The public cloud market is set to hit $1 trillion by 2026. As cloud providers race to grab market share, there are two clear winners: AWS and Microsoft Azure. Both providers are actively rolling out their infrastructure in new regions and expanding their capabilities to meet the growing needs of cloud-native enterprises. One such need is security.
Your data is your most valuable asset, so you and your security teams must ensure your cloud provider is protecting it. This article offers a side-by-side comparison of the most critical security components of AWS and Azure, so you can decide which one works best for your enterprise.
How cloud security works
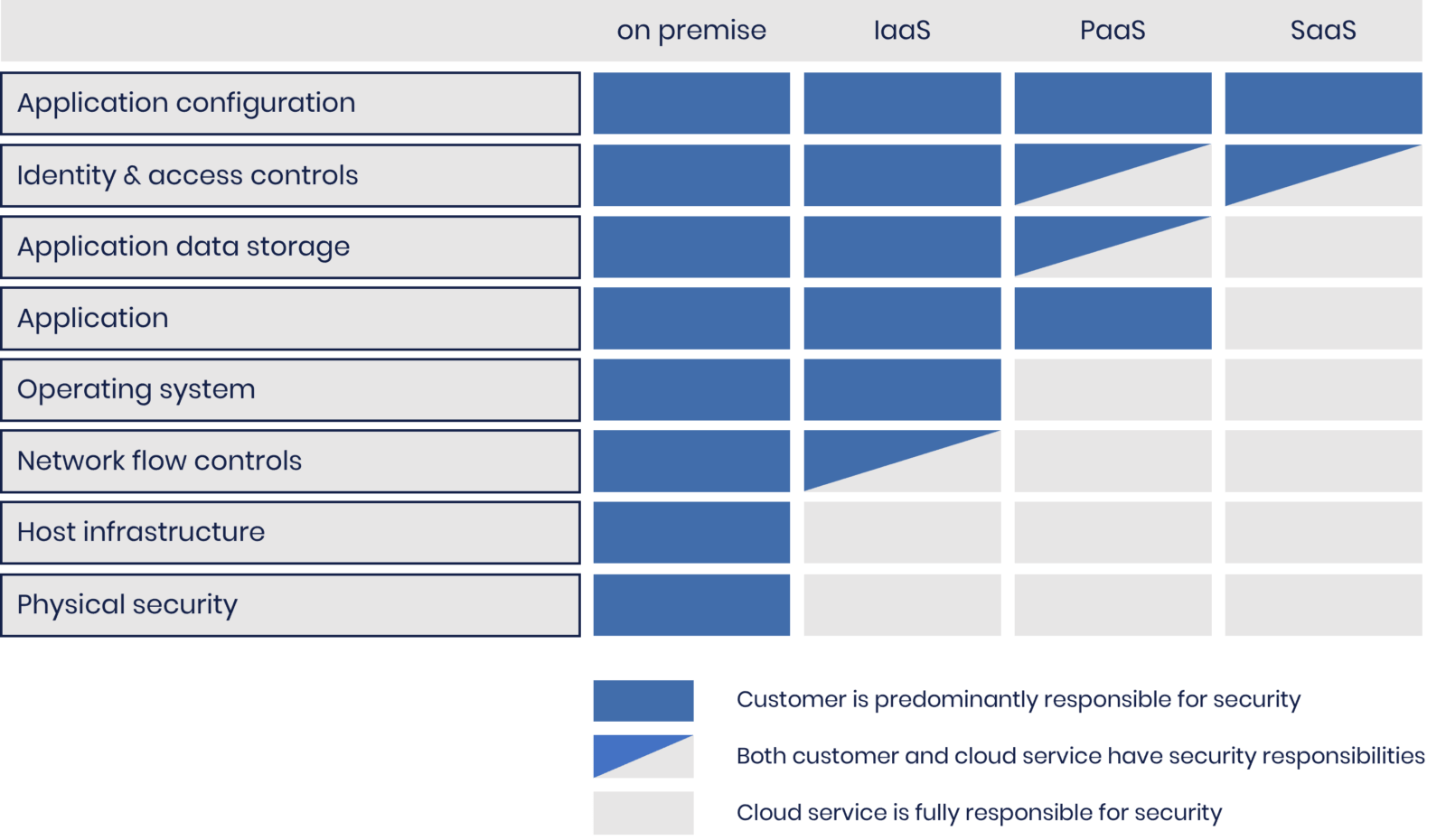
Both AWS and Azure cloud providers operate according to the shared responsibility model.
There are three main types of shared responsibility models:
- IaaS- While the customers are responsible for the OS security, software, and data they need to run their applications, the cloud provider is responsible for the security of the cloud infrastructure (the virtualization layer, disks, and network).
- PaaS- The cloud provider is responsible for all infrastructure, OS security, and applications.
- SaaS- The cloud provider is responsible for almost every aspect of security, from applications and middleware to runtime, services, and storage. Customers must still protect their usernames and passwords from phishing and social engineering attacks.
The two cloud providers have slightly different interpretations of shared responsibility for each type. For example, customers offering SaaS services on Azure and AWS are responsible for various aspects of their security:
- Azure: data, devices, accounts, and identities
- AWS: data, applications, network and firewall configurations, and client-side encryption
Azure security vs. AWS security: the key differences
As organizations store their data in the cloud, cloud services must become more resilient to the inevitable attack. In response, organizations such as the Cybersecurity and Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST) established guidelines for building infrastructures based on the six pillars of zero-trust architecture security (identity, data, infrastructure, networks, devices, applications, and APIs).

We will explore the security of the two cloud providers in more detail and how they address each pillar below.
Identity and Access Management (IAM)
For large organizations with hundreds or even thousands of users, identity and access management (IAM) is critical. IAM helps organizations manage and secure these user identities through different processes and systems: authentication, authorization, password management, access control, user provisioning, and auditing and compliance.
Microsoft Azure
Azure uses its Active Directory technology to offer basic IAM for free. It includes cloud authentication, unlimited single sign-on (SSO), multi-factor authentication (MFA), and role-based access control (RBAC).
Customers must pay for premium features such as secure mobile access, security reporting, and enhanced monitoring. A two-tiered premium subscription model costs $6 or $9 a month.
AWS
If you’re an Amazon customer, AWS IAM is free and includes features such as fine-grained permissions, single-sign-on (SSO), support for compliance, and multi-factor authentication MFA).
It also provides shared access to your AWS account and integration with many other AWS services. Only admins can assign permissions in AWS IAM, ensuring superior default security.
AWS IAM is a cloud service. For hybrid environments, however, it must integrate with Azure’s Active Directory.
Storage data encryption
Storage data encryption is a process that encodes data stored in the cloud. This encryption protects data stored from unauthorized access, breaches, or theft. Both Microsoft and AWS provide storage data encryption in transit and at rest. Each cloud provider offers key management encryption through its object storage services.
Microsoft Azure
Azure’s Blog Storage offers key-based data encryption through its Key Vault. It provides both server-side and client-side encryption using AES-256 symmetric keys.
Azure’s data storage doesn’t include support for customers to manage the keys themselves, although it plans on offering this in the future. Keys are generated using FIPS 140-2 validated hardware security modules (HSMs).
AWS
AWS offers two options for protecting data at rest:
- Client-side encryption. Encrypt the data on the client side and then upload it to AWS S3, allowing the customer to manage the encryption process, keys, and related tools.
- Server-side encryption. AWS fully manages your data by encrypting the object before it saves it in its data center and decrypting it when you download it. AWS also offers fully-managed, key-based data encryption through its Key Management System (KMS) with SSE-KMS and SSE-S3 server-side encryption.
AWS offers either fully-managed keys or support for customers managing their keys themselves. All keys are securely generated and protected using FIPS 140-2 HSMs, which can be hardware or software-based.
Data in transit is protected using Secure Socket Layer/Transport Layer Security (SSL/TLS) or client-side encryption.
Monitoring
Since cloud platforms store your data in their infrastructure, they have data at their disposal. The raw data is only helpful if properly organized and analyzed. AWS and Azure take this data and use it to offer tools that track, measure, and monitor your data to improve cloud health and operational performance.
Microsoft Azure
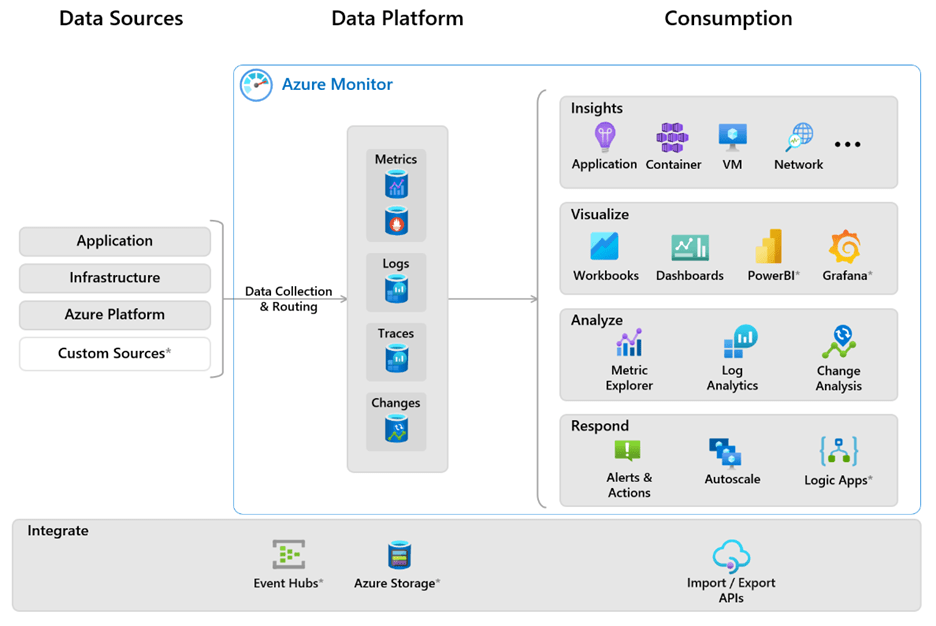
Azure’s monitoring service, Azure Monitor, organizes data by metrics or logs. Azure Monitor relies on users to set metrics rather than automatic metrics like AWS. Azure Monitor Metrics puts numeric data into a time series database for better transport and analysis. Azure Monitor Logs puts log and performance data into a single workspace and operates in near real-time. While it does offer some automation features, users can customize alerts and responses.
AWS
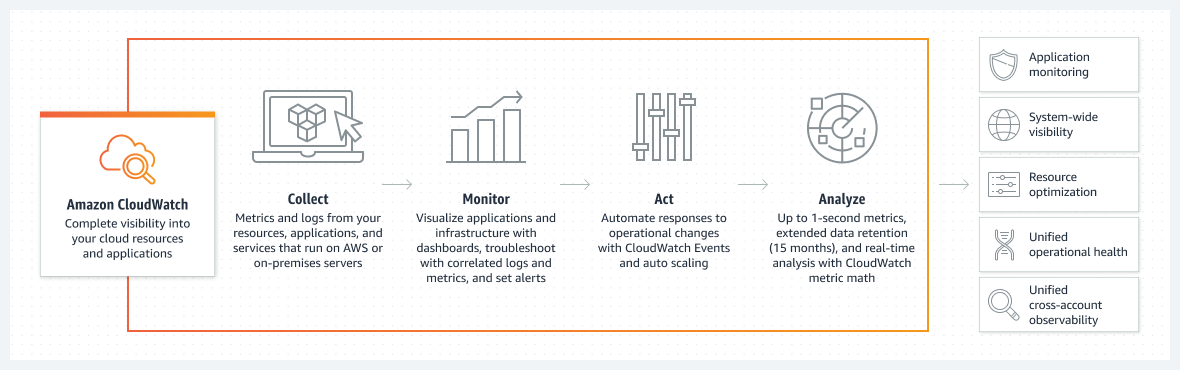
Similar to Azure Monitor, AWS CloudWatch is Amazon’s monitoring service. Metrics, logs, and event data are aggregated from your systems and applications and consolidated into a single platform. This feature includes AWS, hybrid, and on-premises applications and resource infrastructure resources.
CloudWatch features custom dashboards and an alert system to notify you of abnormal behavior. You can configure CloudWatch Alarms to notify staff of threats or automatically respond by shutting down unused instances, for example.
Threat detection
With digital assets growing, it’s becoming challenging for security teams to identify and prioritize threats. Both cloud services have responded with automated solutions that include dynamic and static threat detection, which can identify misconfigurations. The value is in spotting activity exploiting these misconfigurations.
- Dynamic threat detection: Identifies and responds to security threats in the runtime through monitoring and analyzing logs to identify behavioral anomalies. It detects threats from malware, botnets, APT, phishing, DDoS, data exfiltration, unauthorized attempts to enter a network, and more.
- Static threat detection: Identifies and responds to security threats through analysis of data at rest (e.g., files on a hard drive and network configurations).
Microsoft Azure
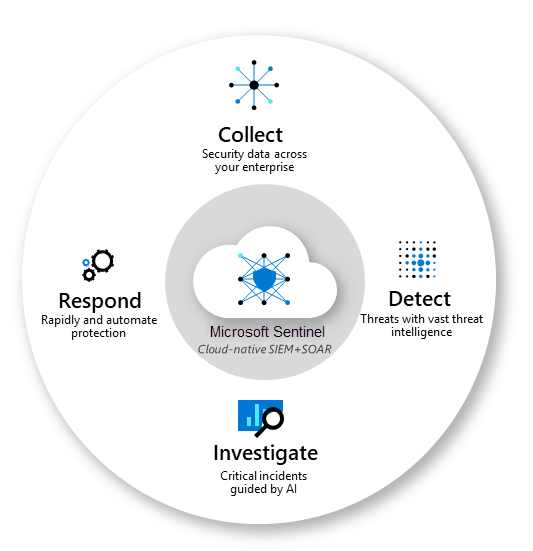
Azure Sentinel is a robust threat detection tool that includes Security Information and Event Management (SIEM), coverage of firewalls, Azure virtual machines, storage disks, and SQL databases. With trillions of signals daily and built-in machine learning, it proactively detects threats and prioritizes them according to its accurate analysis of security events.
This analysis of events is based on rules configured by the administrator. When a rule is violated, a threat alert is triggered. However, this isn’t as straightforward as it seems- if the rules are misconfigured or insufficiently customized, they can alert security teams for false positives. Furthermore, rules will not trigger when something is patched, meaning that a perfectly configured rule today may no longer work the following day.
AWS
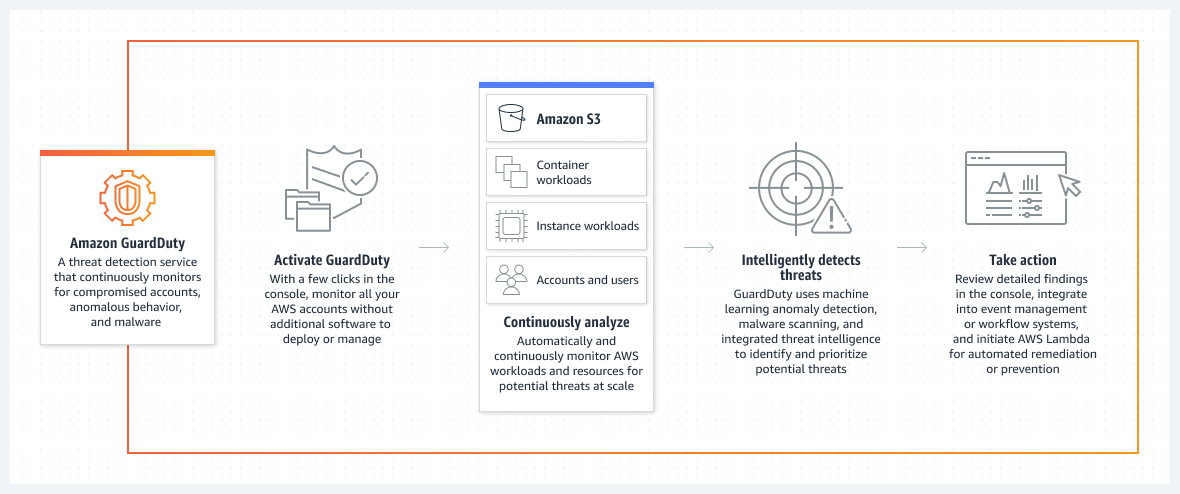
GuardDuty is AWS’s threat detection tool. It continuously monitors all AWS accounts, applications, and workloads, using machine learning to detect threats in real time. To do this, AWS GuardDuty requires you to correlate security information from all your different sources to accurately identify and address threats.
Virtual Private Network (VPN)
Data transferred over the internet is at risk from hackers, interference, and curious onlookers. Both cloud providers offer VPN services that encrypt data as it travels from a public cloud to a data center, keeping it safe from third parties.
Microsoft Azure
VNet, Azure’s VPN service, doesn’t offer the public and private segregation that AWS does. It provides a management portal, CLI, and PowerShell for customized network architectures.
AWS
Compared with Vnet, AWS’s VPN service offers more customization. Take the Virtual Private Cloud (VPC), for example, that delivers both public and private subsets to segregate networks so you can run public-facing web applications while keeping your back-end servers confidential. Both public and private subsets offer various architectural options.
Azure security vs. AWS security: which cloud is more secure?
The winner depends on the cloud you use. Both provide adequate protection, but the most suitable option depends on your business and how you use the different features. As the market leader, AWS is known for its user-friendliness, offering better customization and control. AWS has also had more time to fine-tune its features, developed many security products, from Security Hub to Macie, and works with hundreds of ecosystem partners.
Azure has similar security offerings, and it may be better for you if you use the Microsoft product suite or hybrid environments.
| Azure | AWS | |
| IAM | Free with basic features | Free for AWS customers |
| Storage data encryption | No support for customer key management | It offers a few more encryption services and functionalities, fully-managed and customer-managed keys (offers support) |
| Monitoring | It may require a slight learning curve to use, security alerts or triggers set by the user, and the dashboard is more cluttered | More user-friendly, focused on incident response, and reduced time to resolution |
| Threat Detection | More robust, proactive threat detection and response | Continuous monitoring and automated threat response |
| VPN | It doesn’t offer the public and private segregation that AWS does | It offers more customizations |
Fix only the threats that are real
No matter how many features AWS or Azure offers, it’s not enough to rely solely on either for your cloud security. Organizations that use more than one cloud provider might find it overwhelming to manage all the different features and alerts each provides.
Advanced cloud threat detection solutions such as Skyhawk Security’s Synthesis Platform deliver complete cloud protection, streamlining your monitoring process with ongoing automated scans and analysis of the threat progress. Combatting alert fatigue, we alert you only when there is an actual threat to remediate and offer a complete runtime hub contextualizing all your specific attack vectors in real time. Request a demo of our tool, and get 100% free CSPM.