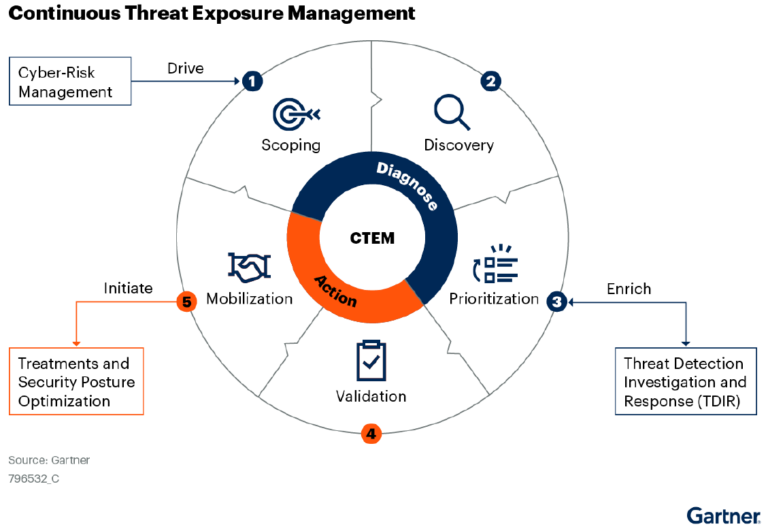
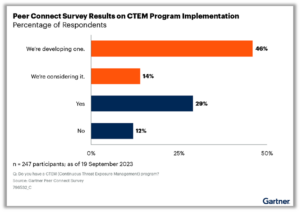
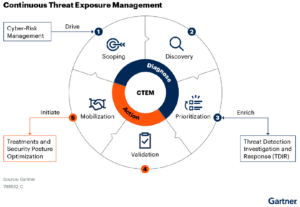
Continuous evolving clouds with continuously evolving threats need continuous threat exposure management (CTEM). This programmatic approach to managing threat exposures can help organizations dramatically reduce breaches. Many organizations are well on their way. According to a Gartner Peer Insights survey, 75% of respondents either have a CTEM program in place or are working on implementing one.
There are several strategic planning assumptions that make CTEM incredibly attractive to security teams.
By 2026, organizations prioritizing their security investments based on a continuous exposure management programme will be three times less likely to suffer from a breach.1
Through 2026, nonpatchable attack surfaces will grow from less than 10% to more than half of an enterprise’s total exposure, reducing the impact of automated remediation practices.2
Through 2025, security leaders who implement cross-team mobilization as part of their exposure management program will gain 50% more security optimization than those only prioritizing automated remediation.3
By 2027, the likelihood of breaches will reach threefold for organizations who fail to continuously manage remote access architecture and processes.4
Through 2026, more than 60% of threat detection, investigation and response (TDIR) capabilities will leverage exposure management data to validate and prioritize detected threats, up from less than 5% today.5
Organizations should be rushing to implement such a security program, especially in the cloud. Cloud attack surfaces are not completely under the control of their customers, this makes it difficult to patch for security and best practice configurations may not align with the organizations business requirements. Clouds are also completely remotely accessed, aligning to another strategic assumption. The net of the situation is: organizations that do business in the cloud need a CTEM Program.
Organizations no longer move to the cloud to try to lower costs – most organizations do not realize significant savings running their applications in the cloud. What companies do realize is the ability to spin up and spin down resources almost on demand, to meet changing business requirements. This flexibility and agility of cloud resources and services makes it very difficult to secure. A dynamic environment cannot be secured with static tools, a programmatic approach that leverages dynamic solutions that are also agile and flexible are needed. Visibility into a cloud environment also presents challenges to security. With just a credit card a company’s cloud environment can expand, making it challenging to secure.
Skyhawk’s Continuous Proactive Protection continuously analyzes customer cloud infrastructure, proactively runs attack simulation against it and uses the results to prepare verified detections, validated automated response and remediation recommendations to ensure the cloud has the most up to date security defenses in place. This continuous protection process includes learning and automated adaptation of threat detection methods. This enables security teams to take a proactive and adaptive approach to their security strategy for the very first time.
The key to a CTEM program is that it continuously evaluates the environment and seeks feedback in terms of its security and leverages this feedback to harden the environment and improve detection. The continuous feedback is key and what allows security to continuously improve to effectively manage threat exposure with adaptive threat detection. The alignment of the continuous feedback of CTEM to Continuous Proactive Protection, which also seeks feedback, makes Skyhawk Synthesis a key technology for CTEM. Organizations can look at several technologies and integrate their inputs and outputs for CTEM, or they can leverage Skyhawk Synthesis.
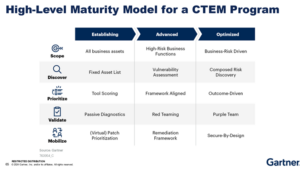
The Maturity Model of CTEM
Skyhawk Synthesis Security Platform can help organizations accelerate the maturity of their CTEM Program and can be used to automate the deployment of the entire CTEM framework. Skyhawk is continuously evaluating the cloud to find new and vulnerable cloud assets as the cloud architecture evolves. Skyhawk Security evaluates the cloud configuration to determine where the crown jewels are, and then identifies the attack paths to those assets. The attack paths that lead to the most valuable assets are prioritized for further analysis as a breach of those crown jewels presents the greatest risk to the business. This is done automatically and continuously to find the most critical threat exposures so they can be addressed fast.
Skyhawk’s Continuous Proactive Protection, an AI-based autonomous purple team, attacks and defends the cloud architecture simultaneously to find new methods that threat actors can use to penetrate the cloud. Using GenAI also helps organizations ensure they have the right defenses in place to stop AI-based attacks, which are on the rise. The output from this purple team identifies threat detection models that need to be updated, posture gaps, and can generate automated response and remediation recommendations.
Skyhawk Security is Critical for an Effective CTEM Program
Skyhawk Security’s Continuous Proactive Protection provides consistent feedback to improve an organization’s cloud posture, ML-based detection, and can generate an automated response or remediation as needed. The key that makes this successful is the platform continuously seeks out feedback from the environment leveraging Generative AI-based red team and blue team, or an AI-based autonomous purple team. As the cloud architecture changes, and posture and detection methods are updated, the platform seeks feedback to identify other weaknesses with posture or detection. The platform continues to seek out and identify threats and exposures, automatically and continuously. This continuous proactive protection helps organizations be three times less likely to suffer a breach.
1, 2: Gartner, Top Strategic Technology Trends for 2024: Continuous Threat Exposure Management by Jeremy D’Hoinne, Pete Shoard Published October 16, 2023
3 – 5: Gartner, Predicts 2023: Enterprises Must Expand from Threat to Exposure Management by Jeremy D’Hoinne, Pete Shoard, Mitchell Schneider, John Watts Published December 1, 2022
Gartner, Implement a Continuous Threat Exposure Management (CTEM) Program by Jeremy D’Hoinne, Pete Shoard, Mitchell Schneider Published July 21, 2022