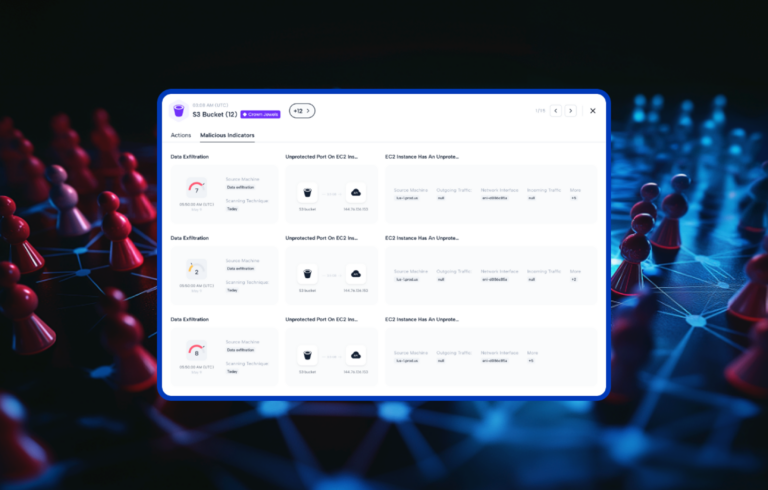
Skyhawk Security recently announced at RSA 2025 an expansion of our AI-Powered Purple Team to secure cloud applications and how they interact with the cloud infrastructure they are hosted on. This new capability identifies weaponized risks in cloud applications, the way these interact with the cloud infrastructure, the blast radius (reachability analysis), potential impact on crown jewels to prioritize risks based on business impact and continuously monitors threats across applications and infrastructure, without agents.
It protects against today’s biggest cloud security issue, one exploited in recent attacks including the MOVEit Transfer breach, the XZ Utils backdoor, a Google Cloud metadata exposure via a web application flaw and Log4j and Log4Shell—thus closing the gap between application security and cloud infrastructure monitoring preemptively, before the attack even starts. These attacks caused massive disruptions and shared a common approach—initially compromising all layers of modern cloud applications, application workload and cloud layers.
In our opinion, this is a very timely announcement as Gartner recently included Skyhawk Security in research that covered this important trend. Key findings included are:
- “Cloud-native security and application security posture management (ASPM) are the future of modern application protection. Startups that embrace these transformative solutions with highly differentiated approaches are likely to attract the most attention from investors and secure a competitive edge.”
- “Well-funded cloud-native security startups are concentrating mainly on runtime security, automated remediation, and cloud incident response.”
Skyhawk Security Continuous Autonomous Purple Team – Preemptive Cloud and Application Security
Skyhawk’s platform proactively identifies weaponized risk in your cloud, across all layers of cloud applications (application, host, and cloud level) and their interactions. The risks are prioritized based on the business value (In CTEM terms, Scoping and Discovery) of the asset impacted by that weaponized risk. The coverage of application vulnerabilities, infrastructure vulnerabilities, misconfigurations and sensitive data discovery are at the core of the data feeds going into the platforms. This in-depth analysis allows customers to:
- Preemptively ensure accurate risk prioritization aligns with business priorities.
- Automated creation of cloud security controls
- Drive operational efficiency by improving the ROI of other AWS Security investments while reducing TCO as the Skyhawk Security platform analyzes the data from these other tools (CNAPPs, Vulnerability scanners, data discovery scanners etc.) and provides the conclusions, recommendations, and remediations
Skyhawk’s Purple Team – a unique approach according to Gartner:
“Other unique approaches, such as intelligent simulation through the use of AI assistants to assess security threats and security posture, offer proactive cloud security.”
Skyhawk’s unique approach is a true innovation solving the new risks customers are facing with the rise of AI based attacks.
“Generative AI-driven threats are challenging current cybersecurity strategies, rendering traditional reactive approaches obsolete. Product leaders must adopt preemptive solutions to stay ahead or risk being outpaced in the escalating battle against sophisticated attacks.”[1]
In that context, it is important to note that while eBPF platforms add host/application-level observability, they are still reactive threat detection approaches.
The results and benefits of the Skyhawk’s Platform:
- Addresses the Progressive Technology-based Adversarial-Driven Risk
- Bridging the gap between SOC and application teams before an attack happens
- Reducing MTTR to seconds by enabling trust in the detection and response.
- Resolving the two main inhibitors to automated response, trust in the alerts and in the response to make no damage
- Preemptive security being the core which enables the trust required to reduce MTTD and MTTR to seconds
- Preemptively identifying weaponized risks and prioritizing the hundreds of thousands of findings to a manageable list of true exploitable risks by reachability analysis.
- Understand true risk and reachability of vulnerabilities from the application to the cloud layers to empower the SOC to secure your business
- Preemptive defense with Skyhawk runs continuously, adapting to changes in real time, ensuring newly introduced cloud assets or configurations are always under protective assessment
- Find threats in real-time to stop cloud breaches
We believe, the key benefits align very well to these Gartner insights:
“Early stage startups are focusing on cloud runtime security with detection and response capabilities. They emphasize integration with SecOps for proactive threat management by automating processes and using advanced tools for continuous monitoring, real-time analytics, anomaly detection, and automated incident response.”
“AI and automation are key to improving security efficiency and addressing resource shortages. Product leaders should invest in AI-driven tools to automate routine tasks, ensuring human oversight and validation metrics.”
Summary
Skyhawk Security Platform is an agentless Cloud and Application Threat Detection and Response (CADR, CDR) that revolutionizes cloud security with preemptive, interactive, and application threat detection and response in one platform. It contextualizes the detections with the business value of the cloud assets, so security teams prioritize the most consequential alerts based on risk to their business with an agentless cloud security platform.
Skyhawk’s threat detection and response sorts and correlates through thousands of events to detect malicious activities in real-time to prevent cloud breaches, eliminating alert fatigue by reducing tens of thousands of events to dozens of alerts. The platform’s purple team simulates attacks against a Digital Twin of the cloud environment, from the application to the cloud infrastructure it is interacting with, uncovering weaponized threats and attack paths a threat actor will exploit. These threats are then prioritized by the business value of the at-risk asset. This prepares the cloud defenses and security teams, so when there is an event, they can act fast. Skyhawk Security enables security teams to take a proactive approach to cloud security for the very first time.
Skyhawk Security prepares cloud security teams in a comprehensive way so they can achieve their goal – to prevent cloud breaches, saving the company’s brand and reputation, while protecting employees and customers.
If you don’t know where to start with your preemptive cybersecurity strategy, try Skyhawk Security for free – sign up today!
Gartner subscribers can read the full report at www.gartner.com.
Gartner, Emerging Tech: Techscape for Startups in Cloud and Application Security by Mark Wah, Charanpal Bhogal, Shailendra Upadhyay, Mark Driver Published April 4, 2025
[1] Gartner, Emerging Tech: Build Preemptive Security Solutions to Improve Threat Detection (Part 2) by Luis Castillo Published April 2, 2025
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.