According to Gartner, 75% of organizations have a Continuous Threat Exposure Management program in place or are evaluating it. Why are so many organizations embracing this approach? In our opinion, it is the embracing of continuous feedback. Cloud environments are dynamic and change continuously, and the security of the cloud environment must be continuously evaluated. As Skyhawk focuses on cloud security, continuous feedback is critical to keep your security strategies inline with your changing cloud infrastructure.
What is CTEM?
Let’s start with the goals of Continuous Threat Exposure Management or CTEM for short. It is a programmatic approach to managing exposure. There are two aspects to this – the framework itself, and how it is applied to the environment.
Let’s start with the Framework:
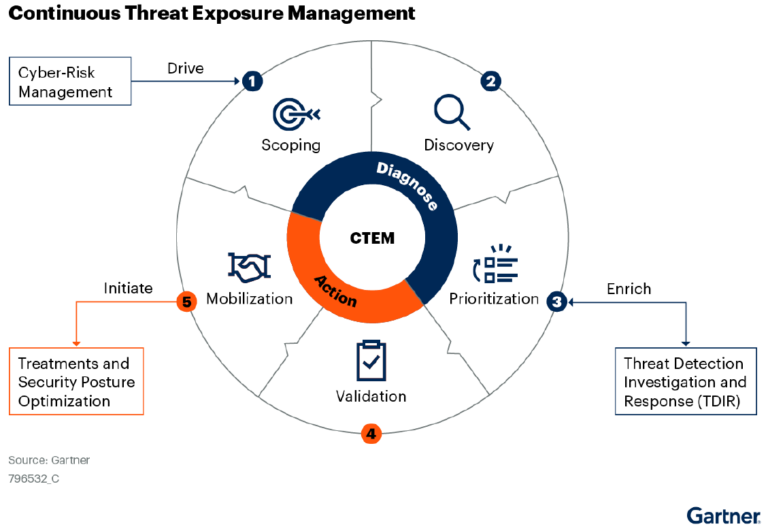
Continuous Threat Exposure Management has 5 steps.
The first step is to scope what is critical to the business. Then, define the attack surface so that critical assets can be discovered. This should go beyond misconfiguration and vulnerabilities. It should be comprehensive and show all the points of entry. The organization needs to look at cloud, SaaS, social channels, all internal and external points of engagement to data and applications.
Once scoping is complete, it is important to begin a process of discovering assets and their risk profiles. Priority should be given to discovery in areas of the business that have been identified by the scoping process, although this is not always the driver.
Prioritizing the treatment of exposures must be based on the urgency, severity, availability of compensating controls, risk appetite and level of risk posed to the organization.
Validation is the part of the process by which an organization can validate how potential attackers can exploit an identified exposure and how monitoring and control systems might react.
Cross-team mobilization shifts expected outcomes from tactical and technical responses to cybersecurity optimizations.
Implementing your CTEM Framework
The value of the framework is pretty clear. It is always looking at the value of your data assets and then helping you manage the risk to your cloud. However, in order for the framework to be effectively, you need to have a comprehensive understanding of the information infrastructure and how the assets and environments are used and what the impact would be if any of those assets or environments were breached. The security team needs to have an in-depth understanding of your data assets and the underlying infrastructure before you can implement CTEM and this cannot be done in a silo. So, before you start buying products or classifying data, the CISO really needs to create a tiger team or compliance team or both, to look at the organization’s data landscape.
The tiger team requires representation of all departments that touch or create corporate data. A full inventory of data and application assets needs to be done, and then their criticality to the business is ranked, and then their accessibility is ranked. For example, what would it mean if your website was breached? It is all public information, but what would the brand damage be? Is a breach here important than a breach to your test/dev environment? Your ordering system that drives 80% of revenues? These are the kinds of questions that the tiger team will address. It will help create a framework to prioritize the security issue based on the value of the asset and the protection or lack of protection that the asset has.
How is CTEM different from other threat detection approaches?
There are three key attributes in the programmatic approach of CTEM that you do not see in other security disciplines.
- Continuous: The continuous aspect of CTEM is different from other approaches, and this aligns particularly well with CTEM for cloud. Cloud architectures are changing rapidly and often to meet changing business needs and requirements. This is why organizations move to the cloud. However, organizations that invest in cloud, need a security framework that takes into account the frequency of this change.
- Feedback: It is not enough to just continuously evaluate the cloud security and cloud architecture – the feedback needs to be implemented and used to update the cloud security. What vulnerabilities need to be addressed, what posture issues, permissions, and more to update the cloud security. This continuous evaluation of cloud architecture to improve cloud security reduces the overall threat exposure of the cloud, reducing the exposure of the business.
- Information driven alerts: Threat actors are generally aware of deficiencies in patch management and lack of prioritization. In other words, if they know medium –severity vulnerabilities rarely get addressed, it presents a path of potentially least resistance. This is not the case for Skyhawk. It does not just look at the alert and simplicity or sophistication of the alert. It looks at the alert and the value of the business asset behind it. This information enables security teams to prioritize alerts and prevent cloud breaches.
Similar to CI/CD, CTEM is always evaluating and updating the infrastructure and seeking out gaps in the security strategy that is protecting this infrastructure.
Skyhawk’s Purple Team delivers Cloud CTEM
Skyhawk Security’s Continuous Proactive Protection helps organizations discover their crown jewel assets and then the GenAI based red team and blue team see how defenses hold up against an attack. This helps organizations prioritize the ease of penetrating their defenses along with the value of the data assets at the end of the attack so they know where to start updating their security posture, threat detection, and response and remediation.
As Skyhawk is continuously evaluating the cloud as it updates, organizations can truly realize the value of the cloud. Skyhawk’s AI-based autonomous purple team is constantly evaluating defenses as the cloud architecture evolves, ensuring your most valuable cloud assets are protected.
Skyhawk Security is not a one-stop shop for your Cloud-native CTEM framework, but it does deliver a significant portion of the capabilities. Many organizations already have too many security tools, so adding several tools to implement this framework is not feasible, but implementing one more product is.