In recent Gartner® research, Emerging Tech Disruptors: Top 5 Early Disruptive Trends in Cybersecurity for 2025, it is noted that there will be a shift from detection and response to preemptive cyber defense using key AI-advancements like Simulation Digital Twins.
Strategic Planning Assumption: By 2030, preemptive cybersecurity solutions will account for 50% of IT security spending, up from less than 5% in 2024, and replace traditional “stand-alone” detection and response solutions as the preferred approach to defend against cyberthreats.
Strategic Planning Assumption: By 2030, simulation data will underpin 20% of strategic business decisions, up from approximately 1% in 2024.
Skyhawk Security supports these strategic planning assumptions as the Continuous Autonomous Purple Team supports a preemptive security strategy by leveraging Simulation Digital Twins to accurately predict how threat actors will compromise your high value business assets, the crown jewels. Skyhawk Security has been at the forefront of these advancements as we recognized a key issue in cloud security, using AI and machine learning in several ways to prevent cloud breaches.
- CDR driven by three layers of AI and machine learning models: These models sort through logs, telemetry and other data, which are sequenced into malicious behavior indicators, which are correlated into the attack sequence
- Integration with LLMs: In March of 2023, Skyhawk Security integrated LLMs to promote the attack sequence to an alert up to 78% faster without producing false positives.
- Continuous Autonomous Purple Team: An AI-based red team “attacks” and AI-based blue team and then prioritizes weaknesses based on the business value of the asset exposed by that weakness.
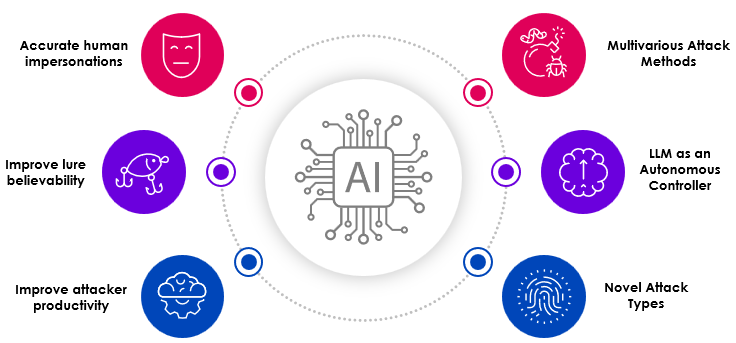
Unfortunately, AI is also available to threat actors so they can create faster, smarter, and more believable attacks. Security teams need to use AI to fight AI. Check out Skyhawk’s blog to learn more: Fight AI-based threats with AI-based Security.
Continuous Autonomous Purple Team
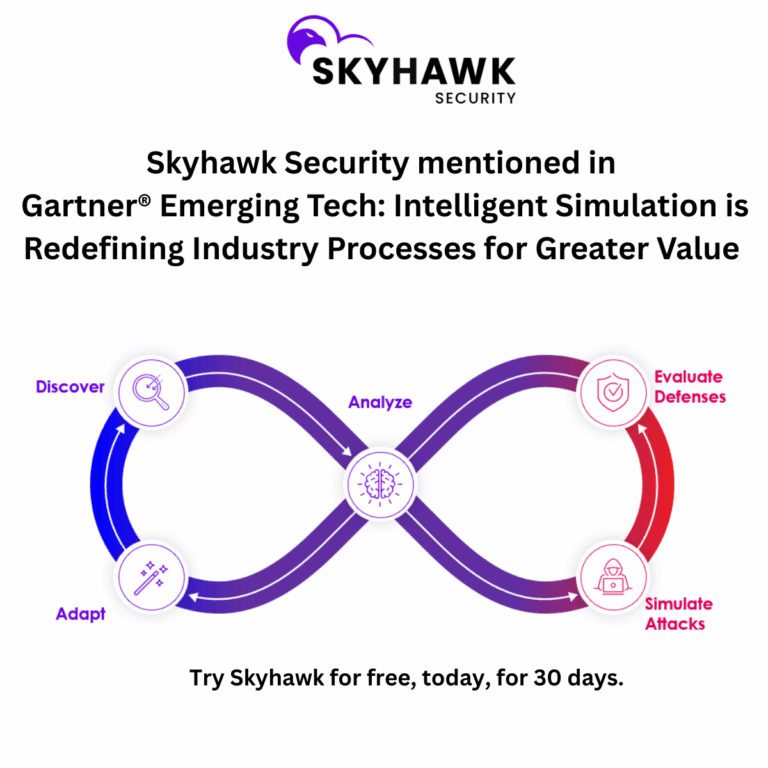
Skyhawk Security’s Continuous Autonomous Purple Team preemptively identifies threats with a Simulation Digital Twin environment to surface weaknesses in your cloud’s security and then prioritize what should be fixed by the business value of the at-risk asset. Security teams can act before an attack occurs to protect their most valuable assets and limit threat actors’ activities to lower-level incidents versus data breaches that require SEC reporting, or worse, are posted on social media by the attacker.
How does it work?
- Discover: Identifies all cloud assets and maps out the paths threat actors could use to gain access.
- Analyze: the configuration, vulnerabilities, and security controls that are in place are fully analyzed and attack recipes are created.
- Simulate Attacks: Leveraging the attack recipes, the Simulation Digital Twin is used to fully execute the attacks.
- Evaluate Defenses: Where the attack is successful, is prioritized based on the business value of the asset that is vulnerable.
- Adapt: CDR machine learning models are updated for more accurate detections, pre-verified automated response is put in place for verified alerts.
Benefits
- Where the red team gets passed the blue team, the security team gets valuable insights identifying posture findings or abandoned roles/permissions
- Validates alerts as the platform has “seen” the attack already in the simulation so it knows what will happen if the attack progresses.
- With validated alerts, validated automated responses can be used! The platform knows it does not want something to progress – so it will trigger the response and stop the threat
- Addresses the Progressive Technology-based Adversarial-Driven Risk
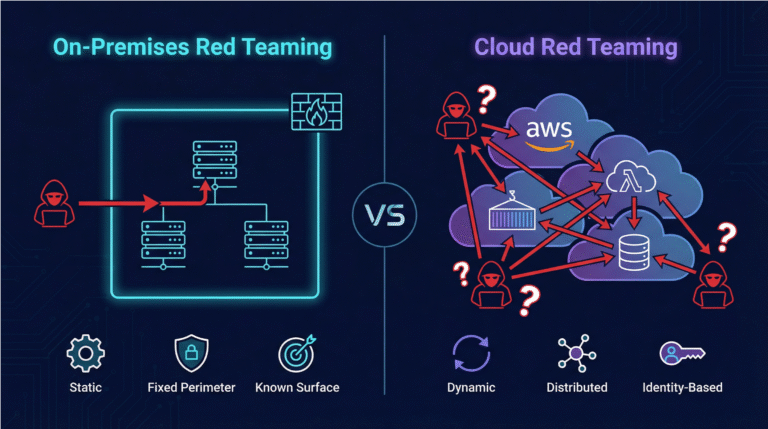
- Cloud footprints are dynamic, resources spin up and down, roles and permissions shift, and new services are constantly introduced.
- Preemptive defense with Skyhawk runs continuously, adapting to changes in real time, ensuring newly introduced assets or configurations are always under protective assessment.
Bridging Preemptive Defense and CDR
Traditional CDR (Cloud Detection & Response) tools look for suspicious activity already underway. Preemptive CDR goes further by:
- Predicting Attack Paths: Skyhawk’s Purple Team runs simulated attacks against a digital twin of your environment. This uncovers potential escalation routes before threat actors discover them.
- Prioritized Fixes: Each simulated breach scenario is tied to business impact, meaning the system prompts you to close the riskiest exposures first.
- Verified Auto-Remediation: Because the simulation verifies each alert’s validity, automated blocking is triggered without the false positives that plague reactive systems.
- Adaptive Identification of Similar Attacks: Once a verified attack path is discovered, the detection logic (CDR) automatically updates its rules to look for suspicious activity that resembles the same path. This ensures that if attackers try a similar approach in your live environment, the system flags and contains it more rapidly.
This four-step process bridges the gap between knowing you have a problem and having the confidence to fix it immediately.
Why preemptive cyber defense?
- Traditional detection and response often activate after a threat actor is well into your environment and it is too late.
- Preemptive CDR merges classic alerting with predictive intelligence, so your security stack effectively denies attackers an exploitable window.
- It fights rapid, AI-powered attacks by removing the guesswork and enabling verified automated responses. Skyhawk’s Purple Team delivers preemptive security.
- Provides feedback and recommendations to improve your other security approaches – CDR, posture issues, abandoned identities and roles and more
- Realize a comprehensive preemptive cyber defense strategy for your every changing cloud architecture
Effectively leverage Simulation Digital Twin for Preemptive Cyber Security
Another area of focus for Gartner in early disruptors is “Intelligent Simulation and Synthetic Data Transforms Cybersecurity Decision Making”. Skyhawk introduced an AI-based Simulation Digital Twin when we introduced the Purple Team in December of 2023.
Strategic Planning Assumption: By 2030, simulation data will underpin 20% of strategic business decisions, up from approximately 1% in 2024.
Why use a Simulation Digital Twin?
Traditional simulations impact production, time, and resources. Playbooks must be created and then they take hours to execute, and they most likely need to be executed during non-business hours so as not to disrupt the SOC.
Skyhawk’s Simulation Digital Twin is completely AI-based:
- Execute AI-based penetration tests with no impact on people, production, or your cloud security
- Accurately configured cloud environments, ensure accurate penetration test results attacks and accurate remediation recommendations
- Realize verified alerts and verified automated responses as mentioned Verified alerts – Threat behaviors that we know we want to stop
- Reduce burnout: Use AI to do this work constantly and consistently to alleviate the burden on your team
Interactive, Proactive, and Preemptive Cloud Security protects your cloud and protects your team from burnout
Skyhawk Security recognized that CDR needed an AI component to proactively detect threats with the first release of our Purple Team in December 2023. It can identify the anticipated issues, weaponized threats, to keep you one step ahead of threat actors. CDR capabilities were recently expanded with our Interactive CDR, an out-of-band verification, which introduces principles of Zero Trust for an immediate diagnosis of the risk level of an active event.
If you don’t know where to start with your preemptive cybersecurity strategy, try Skyhawk Security for free – sign up today!
You can read the full report at www.gartner.com.
Gartner, Emerging Tech Disruptors: Top 5 Early Disruptive Trends in Cybersecurity for 2025 by Matt Milone, Luis Castillo. Isy Bangurah, Alfredo Ramirez IV Published February 5, 2025.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.