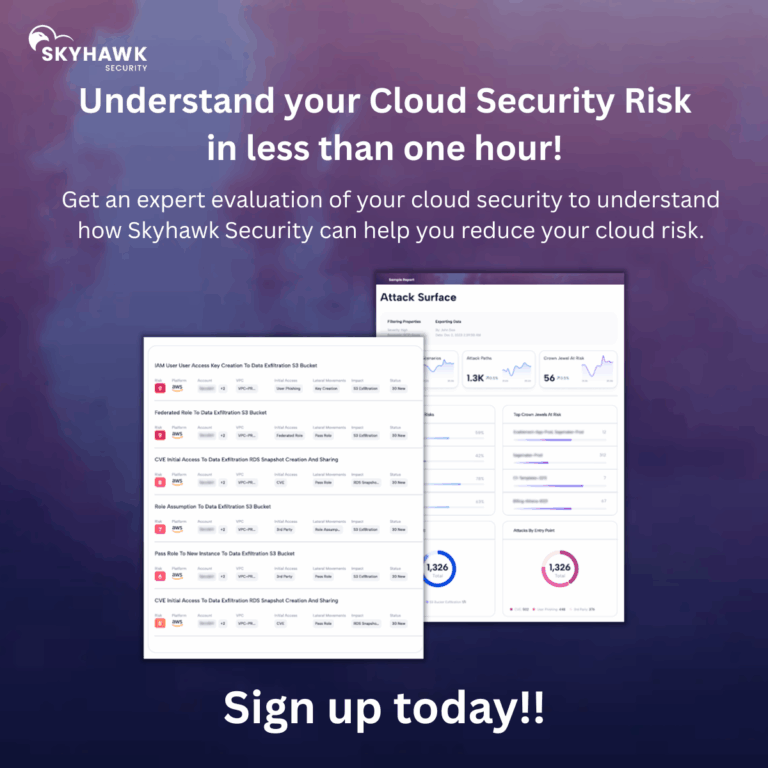
99% less noise. 100% Actionable Security.
Visibility isn't security.
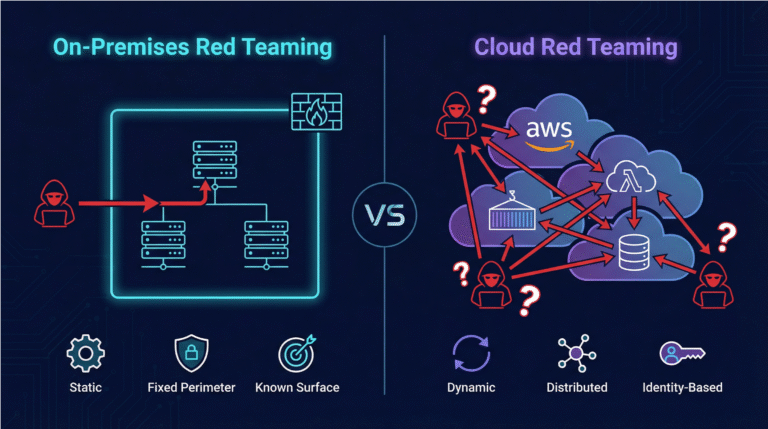
Skyhawk’s Red Team-as-a-Service brings an adversarial lens to your cloud, automatically proving which CNAPP alerts are real threats and which are just noise.
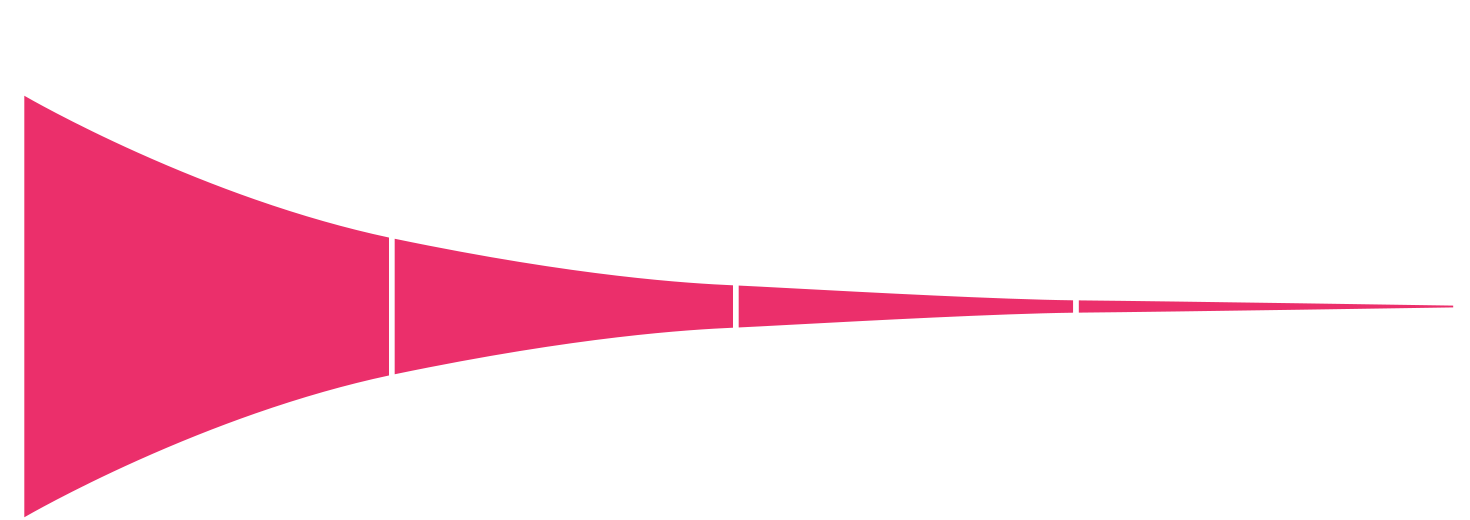






Realize SecOps Efficiency
revolutionizing cloud
breach prevention
Skyhawk Security innovative technology make us the leader in Cloud breach detection.
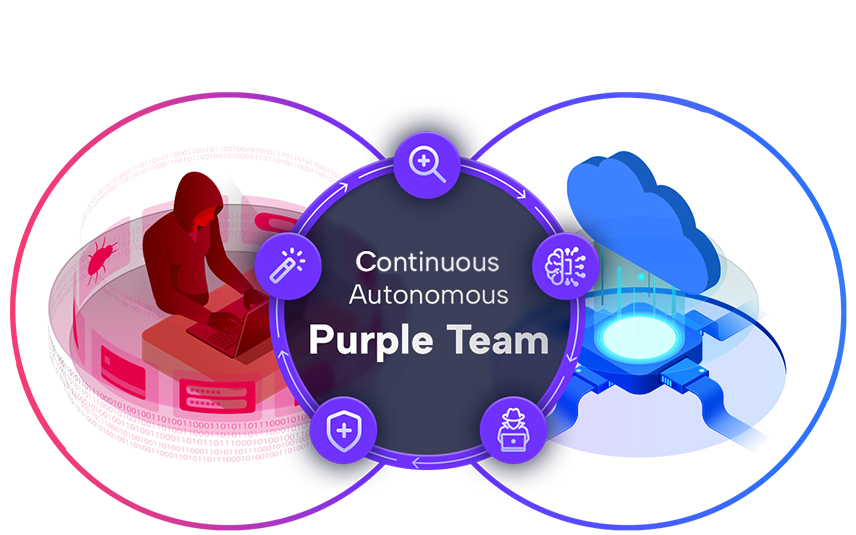
Autonomous Purple Team
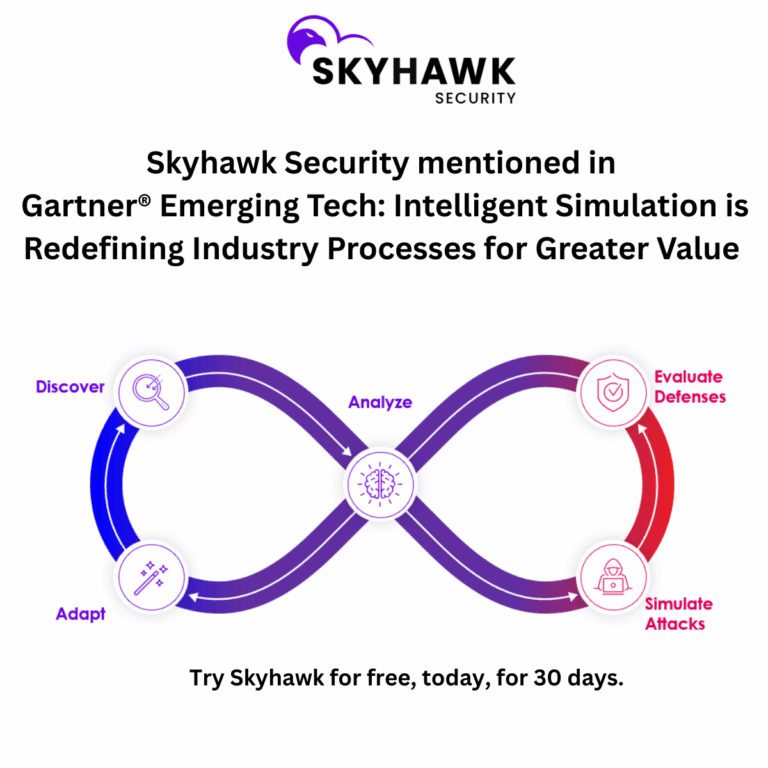
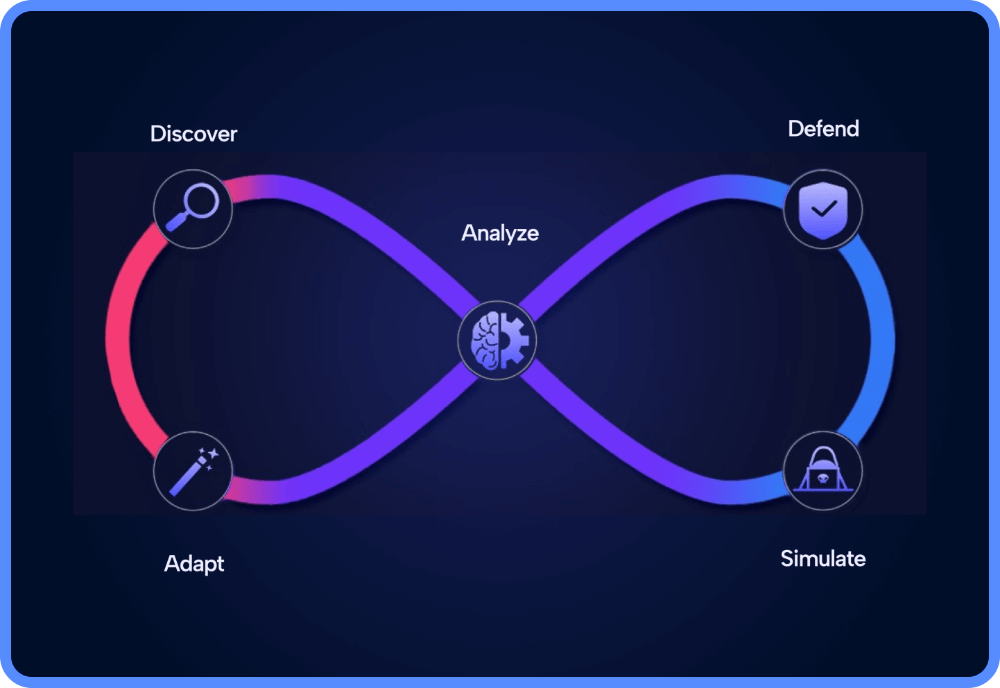
The first AI-based, autonomous purple team provides Adaptive Cloud Threat Detection and Response. It continuously analyzes customer cloud infrastructure, proactively runs attack simulation against it and uses the results to prepare verified detections, validated automated response and remediation recommendations to ensure the cloud has the most up to date security defenses in place.
Shift Left CDR
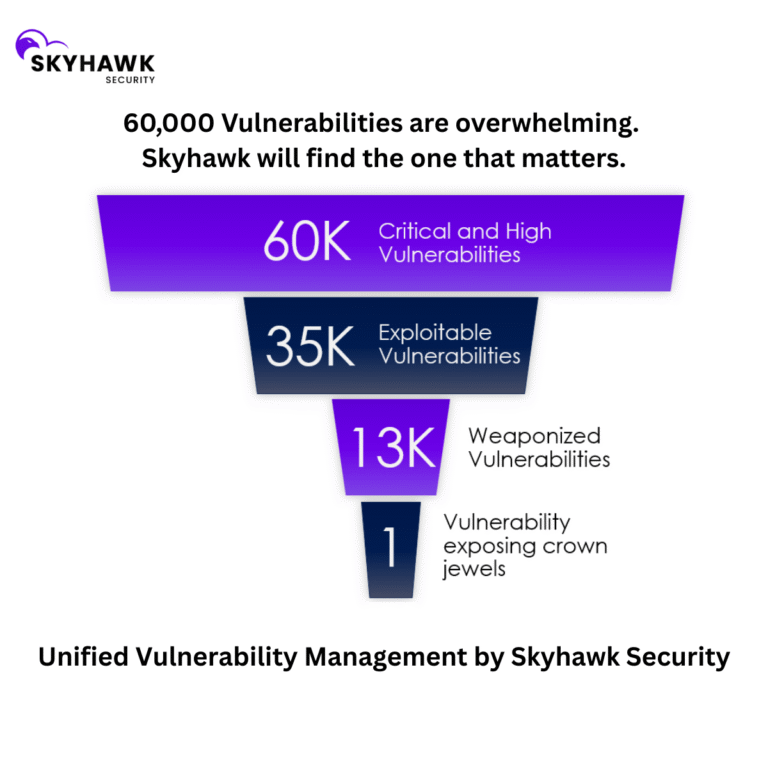
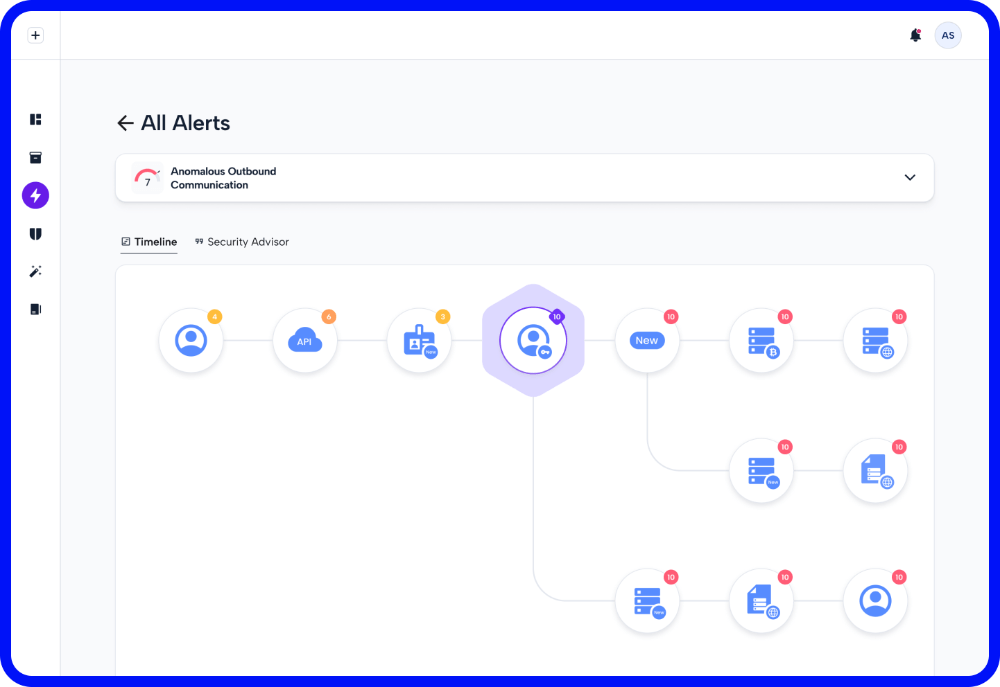
Understand how threat actors can get to your most precious data assets, your crown jewels. Leveraging machine learning, Skyhawk calculates all the paths to your crown jewels, and when a threat actor steps on that path – you get an alert fast to prevent the breach!
Operational Efficiency
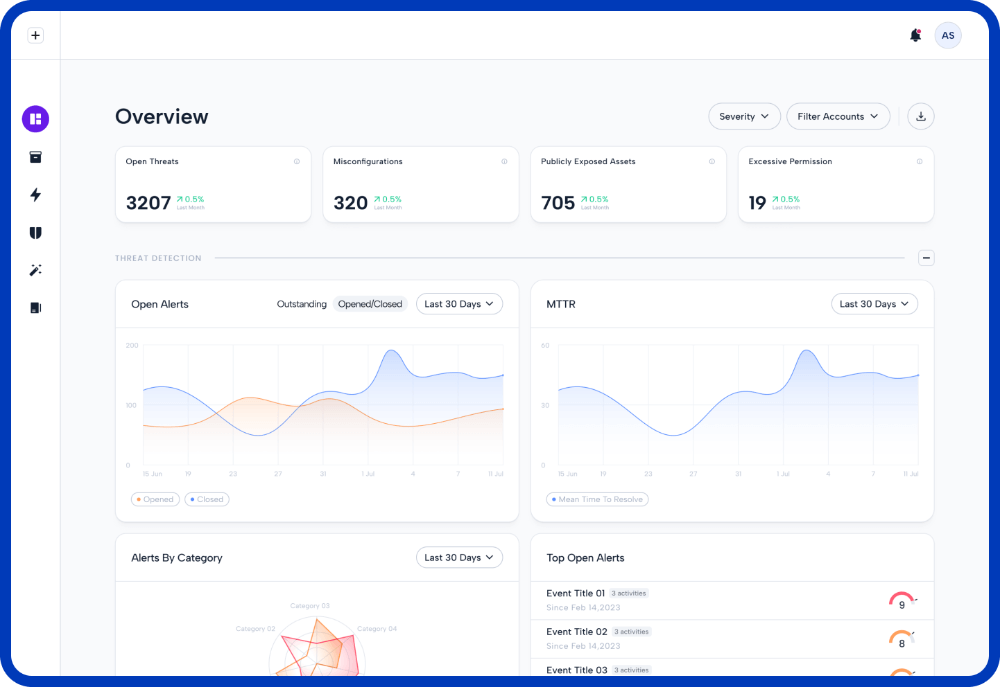
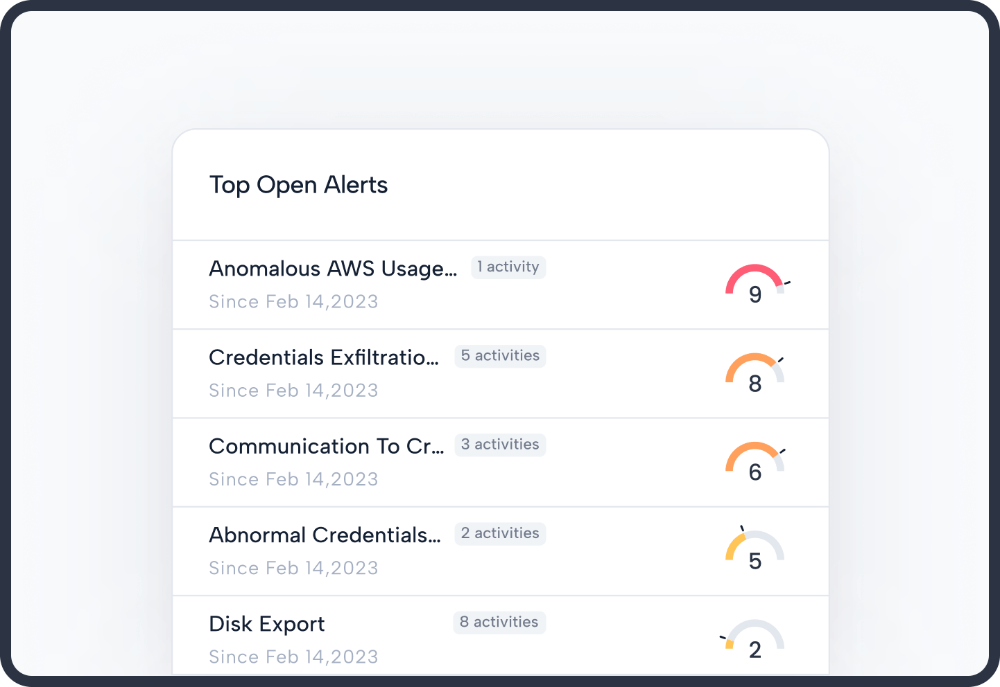
A simple, agentless deployment is complete in minutes to minimize the use of personnel and cloud resources. The platform sorts through thousands of events, to create sequences, which are then further sorted to a reasonable amount of alerts that your security team can handle. Security teams cannot effectively respond to thousands of events, but they can effectively respond to a dozen alerts.
Real-Time Observability of your Cloud to Understand Threats
Understand how threats are unfolding in your cloud, right now, so you can stop them before they become breaches. The detailed attack sequence provides all the evidence in one place so you can fully understand the behaviors and how assets were compromised.