In honor of Cybersecurity month, Skyhawk Security is offering a free 30-day subscription to the complete platform.
Why try Skyhawk Security?
Your Security and Development teams are overwhelmed with the number of CNAPP findings. There is a constant argument between security and development regarding what is a true finding vs a false one. This puts a tremendous strain on resources – there just aren’t enough to identify and address all the true findings. Additionally, some of the findings will need to remain due to architectural reasons, constraints, and legacy dependencies.
According to a Gartner® report, “Through 2026, non-patchable attack surfaces will grow from less than 10% to more than half of the enterprise’s total exposure”1. Addressing findings that can be fixed can be a long process on its own, leaving the initial penetration point exposed for threat actors. While there may be a level of inherent exposure the organization needs to accept, it doesn’t mean that the organization needs to accept the risk. There is a way to manage the risk, with prepared detection and response that is informed with the business context.
Additionally, the SOC is getting overwhelmed with alerts. Threat Detection tools like SIEMs, are lacking the cloud and application context resulting in alert fatigue as there is not an effective way to analyze and respond to these alerts. The SOC spends hours researching these alerts only to find the majority of them are benign – and all that time is lost. While these benign alerts are being investigated, real incidents do not get focus and attention, allowing threat actors to progress in their reconnaissance and lateral movement in your cloud, while your team are completely unaware.
There are concerning findings and actual threats in all of these tool sets – but how can you find the threats that matter versus the ones that don’t? How can you focus on these issues ahead of time and proactively?
How can Skyhawk help?
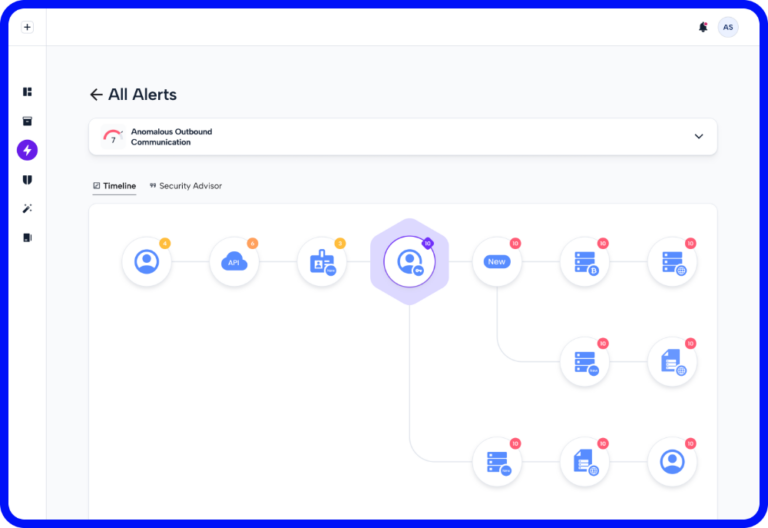
Skyhawk Security’s Cloud Threat Detection and Response (CDR) with its three layers of AI, protects the cloud against cyberattacks, even unknown unknowns, proactively. For a security platform to truly manage risk, it must be able to identify unknown unknowns, as there is no perfect posture in the cloud. And it must do so proactively so that when your SOC sees the alert, they already know it is a true positive, have the context and know how to respond, preferably with automated response at machine speed. Your working assumption must be that if a threat actor wants to get in, they will. An incident is inevitable but using the right tools you can prevent it from being a material incident or a breach. Organizations therefore must have a way to detect threats, make sure the team has context and can respond to these threats fast before an impact occurs.
Industry statistics indicates that in 70% of the cloud attacks, the attacker is logging in and not breaking in, using leaked credentials, API Keys etc. Skyhawk will recognize the malicious behaviors, even if the threat actor penetrated the cloud is using a legitimate credentials, role, or other means, and stop the threat actor before any significant damage is done, like data exfiltration, ransomware etc.
The AI-based Autonomous Purple Team proactively identifies threats and then rehearses them (continues AI based Tabletop) using a simulation twin AI-based cloud environment. This process proves to the SOC ahead of time what a malicious behavior in your specific cloud will look like. The result is a verified detection which allows you to build a verified automated response to respond to the pre-verified, true incidents in machine speed. The SOC can be confident that the automated response will work to stop the breach while not impacting production as they have seen it in action – it is completely verified!
Skyhawk’s CDR and Purple Team go beyond toxic combinations, to identify weaponized threats, and create the appropriate alert or response to stop the incident before it becomes a breach.
Does this sound too good to be true? Try the platform for free for 30 days – click here to subscribe!
1 Gartner, Predicts 2023: Enterprises Must Expand from Threat to Exposure Management, Jeremy D’Hoinne, Pete Shoard, et al.., 1 December 2022. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved