The reason why cloud threat detection is so difficult is for one reason – it requires expertise to make sense of vast amounts of disjointed data and alerts. There is too much data and alerts to sort though, aggregate, correlate, and determine if what is happening is a threat, a one-off, a mistake in employee permissions, or even an actual breach in progress. Analyzing data requires understanding of the context, for cloud threat detection this adds another layer of complexity since the cloud context is continuously evolving, some of which is ephemeral. For successful cloud threat detection, security analysts must use contextual information to be successful which is impossible to do without the right purpose-built tools and services. Contextualizing, cleaning benign data, aggregating, correlating and generating security insights in near real-time and cost-effective manner is a very challenging problem to solve. So, what do other tools do? They overwhelm you with too many alerts – and most of them by themselves do not look like an issue. There is an alert for every activity in the cloud that on its own might be anomalous behavior that has no risk associated with it. When there is an alert for every activity, teams become desensitized to the alert onslaught, and threat actors achieve their goal with the help of your security tools.
Skyhawk Synthesis takes tens of thousands of raw data points over the course of minutes and hours, and determines the relationship of these data points, and then identifies which are actual threats to your crown jewels, and which are just one-off behaviors. Skyhawk alerts matter – they are validated alerts.
So, how do we do this?
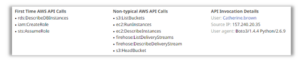
Let’s start with some events. Take a look these anomalous cloud events:
We see that for the user Catherine.brown, there are first time cloud API calls and non-typical cloud API calls. In another security tool, these activities would cause several alerts and your security team would need to figure out the relationship between these activities and events.
With Skyhawk, you don’t have to, we aggregate this data and determine all the relationships and dependencies to see if this is something of interest in terms of your security. In addition, since Skyhawk correlates, we may be able to alert on an anomalous combination of calls, even though each call on its own might not be anomalous.
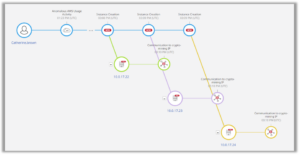
As a result, we are able to determine that all of these events align to a single malicious behavior indicator (MBI) which shows there is anomalous Cloud API Usage Activity. This tells the team there is something going on in cloud infrastructure they need to pay attention to. Skyhawk Synthesis then continues to sort through the data and then correlate events, into MBIs. MBIs are then correlated into the attack sequence.
Behind each of these MBIs, there are 10 or more events, that are then correlated into an attack sequence, providing all the evidence to the security team so they understand how the threat actor got in, how they are moving through the environment, and what they were able to compromise.
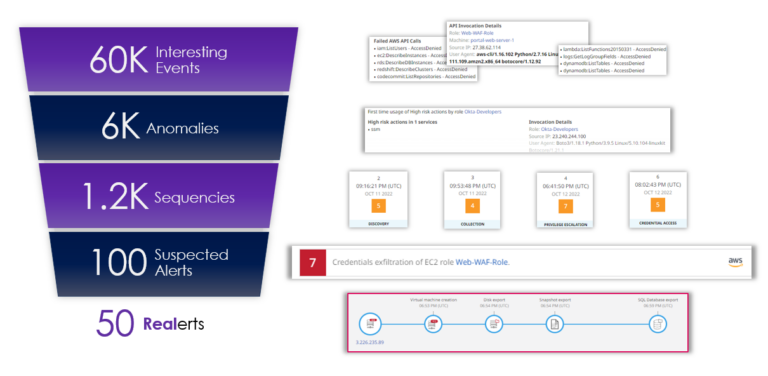
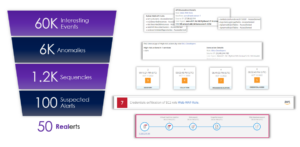
Throughout this entire process, tens of thousands of data points are sorted down to just a few alerts. This graphic shows a real example from one of our customers. From approximately 60,000 events over a one-month period, the security team got 50 alerts that needed to be investigated. The man-hours saved from this security team is immeasurable. It would take too many incident responders, more than money can buy, to start with 60,000 data points and then to get to 50 alerts before it is too late. Security teams do not have this time because as they are researching these events, threat actors are penetrating their environment and threatening their crown jewel assets – the most valuable data within an organization’s cloud.
The sorting of interesting data points to meaningful alerts:
- 60,000 events are sorted through and if they are interesting, they are aggregated and grouped into anomalies
- 6K anomalies are grouped into MBIs and then sequenced
- 1200 sequences are evaluated for risk
- 100 sequences are flagged as suspicious, and continued to be evaluate for risk
- 50 sequences are then promoted as an alert that the security team must investigate
Even if you have unlimited budget, which we know is never the case, there isn’t enough cloud security expertise to hire, and the operational cost will be immense. With Skyhawk Security Synthesis Platform, this operational efficiency is already significant in providing the best TCO and improving security by directing the security teams to know exactly which are the validated alerts that they need to focus on. These alerts matter. Security teams will not be wasting time on benign events – they will be focusing on the key threats to your cloud and your business.
Want to learn more? Contact us today for a demo!