Security teams are quickly realizing the benefits of Generative AI and are incorporating this technology into their security products for earlier detection of risks in the environment. AI can help security teams better recognize and resolve threats and exposures in their cloud environment. However, threat actors have also realized that AI offers them benefits as well. Security teams must leverage AI-based security to overcome AI-based threats. (Join the webinar: Fight AI-based Threats with AI-based Security)
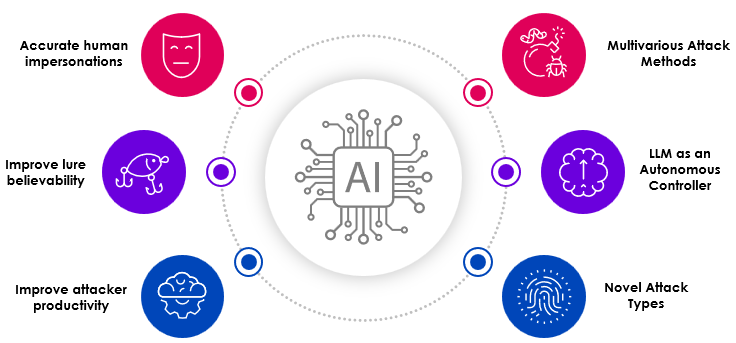
Figure 1. How are Threat Actors are Increasing Their Productivity with AI
- Improve attacker productivity: Attackers can leverage generative AI to execute more attacks, faster. AI can be used to lower the training required to write a credible lure. Generative AI also assists with automation and scale of attacks.(1)
- Improve lure believability: LLMs can process large quantities of data to identify which lures work best. (2)
- Accurate human impersonations: GenAI can create more realistic voices and video, which could undermine identity verification.(3)
- Multivarious Attack Methods: These attacks can be harder to detect than replacing polymorphism. (4)
- Using LLM as an autonomous controller to achieve a higher level of action decision.(5)
- Novel attack types: This is the scariest of things. If a threat actor can conceive of an entirely new method to attack, it would be undetectable in most cases.(6)
In our opinion, Skyhawk Security plays a role in all of them, and we will comment on three of them in this blog.
This is the first recommendation:
“Elevate requirements for more adaptive behavioral and ML defenses in your existing security controls. Currently, only 50% of enterprise endpoints have behavioral-based detection logic.” (7)
Skyhawk Synthesis Security platform can help organizations overcome threats, including AI-based threats in two keyways:
First, our machine learning models observe behaviors in the runtime to identify threats. These three levels of machine learning model sort through logs, data, and telemetry to find interesting events. There are three levels of machine learning models.
- Skyhawk Security Cloud. This is an aggregate view of risk across all our customers’ clouds, for roles and assets within the cloud. The models at this level provide a very wide view of context and help assess the overall risk of the attack sequence. To learn more about our attack sequence, check out this blog on The Science Behind our Security.
- The Customer Cloud. Several models are created to detect threatening behaviors or events within each customer cloud. For example, models that are built to detect suspicious or malicious behaviors in the network.
- Users and Cloud Assets. Finally, the Data Science team creates models for users, roles, assets, and functions to look for suspicious network traffic or API usage.
The second keyway is with Continuous Proactive Protection. We leverage AI and machine learning to update these models with Continuous Proactive Protection. This latest advancement introduces the first AI-based, autonomous purple team providing Adaptive Cloud Threat Detection and Response, continuously enhancing its protection of the customer’s cloud.
It continuously analyzes customer cloud infrastructure, proactively runs attack simulation against it and uses the results to prepare verified detections, validated automated response and remediation recommendations to ensure the cloud has the most up to date security defenses in place. This continuous protection process includes learning and automated adaptation of threat detection methods. This enables security teams to take a proactive and adaptive approach to their security strategy for the very first time.
Figure 2: Skyhawk Security Continuous Proactive Protection
It uses AI to continuously execute attacks against your cloud – an AI-based red team. An AI-based blue team continuously defends against these attacks. The results are used to update the threat detection, including the three levels of machine learning models. AI-based red and blue teams do not tire and do not stop fighting each other, to ensure your detection methods are always up to date.
A recommendation in the 2023 Gartner®, 4 Ways Generative AI Will Impact CISOs and Their Teams was as follows:
“Ensure you can measure drift in detection rate from existing controls.” (8)
Skyhawk Security updates threat detection models daily and this does two things. First, it eliminates drift from the models. Second, it ensures that threat actors cannot reverse engineer the detection methods. Threat actors, even GenAI-based threat actors, cannot outrun Skyhawk.
Another Recommendation from Gartner 4 Ways Generative AI Will Impact CISOs and Their Teams, is as follows:
“Reduce the number of ‘blind spots’ – assets, transactions, and business processes that you cannot monitor for anomalies.”(9)
Skyhawk Security’s Generative AI is constantly scanning the environment for posture, identity, and other security gaps. Our Shift Left CDR analyzes pathways to your most precious assets, and once a threat “steps” on one of those paths, we are able to send an alert, so security teams can prevent your most precious data from being accessed.
Generative AI helps security teams improve threat detection, better identify security gaps, and accelerates fixes. However, Generative AI can be used for malicious intent as well. It is important to consider cloud security tools that leverage AI to improve security and to mimic threats that are AI-based. Security teams need to leverage automation. There are too many alerts, too many threats, and too many gaps to address – there just aren’t enough people. Skyhawk Security leverages generative AI to identify gaps in your cloud security and uses automation to make updates to your threat detection.
Check out our blog to understand how Skyhawk Security can help with Novel Attack Types as well, or “Unknown Unknowns”.
Gartner: 4 Ways Generative AI Will Impact CISOs and Their Teams by Jeremy D’Hoinne, Avivah Litan, Peter Firstbrook Published June 29, 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
1 – 9 Gartner: 4 Ways Generative AI Will Impact CISO’s and Their Teams by Jeremy D’Hoinne, Avivah Litan, Peter Firstbrook Published June 29, 2023