This blog was written by Asaf Shahar, VP, Products at Skyhawk Security
The UK Information Commissioner’s Office (ICO) recently fined Liverpool-based law firm DDP Law £60,000 following a ransomware attack that exposed highly sensitive criminal case data. The investigation revealed critical security gaps: the absence of firewalls, lack of multi-factor authentication, unpatched systems, and most notably, the compromise of a user account that had been inactive for several years.
This case is a textbook example of why modern threat detection and response solutions — like Skyhawk Security — are essential in today’s cloud-first landscape.
Early Detection Through Anomalous Behavior
Ransomware attacks, even when well-orchestrated, often create early-stage signals. Attackers typically generate noise in the form of anomalous login behavior, abnormal access times, and a pattern of failed or unauthorized API calls.
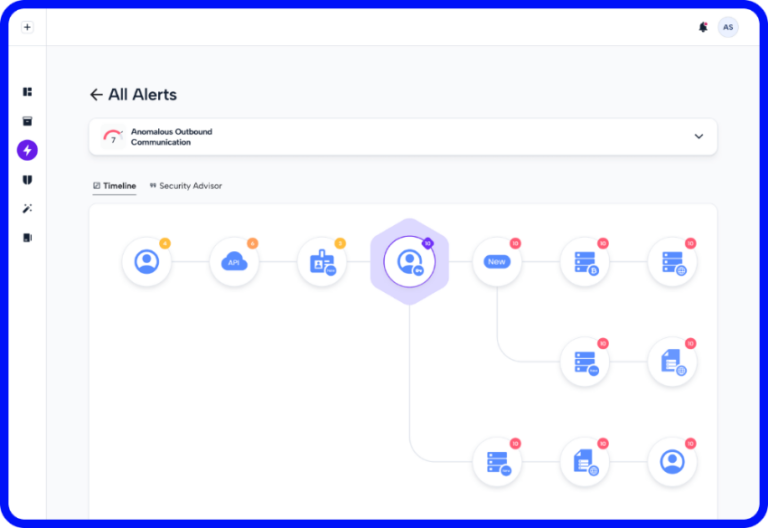
Skyhawk’s Cloud Detection and Response (CDR) platform continuously monitors and correlates user, asset, and network activity across cloud environments. In this case, an attacker using dormant credentials to suddenly access sensitive systems or initiate lateral movement would have triggered multiple low-severity Malicious Behavior Indicators (MBIs). These would have been automatically correlated into a single high-confidence incident — allowing detection long before ransomware was deployed.
Real-Time User Verification with Interactive CDR
Skyhawk’s Interactive CDR would have sent real-time verification prompts to the employee associated with the suspicious activity. If the credentials were stolen and the activity wasn’t legitimate, the user would either deny the activity or fail to respond — enabling immediate response actions like session termination or account quarantine.
This drastically reduces the time between detection and response while providing concrete evidence of compromise, especially critical in attacks involving credential theft.
Attack Simulation and Blast Radius Analysis
Skyhawk also offers a powerful “what-if” analysis capability. By simulating credential theft, the system evaluates what an attacker could do if they compromised a specific identity. This blast radius analysis includes:
- Mapping potential lateral movement paths
- Evaluating reachable data stores, applications, or sensitive workloads
- Highlighting over-permissive or high-impact accounts
In DDP Law’s case, the compromised user account had been inactive for years — a red flag on its own. Skyhawk would have surfaced this account as a high-risk identity during continuous breach path analysis. Even before any attack occurred, the platform would have alerted on the dangerous combination of:
- A dormant user with elevated or unmonitored permissions
- A lack of activity over time with no deprovisioning
- High potential blast radius if compromised
The risk could have been mitigated proactively — by removing unnecessary access or deactivating the account entirely.
Contextual Risk Prioritization and Remediation
Skyhawk doesn’t just flag misconfigurations — it ties them to exploitable attack paths. For example, if cloud storage or case record systems were exposed via permissive network settings or poorly scoped IAM policies, Skyhawk would have prioritized them based on their exposure to known attack vectors.
This shifts security from reactive alerting to proactive risk reduction.
Reducing Noise, Accelerating Response
Skyhawk streamlines the threat detection process by correlating behaviors over time and across multiple entities. Security teams aren’t left chasing low-level alerts — they receive rich, contextual incidents that highlight:
- The method of entry
- The path of escalation
- The affected assets and identities
This enables faster triage and effective containment.
Conclusion: Moving From Reactive to Proactive Security
The DDP Law breach highlights the cost of neglecting modern cloud security practices. An inactive user account should never be an entry point for ransomware. With Skyhawk Security’s cloud-native detection, verification, and simulation capabilities, this breach could have been detected early — or even prevented entirely.
Skyhawk’s platform delivers:
- Early detection of suspicious activity
- Real-time user verification workflows
- Continuous breach simulations and blast radius analysis
- Actionable insights into identity risks and misconfigurations
Security is no longer about chasing alerts — it’s about understanding the context and acting before damage occurs.
If you don’t know where to start with your preemptive cybersecurity strategy, try Skyhawk Security for free – sign up today!