Skyhawk Synthesis Security Platform
Prevent Cloud Breaches with Accurate Threat Detection
Cloud Infrastructure Entitlement Management (CIEM)
Protecting your cloud starts with access.
Cloud Identity and Entitlement Management (CIEM) helps organizations effectively manage permissions, users, group and roles while ensuring the productivity of your team.
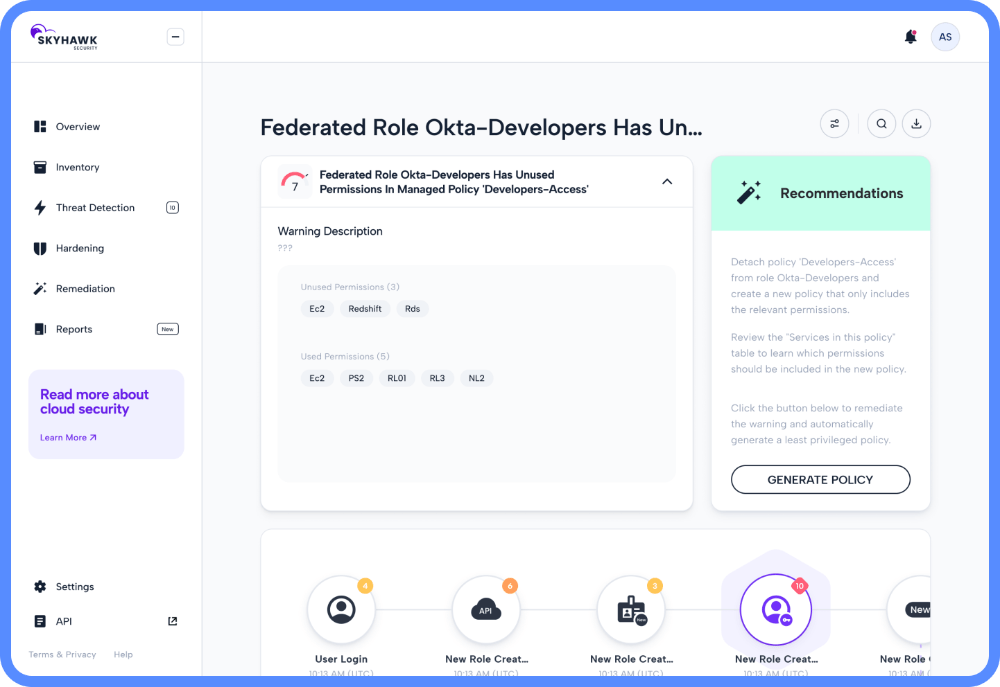
Skyhawk Synthesis takes a full inventory of permissions and policies connected to users, groups and roles. The unused permissions can then be safely removed, reducing the overall attack surface for hackers.

Right-size permissions to stop breaches

Effectively manage the attack surface

Identify Used and Unused Permissions
Security teams often over-assign permissions to ensure the productivity of the team is not impacted. It makes things easier for them, but it also expands the attack surface. Skyhawk Synthesis automatically identifies the unused permissions so the security team can adequately assess your cloud’s exposure and risk.
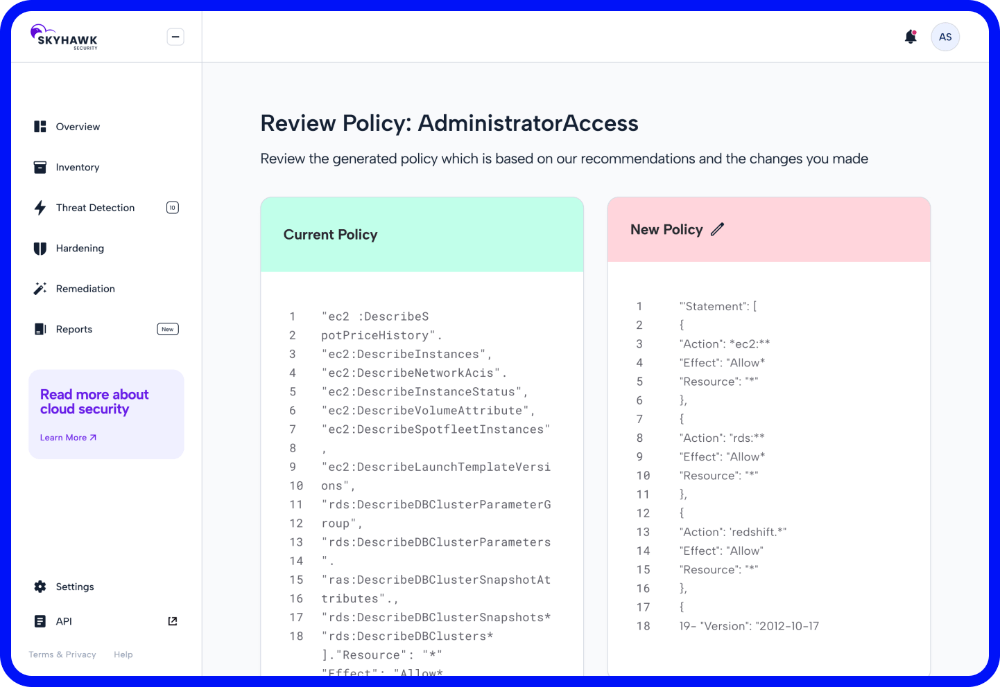
Insight-driven Policy Remediation
Security teams need automation to help them more accurately secure their cloud. Skyhawk Synthesis automatically creates new permission policies to reduce the attack surface for threat actors without impacting employee productivity.
Our Cloud Breach Prevention Consists of One Single Platform for CSPM, CIEM and CDR
Skyhawk Security’s Cloud threat Detection and Response (CDR) platform contextualizes and correlates all of your specific attack vectors in real time – to reduce alerts and focus only on actual attacks as they unfold. It provides scored and validated realerts, and insights on what you can do to address them.