Cloud security teams are evolving their security approach, going beyond alerts and looking at the threat exposure with a business context. This enables the cloud security team to prioritize security gaps based on the value of the asset behind it. It also makes it easier for the CISO to clearly communicate what the threat exposure means to the business.
Here are the top 10 questions on CTEM:
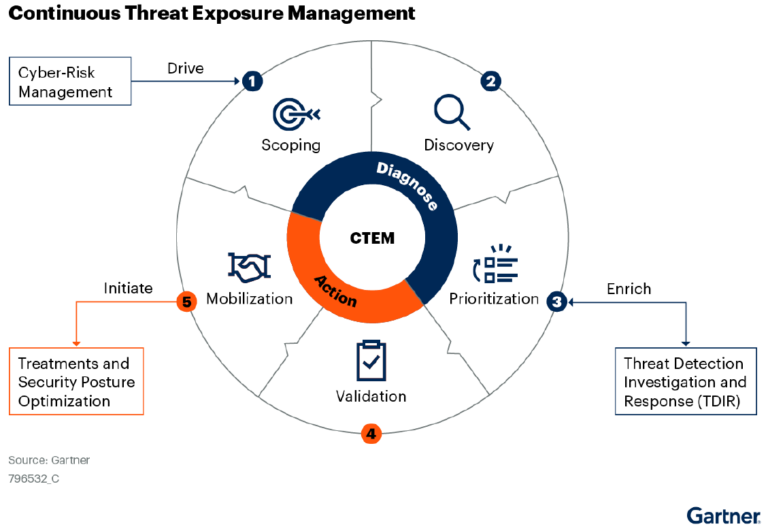
1. What is Continuous Threat Exposure Management (CTEM)?
- It is a programmatic approach to managing exposure. There are two aspects to this – the framework itself, and how it is applied to the environment.
- The first step is to define the attack surface. This should go beyond misconfiguration and vulnerabilities. It should be comprehensive and show all the points of entry. The organization needs to look at cloud, SaaS, social channels, all internal and external points of engagement to data and applications.
- Second, the process of discovering assets and their risk profiles. Priority should be given to discovery in areas of the business that have been identified by the scoping process, although this is not always the driver. This is accomplished through frameworks and discussion, not necessarily with a product.
- Prioritizing the treatment of exposures must be based on the urgency, severity, availability of compensating controls, risk appetite and level of risk posed to the organization.
- Validation is the part of the process by which an organization can validate how potential attackers can exploit an identified exposure and how monitoring and control systems might react.
- Cross-team mobilization shifts expected outcomes from tactical and technical responses to cybersecurity optimizations.
- This entire approach is executed, continuously, to ensure that as the architecture, threats, and business priority of business assets changes, the threat exposure is updated and accurate
2. How does CTEM differ from traditional vulnerability management?
Vulnerability management looks exclusively at the security architecture from a security perspective. CTEM provides the business perspective, it looks at the business value of the asset that is behind the exposure. This is then used to prioritize the exposure, what should be fixed first based on how easy it is to use the exposure to access the business asset.
3. What are the core components of a CTEM program?
- There are three main aspects.
- First, the framework itself and the first step is to identify where your business assets are and the criticality of those assets. This helps organizations determine which exposures matter the most. This will entail tiger teams and discussions more than actual products. Also, what internal and external requirements need to be followed. Is your organization required to be compliant with HIPPA, SEC Cybersecurity Rules, or other regulations? This should be part of the threat exposure as well as being out of compliance can cause financial penalties.
- Second, the five steps outlined above look at the attack surface, and then how easily a threat actor can get to the valuable business assets. Similar to a purple team, it will execute an attack and then see how the security that is in place responds. This will surface the weakest points in the overall cloud security, and the business value of the asset provides the context for the security team to know what should be fixed first.
- Third, is the continuous nature of the program. This is especially important for cloud. Organizations leverage the cloud because it is flexible, agile, and easy to spin up and spin down resources and this type of environment is not easy to secure. CTEM is ideally suited to securing clouds.
4. How can CTEM improve my organization’s security posture?
According to Gartner, by 2026, more than 50% of all attack surfaces will not be patchable. There could be several reasons for this including that patching the cloud services makes it not usable for certain segments of the organization. If security teams cannot “lock down” the cloud and services, they need to have another way to manage the threat exposure, this is why a programmatic approach, like CTEM, is needed.
5. What technologies and tools are used in CTEM?
There are several tools and platforms that could be used to be part of a CTEM strategy and they all have strengths and weaknesses. It is important to look at several different technologies to ensure the breadth of your security needs are covered. Here are a few for consideration:
| Technology | Strength | Weakness |
| CSPM | Helps to secure the environment’s perimeter to prevent threat actors from penetrating the cloud. | Not all suggested updates can be executed as they can slow down cloud productivity and once the threat actor is within the perimeter, CSPM will not be helpful. |
| CIEM | Similar to CSPM, it focuses on permissions, which in a cloud is critical to access cloud services, it helps secure the perimeter and access to the cloud. | Over-restriction can lead to a downturn in team productivity as they do not have access to the resources they need to do their jobs |
| XDR | Evaluates behaviors within the environment and correlates them to identify actual attacks to get a comprehensive view of threats | Not all threat detection is built the same; be sure to evaluate one that build machine learning models for detection custom to your cloud, on-prem environment, etc. |
| CDR | Cloud Threat Detection and Response, similar to XDR, correlates logs and telemetry from across the cloud to identify malicious events. These are correlated into an attack sequence to identify verified threats and alerts. | Cloud-native solutions are built only for clouds. Separate solutions will need to be used for on-prem, and other clouds, etc. Most cloud-native solutions require several security services to deliver comprehensive CDR. |
| SIEM | Can be used to process large amounts of logs so you can get a broad view of issues across the environment | Updates to the environment can break the detection rules; this can be very resource intensive |
| CNAPP | Visibility into cloud-native environments, including real-time monitoring of workloads, network traffic, and user activities. | Complexity and cost for management and maintenance; can require too many resources |
| Proactive Protection | An AI-based autonomous team that surfaces weaknesses in the attack surface and then prioritizes those issues based on the business asset behind the weakness | Many organizations claim to be proactive, but are not; be sure to clearly understand what Is meant by “proactive” |
6. How is CTEM implemented in an organization?
- The first step is to set up three tiger teams to guide the implementation.
- The first will help identify the data assets across the entire organization. This team will also classify the data and then determine what the business response should be to a breach of the data based on the classification. It should include what risks the team is willing to accept.
- The second Tiger Team will evaluate the relevant technologies to achieve their goals. This team should leverage the requirements of the first data classification tiger team to identify the best platforms, tools, and processes to be used to support their goals of reducing business risk. Additionally, this team should fully describe the risk that could be accepted as well and how the technologies will play a role. There should be a framework for measuring the overall threat exposure based on the data assessment from the first tiger team and the technologies used so that this can be measured and reported to senior management.
- The third tiger team will implement. This should ideally be the SOC. This team should also review the framework for ongoing measurement to ensure they can support it. If this tiger team will not be responsible for the ongoing management and maintenance of the program, the three tiger teams should determine who will be responsible and develop a transition plan.
7. What are the benefits of adopting CTEM?
- Continuous: The continuous aspect of CTEM is different from other approaches, and this aligns particularly well with CTEM for cloud. Cloud architectures are changing rapidly and often to meet changing business needs and requirements. This is why organizations move to the cloud. However, organizations that invest in cloud, need a security framework that takes into account the frequency of this change.
- Feedback: It is not enough to just continuously evaluate the cloud security and cloud architecture – the feedback needs to be implemented and used to update the cloud security. What vulnerabilities need to be addressed, what posture issues, permissions, and more to update the cloud security. This continuous evaluation of cloud architecture to improve cloud security reduces the overall threat exposure of the cloud, reducing the exposure of the business.
- Information driven alerts: Threat actors are generally aware of deficiencies in patch management and lack of prioritization. In other words, if they know medium –severity vulnerabilities rarely get addressed, it presents a path of potentially least resistance. This is not the case for Skyhawk. It does not just look at the alert and simplicity or sophistication of the alert. It looks at the alert and the value of the business asset behind it. The context enables security teams to prioritize alerts and prevent cloud breaches.
8. How does CTEM help in managing compliance requirements?
As managing threat exposure is the core tenant of CTEM, compliance will be part of the scoping process in terms of the threat exposure. What is the risk if you are not meeting a compliance requirement? Non-compliance is an exposure as this can lead to financial penalties and other business risks. Including compliance requirements as part of the overall scoping ensures internal and external compliance requirements, minimizing fees and exposure.
9. Can CTEM be integrated with existing security frameworks?
Yes. CTEM is aligned very well with security frameworks and can help augment security approaches and expand the conversation to threat exposure from a business perspective. For example, integration with MITRE helps determine if an organization is being targeted by a specific group, or a set of TTPs is being leveraged.
10. What challenges might organizations face when implementing CTEM?
There are two categories of challenges:
- The business level challenges could slow or delay the implementation of CTEM. The first is the data classification. Agreement on what is the most valuable and critical data to the business could be challenging. The acceptable level of risk could also delay implementation.
- The technical challenges are also two-fold and involve finding the right technology and the right people. It is especially difficult to hire security professionals.