Skyhawk Synthesis Security Platform
Prevent Cloud Breaches with Accurate Threat Detection
Skyhawk Synthesis monitors behaviors in the runtime using machine learning models tailored to your cloud, to ensure the accurate detection of malicious incidents. This enables security teams to act fast to prevent incidents from becoming cloud breaches across AWS, Azure, and Gloogle Cloud.
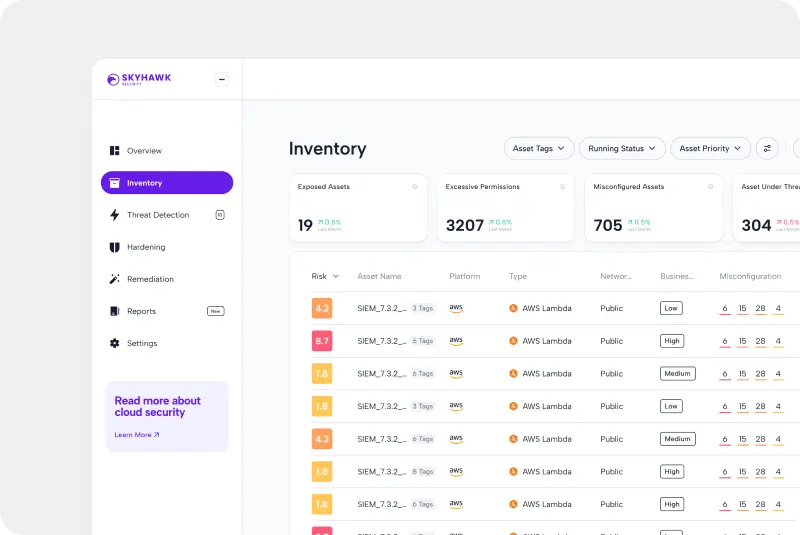
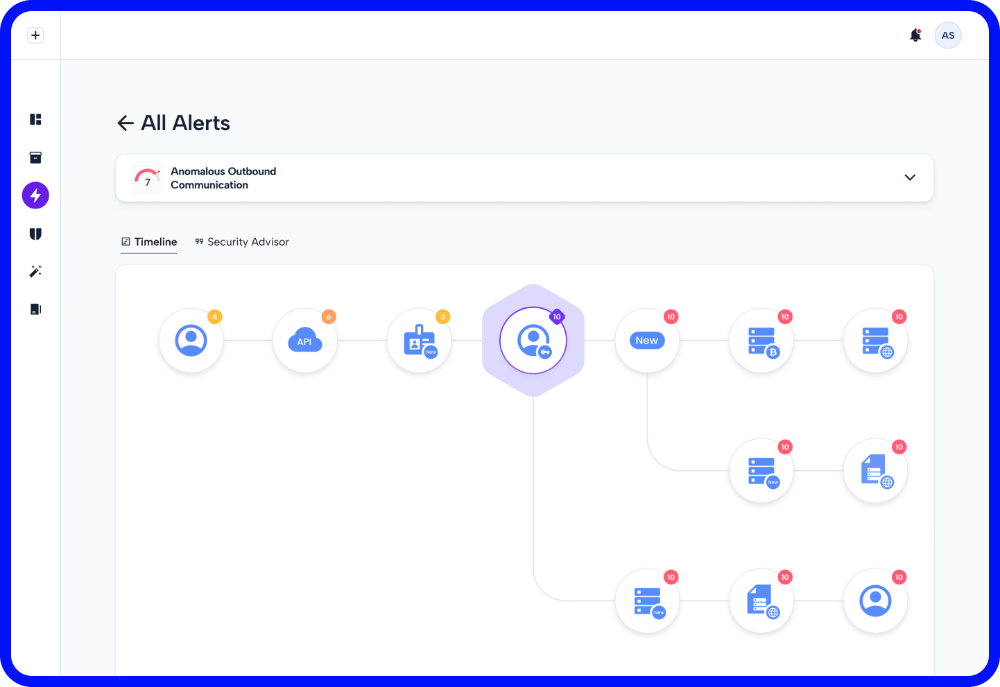
The attack sequence from Skyhawk show the series of behaviors and activities that a threat actor used to try to breach your cloud. This evidence and data is used by security teams to lock down the data and assets to prevent cloud breaches.

Understand Alert Context with the attack path

Eliminate Alert Fatigue with Verified Alerts

Skyhawk Synthesis creates custom models at three layers within your cloud environment. These models are updated daily to prevent drift and ensure accuracy. Daily updates also ensures threat actors cannot reverse engineer these models to attempt to outsmart detection. Models are created across the entire Skyhawk Security Cloud, within the customer cloud, and then for cloud users and assets.
In order to find threats that are impacting your business right now – you need to monitor theruntime. Runtime monitoring detects threats as they are unfolding, not at pre-set intervals. Other solutions review the behaviors at specific times, looking at a snapshot of the environment. Runtime monitoring from Skyhawk Synthesis finds issues in your cloud, right now – so you can stop them from
evolving to full blown breaches.
Malicious Behavior Indicators are activities that Skyhawk Synthesis has identified as risky and may pose a threat to your business based on our own AI and ML modeling of what is normal for your cloud. MBIs typically correlate multiple behaviors, activities, or events into a single more powerful data point that makes it clear if something malicious is going on in your cloud, or if this is a benign activity. MBIs are the foundational elements of the Attack Sequence.
Threat actors are typically not performing really visible, explosive events that make it very obvious that a breach is in process. Slow, under the radar events are used to compromise your organization’s cloud. Remove the time of hours or days as this is not always the case. Remove the time of hours or days as this is not always the case. Skyhawk Synthesis sequences MBIs and then assesses the risk of the sequence. Once the risk of the sequence reaches a threshold, an alert is propagated to the security team. An alert from Skyhawk is not to be ignored – this indicates there is an actual threat to your cloud.
Continuous Proactive Protection from Skyhawk delivers digital twins continuously monitoring and protecting your cloud environment to find security threats and then fixes them. As your cloud changes, so do your security needs. This adaptive CDR delivers detection tuned to each customer’s cloud by updating the detection models and creating new MBIs for your cloud. It is your autonomous, AI-based purple team.
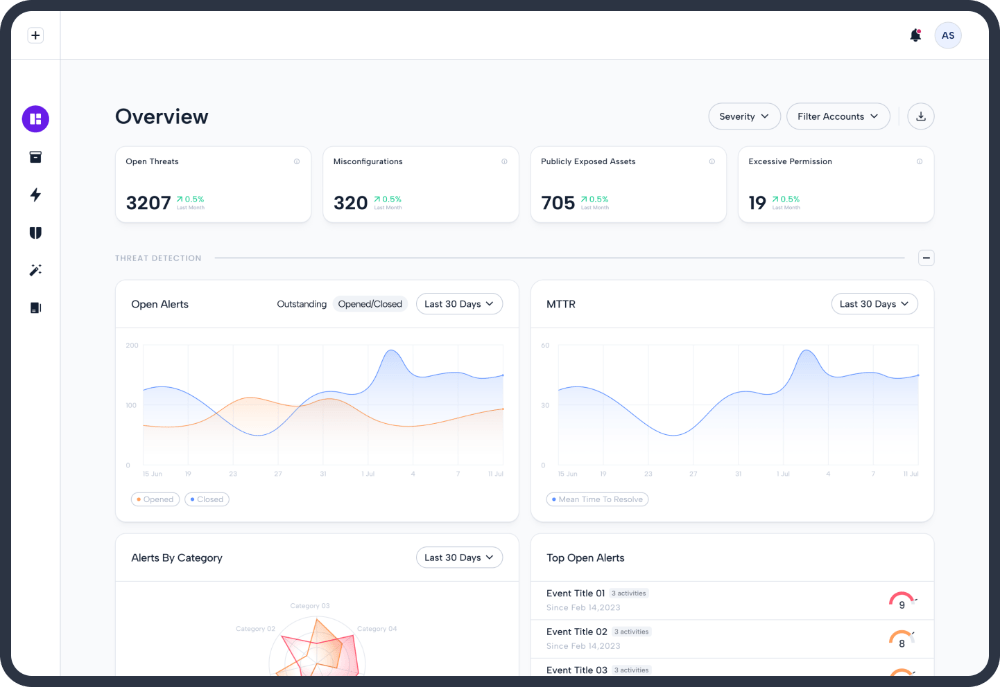
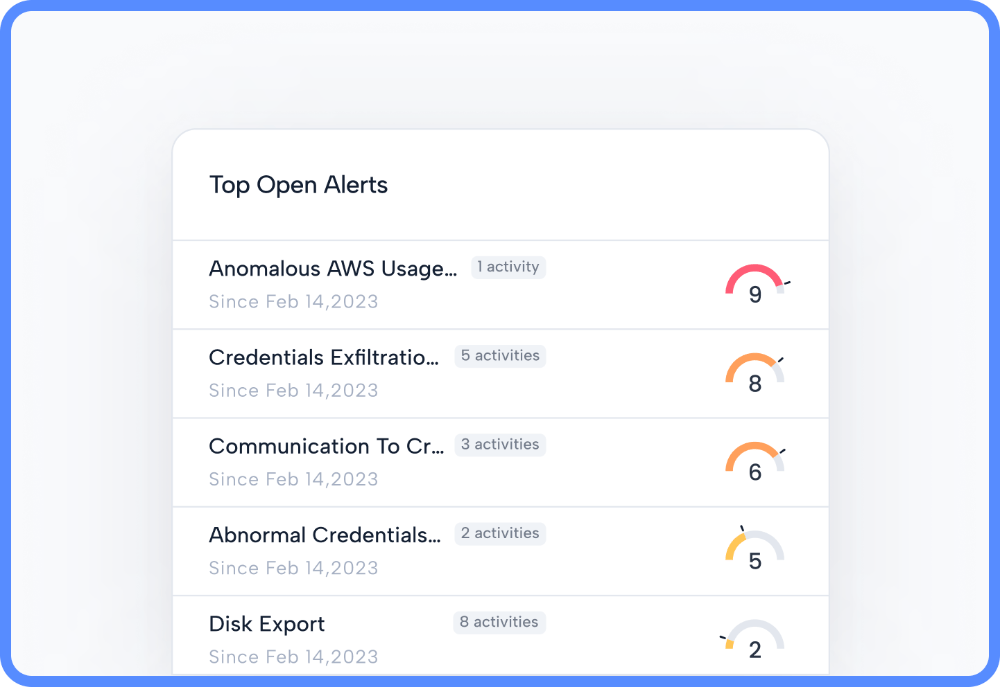
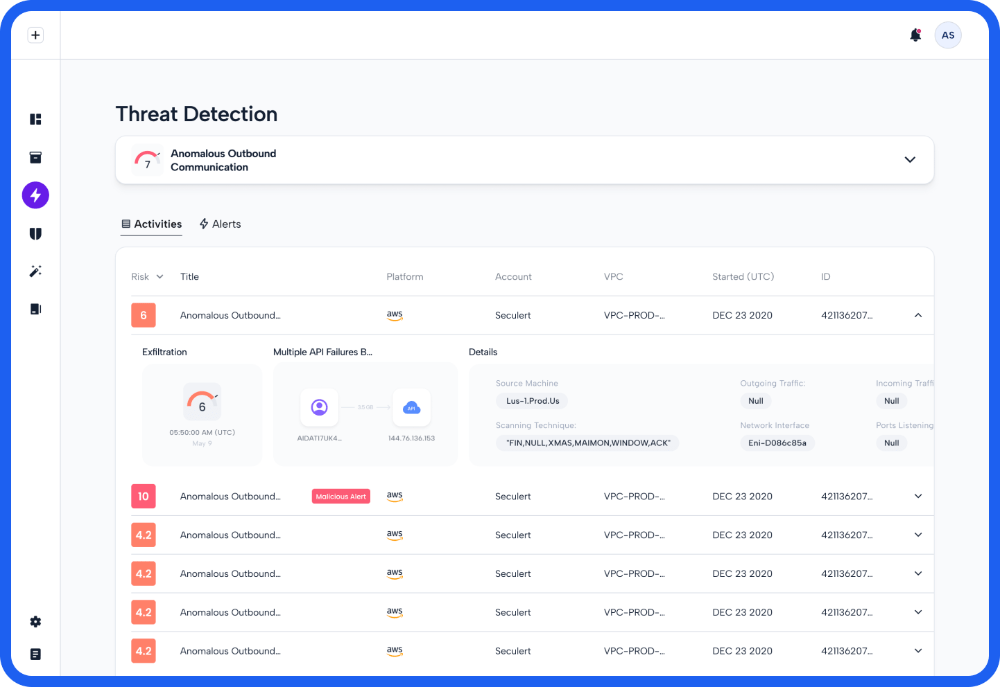
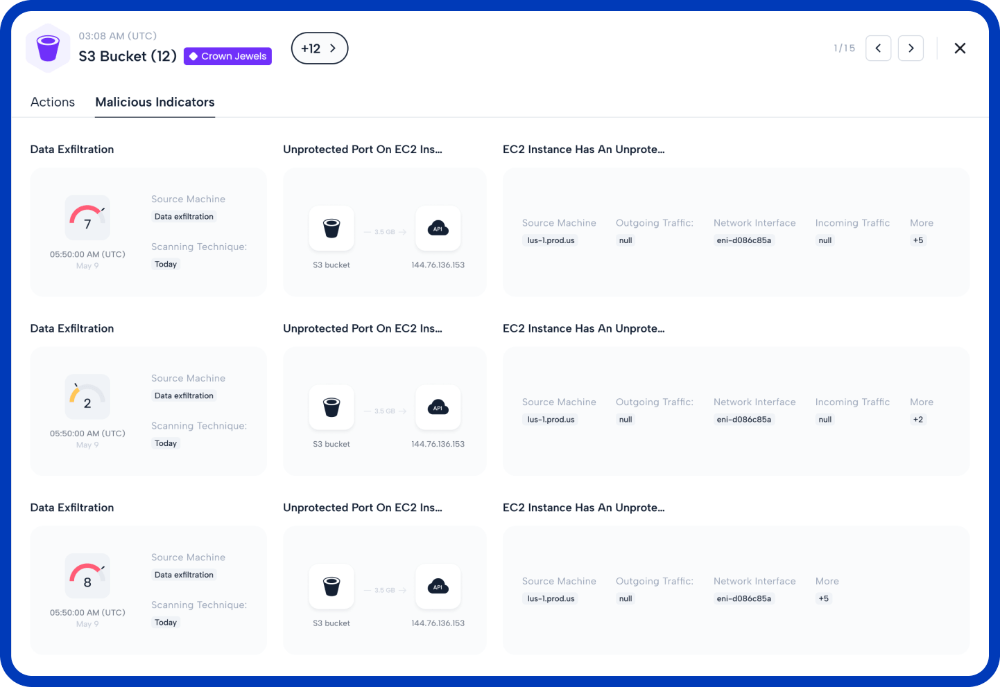
Platform contextualizes and correlates all of your specific attack vectors in real-time. This eliminates alert fatigue and ensures security teams are only focused on actual security threats. It provides scored and verified alerts and insights on what you can do to stop them to prevent cloud breaches across AWS, Azure, and Gloogle Cloud.