This blog is authored by Amir Shachar, Chief Data Scientist at Skyhawk Security.
If you are reading this blog, you are probably wondering how to detect unknown unknowns in the realm of cybersecurity. The very nature of these unknown threats makes them difficult to detect using conventional security measures. However, by leveraging a platform that harnesses the power of machine learning to decipher behavioral intent, we can uncover these elusive threats. In this blog, we will explore the concept of unknown unknowns in cybersecurity, discuss the importance of identifying behavioral intent, and introduce the Skyhawk Synthesis Security Platform—a cutting-edge solution that employs multiple layers of machine learning to detect both known and unknown attack patterns.
What is an unknown unknown?
To grasp the concept of unknown unknowns, we must first define them. In the context of security, unknown unknowns refer to attack patterns that are unfamiliar to security researchers while it used in the wild (also referred to as zero-day attacks). They are activities that are not yet considered to be suspicious or malicious. Many existing tools focus on known attack patterns, but what about those that are yet to be discovered? This is where the concept of unknown unknowns becomes crucial.
Skyhawk Synthesis Detects the Unknown Unknowns
The Skyhawk Synthesis Security Platform stands out by utilizing three layers of machine learning to identify threats, ensuring that no threat actors can infiltrate your cloud infrastructure undetected or misuse your valuable assets. Let’s explore these layers in detail:
1. Malicious Behavior Indicators (MBIs):
MBIs are activities that Skyhawk has identified as suspicious behaviors. This is done by tailored behavioral modeling of each object and environment detecting deviation from the normal behavioral in relation to the object and the object groups. The art underneath is which behaviors are monitored and the richness of the model parameters.
2. Attack Sequence Assembly:
Leveraging AI and machine learning, the platform correlates MBIs to form an event sequence, providing a comprehensive view of the incidents. This analysis allows the security team to understand the context and easily perform the initial incident triage in order to resolve the alert efficiently. The platform utilizes advanced machine learning models to accurately identify the intent behind the observed sequence of events. It is also determining severity of the incident factoring in additional context such as the potential business impact and access to sensitive data enabling a comprehensive assessment of the threat’s severity.
3. Early Detection with ChatGPT:
Integration with large language models such as ChatGPT enhances Skyhawk Security’s capability to identify malicious actors 78% faster. ChatGPT acts as 1000 Virtual Incident Responders (VIR), evaluating the attack sequence and increasing confidence in determining malicious intent earlier in the sequence.
The result of these three layers of machine learning and AI working together is the ability to detect unknown attack patterns without the need for a closed set of predefined polices.
Unknown unknown is something like a connection or steps that the attacker takes that do not seem like an attack; we didn’t see enough activities for it to seem suspicious or malicious; we want to be able to detect the malicious behavior before it happens – that is why it is called an unknown unknown; find connections in the data that are not straightforward for the experts, but AI expert (not a human) or machine can detect it
How does that differ from other detection tools using AI?
Most AI-based tools focus solely on the first layer, detecting MBIs. However, without considering context and the past sequence of events, these tools often generate an overwhelming number of alerts due to frequent anomalies in cloud environments. This flood of alerts burdens security teams and delays effective response, making them primarily useful for forensics after weeks of malicious activity.
The more sophisticated tools rely on predefined sets of combinations deemed indicative of malicious intent. Consequently, they suffer from a limited scope, detecting only a predefined and narrow range of attack patterns.
In contrast, Skyhawk Synthesis goes beyond these limitations by analyzing attack sequences and detecting a broad spectrum of attack patterns, without relying on a closed set of predefined policies.
Example of Unknown Unknowns
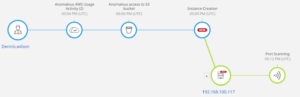
In this image, we see an example of an unknown unknown. Machine learning models look for behaviors and correlate those behaviors. If the alignment of those behaviors shows malicious intent in the cloud, then it is determined to be a threat. Skyhawk Synthesis does not look for specific patterns to identify threats, it aligns many actions and behaviors to find the threats. The first layer of AI is indicated at the atomic indicator, and the second layer combines the activities into a comprehensive attack story. With visibility into the entire story, we are able to assess the intent and alert on the sequence to prevent the breach.
Summary
In the ever-evolving landscape of cybersecurity, detecting unknown threats is a paramount challenge. By leveraging the power of multiple AI layers, such as behavioral modeling, attack sequence analysis, intent determination, and early detection through ChatGPT integration, the Skyhawk Synthesis Security Platform offers a comprehensive solution. With the ability to detect both known and unknown attack patterns, it empowers organizations to stay one step ahead of threat actors and safeguard their valuable assets.