According to industry experts, remediation can take up to four months on average to address critical and high Cloud-Native Application Protection Platform (CNAPP) findings, like those from Wiz. Threat actors will not wait these months for any security team to resolve them – this is their window of opportunity. Threat actors will exploit these weaponized threats, putting your business at risk.
Additionally, CNAPPs typically raise hundreds of thousands of findings that need to be remediated. This is overwhelming for any security team regardless of the size. The time it takes to evaluate these issues and determine which are false alarms and which need to be addressed further widens the threat actor’s window of opportunity.
What is the window of opportunity?
According to industry sources, it can take up to 128 days to resolve critical alerts – that is more than four months!
Figure 1: This image represents the window of opportunity for threat actors, over four months in some cases!
It can take 114 days for high level alerts, which is almost four months as well. Again, threat actors will not wait – they will take advantage of these vulnerabilities and exposures.
A recent press release based on the 2025 Cloud Security Report from Checkpoint also found that 65% of organizations suffered a cloud-security incident in the past year, and only 9% detected the incident within the first hour, and only 6% remediated it within that hour! This lack of action provides threat actors with an opportunity to breach your cloud while the security team works on hardening issues. There needs to be a second line of defense while hardening the cloud, this is where cloud threat detection and response comes in. CDR will detect the threats that are leveraging the unhardened cloud surface.
Close the window with Skyhawk Security
Skyhawk Security’s executes continuous tabletop exercises with the AI-based Purple Team. It is built with AI-based Red Team, a cloud-native Breach and attack simulation (BAS) which continuously validates the security controls of your cloud. Skyhawk goes one step further and doesn’t just analyze just at the technical exploitability, it analyzes what is truly weaponized.
The platform also evaluates threats to your most valuable business assets, the crown jewels, and prioritizes those as they present a clear and present risk to your business. This information arms the security team with the prioritization they need to address to close the attacker’s window of opportunity and stop cloud breaches.
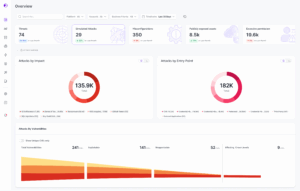
Figure 2: This funnel is a graphical representation of a customer case study: the number of critical and high vulnerabilities (identified by Wiz), and how Skyhawk Security Adversary Inteligent Simulation prioritized those vulnerabilities down to the ONE that actually put the business at risk.
How does it work?
Skyhawk’s AI-based Purple Team uses a cloud-native agentless Breach and Attack Simulation module (BAS), to produce step-by-step attack scenarios. It then maps your security controls for each step of the attack, providing a unified view of simulated attacks along with suggested preventative remediations, threat detection and response (the layers of defense). This continuous autonomous process ensures there are compensating controls in place to detect threats while the application and DevOps teams implement the risk/path remediation steps.
Skyhawk closes this window in three ways:
- First, the platform shows what weaponized threats need to be addressed first – prioritized by the business value of the asset. How many CNAPP or CSPM findings do you have in your tool right now? Wouldn’t it be helpful to know the ones that are actually putting your business at risk? Skyhawk can do that – now. For one of our customers, Skyhawk reduced 500,000 issues to just 300 that require resolution, more than a 99% reduction.
Figure 3: Overview of Skyhawk Security’s Platform, showing how Skyhawk Security sorts through thousands of CNAPP Findings and toxic combinations to get to the few that actually pose a risk to the business.
- Second, it detects malicious behaviors to find threat actors that are exploiting these weaponized threats now. This accelerates detection. Check out this blog which shows that Skyhawk Security detects these incidents in minutes, and some cases, just one minute! Contrast that with the report findings mentioned earlier.
- Third, there are some CNAPP alerts that cannot be addressed due to architectural considerations. In these cases, the platform improves the detections with the rehearsals, so any activity that is attempting to exploit the exposure, is alerted. The platform can go further and create verified automated response to automatically stop these activities.
A Comparison: Skyhawk Security and CNAPP
| Key Capabilities | Skyhawk Security | CNAPP |
| AI-Driven Preemptive Purple Team | Yes – Combines AI-powered simulations with behavioral analysis to proactively identify and mitigate risks, prioritized by business value. | No – Does not provide proactive AI-driven purple team capabilities. |
| Real-Time Interactive Cloud Detection and Response (CDR) | Yes – Interactive AI-driven CDR provides actionable insights during attack simulation and live incidents, aligning to Zero Trust principles. | No – Lacks real-time interactive CDR. |
| Detection Methodology | AI-Based – Implements model-based detection and precise threats correlation; models customized for the cloud, updated daily. | Rule-Based – Relies solely on static rule-based detections, which threat actors will reverse engineer. |
| Incident Correlation | Advanced AI Correlation – Identifies polymorphic attacker behavior across cloud environments. | Principal-Based – Focuses on isolated identity principles without contextual polymorphism. |
| Signal-to-Noise Ratio | Optimized – AI-driven detection significantly reduces noise, enabling SOC efficiency and clarity. | High Noise – Generates high alert volumes, adding strain to SOC teams. |
| Risk Assessment: Weaponized vs. Theoretical Risks | Weaponized – Differentiates and mitigates practical attack paths (e.g., lateral movement, privilege escalation). | Theoretical – Focuses on isolated theoretical vulnerabilities rather than real-world exploitability. |
Want to learn more?
- Check out the webinar! Learn how Skyhawk closes this window of opportunity.
- Try Skyhawk free for 30 days! You can get started in one hour.
- Book a meeting with Skyhawk to learn more!