Skyhawk Security is proud to announce the expansion of its cloud threat detection and response capabilities with Interactive CDR. This new capability expands the team that can verify if an activity is malicious or not, by going to the alleged source of the activity, incorporating principles of Zero Trust. This crowdsourcing of threat verification reduces the burden on the SOC and accelerates the time to response.
The SOC is overwhelmed with alerts. The team is inundated with events, with no context, so they have to treat all of the events the same – as a threat. Data indicates that 70% of cloud breaches start with compromised credentials, API Keys etc., so even if an authenticated identity is involved, the SOC still has to investigate to ensure the activity is an actual business activity. This greatly increases the burden on the SOC as even the activities that look legitimate require questioning and review. This is the problem that Interactive CDR will solve – fast, real-time verification of anomalous suspicious activity directly from the asset owner.
Skyhawk Security Cloud Threat Detection and Response continuously monitors cloud asset behavior, including users, roles, machines, and more. If a behavior deviates from the norm, the new Interactive CDR automatically sends a notification to the user who owns the asset or identity, asking them to authorize and validate the activities that triggered the alert. This aligns with Zero Trust and the core concept of CDR’s detection flow, which happens regardless of the user’s role or location, even inside the network, eliminating the assumption that users inside the cloud perimeter are trustworthy.
The SOC is able to share some of the burden of alert verification. This team is already understaffed, this new capability is one small way to alleviate the burden on this team.
How does this work?
Through a mobile app, we are able to ensure accuracy of the threat and reduce the burden on the SOC, fast, by bringing the asset owner into the threat verification process quickly and easily.
First, a malicious activity is detected. Then, Skyhawk categorizes the activity and determines if the activity being executed is a user or cloud asset. If it is an asset, we identify the owner of the asset. There are then two possibilities forward depending on if the activity is verified by the user or is being executed by a threat actor.
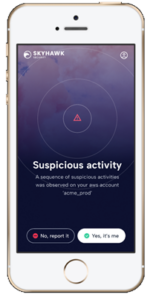 If they are aware of this activity, and they are responsible for the activity, then the user simply indicates that they are executing this activity. The platform still monitors the activity, just in case there is a future malicious insider activity. The risk score is of the activity is reduced with the verification from the owner and it is flagged as user verified.
If they are aware of this activity, and they are responsible for the activity, then the user simply indicates that they are executing this activity. The platform still monitors the activity, just in case there is a future malicious insider activity. The risk score is of the activity is reduced with the verification from the owner and it is flagged as user verified.
 If it turns out they are not aware of this activity, and it is in fact malicious, this means their credentials are most likely compromised. The SOC team is then alerted to the fact that there is an unverified activity in the cloud, it is suspicious and needs to be addressed now. The SOC is able to act fast and they know they are not wasting their time as the owner has said, I am not doing this.
With Interactive CDR, your organization will realize:
If it turns out they are not aware of this activity, and it is in fact malicious, this means their credentials are most likely compromised. The SOC team is then alerted to the fact that there is an unverified activity in the cloud, it is suspicious and needs to be addressed now. The SOC is able to act fast and they know they are not wasting their time as the owner has said, I am not doing this.
With Interactive CDR, your organization will realize:
 If they are aware of this activity, and they are responsible for the activity, then the user simply indicates that they are executing this activity. The platform still monitors the activity, just in case there is a future malicious insider activity. The risk score is of the activity is reduced with the verification from the owner and it is flagged as user verified.
If they are aware of this activity, and they are responsible for the activity, then the user simply indicates that they are executing this activity. The platform still monitors the activity, just in case there is a future malicious insider activity. The risk score is of the activity is reduced with the verification from the owner and it is flagged as user verified.
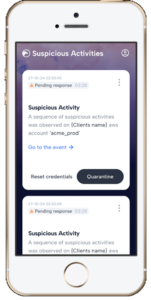 If it turns out they are not aware of this activity, and it is in fact malicious, this means their credentials are most likely compromised. The SOC team is then alerted to the fact that there is an unverified activity in the cloud, it is suspicious and needs to be addressed now. The SOC is able to act fast and they know they are not wasting their time as the owner has said, I am not doing this.
With Interactive CDR, your organization will realize:
If it turns out they are not aware of this activity, and it is in fact malicious, this means their credentials are most likely compromised. The SOC team is then alerted to the fact that there is an unverified activity in the cloud, it is suspicious and needs to be addressed now. The SOC is able to act fast and they know they are not wasting their time as the owner has said, I am not doing this.
With Interactive CDR, your organization will realize:
- Faster MTTR: Faster incident resolution through enhanced user engagement to secure accounts and a stronger, more efficient defense against cloud data breaches
- Interactive Protection: Real-time distributed detection and verification of activities verified with the source or owner, reducing the window of opportunity for attackers to exploit compromised credentials or vulnerabilities
- Minimized Disruption: Legitimate actions are quickly cleared, avoiding unnecessary investigations, allowing the SOC to focus on real suspicious activities to immediately address
- Improved Security Efficiency: Security teams can focus on actual threats, as context aware false positives are resolved quickly through user verification, reducing manual investigation efforts
- Added on top of Skyhawk’s Proactive CDR: Proactive CDR helps pre-verify scenarios that are agreed to be malicious and their response. The new capability adds another protection mechanism on top