Find Cloud Vulnerabilities that put your business at Risk with continuous Tabletop Exercises by Skyhawk
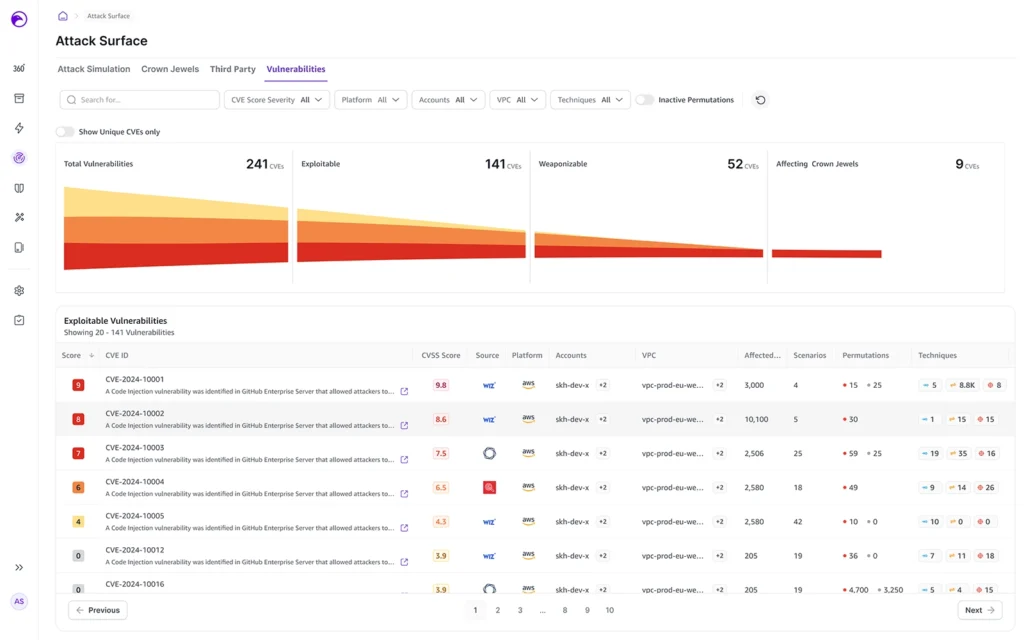
Organizations are overwhelmed with CVEs that need to be examined, triaged, and if deemed a threat, remediated. Our customers tell us they have tens of thousands of vulnerabilities floated by various vendors that require significant analysis, which requires significant time and effort. The challenge is that teams do not have enough people and/or time to […]
Close the Window of Opportunity on Threat Actors: How Skyhawk Optimizes your CNAPP
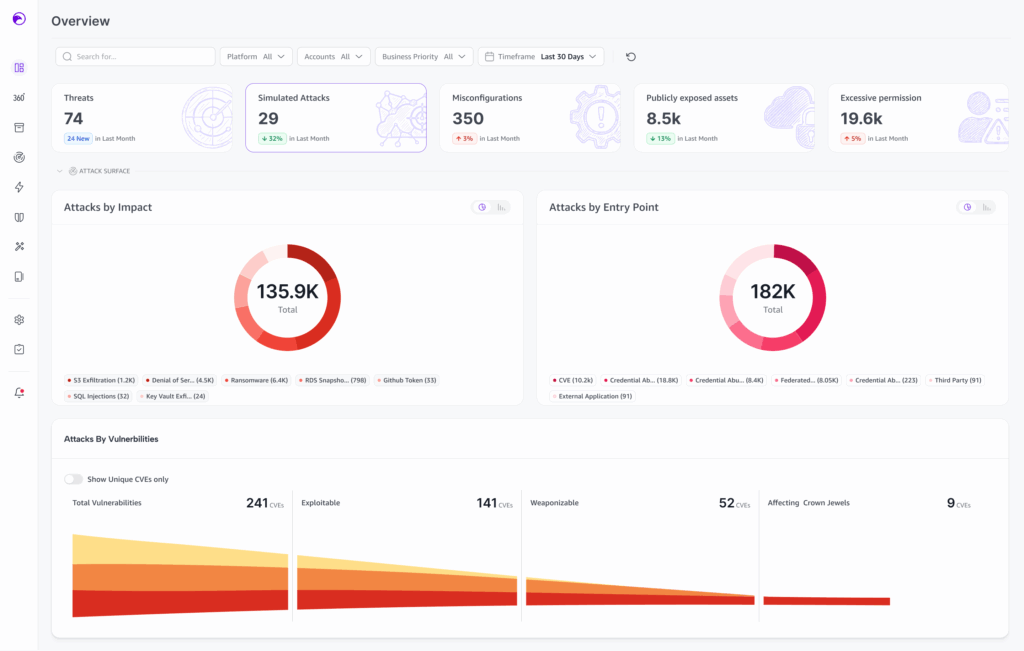
According to industry experts, remediation can take up to four months on average to address critical and high Cloud-Native Application Protection Platform (CNAPP) findings, like those from Wiz. Threat actors will not wait these months for any security team to resolve them – this is their window of opportunity. Threat actors will exploit these weaponized […]
Cloud Security Disciplines Converge to Effectively Prevent Cloud Breaches
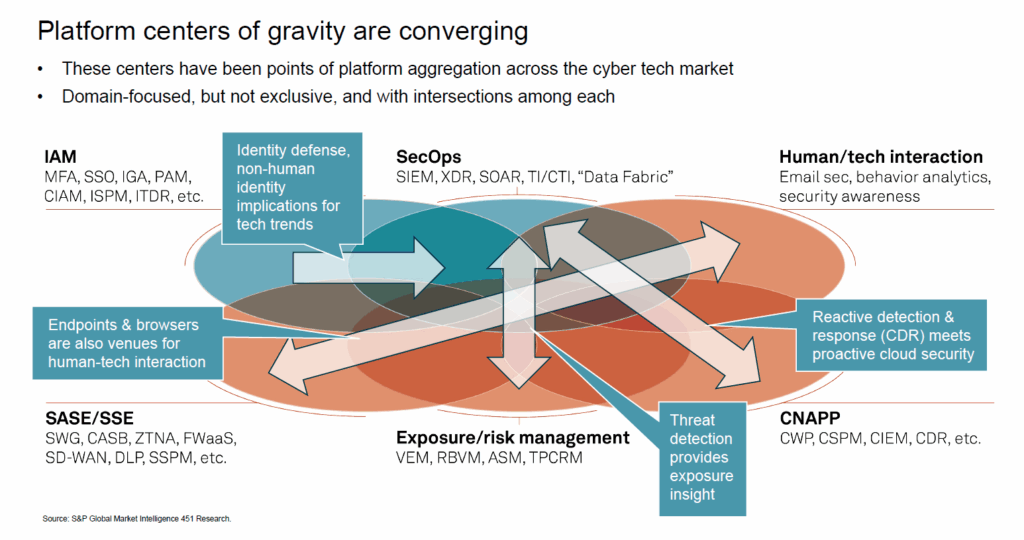
We attended an info session at security conference and this slide caught my eye – because all of the trends here center around preemptive threat detection. At Skyhawk Security, we started our journey to a proactive and preemptive approach to cloud security in 2023 with the introduction of our Continuous Autonomous Purple Team, and it […]
Jennifer Duman of Skyhawk Security Recognized as a 2025 CRN Inclusive Channel Leader

TEL AVIV, Israel, July 7, 2025 — Skyhawk Security, the originator of cloud threat detection and response (CDR), announced today that CRN®, a brand of The Channel Company, has named Channel Director Jennifer Duman to its prestigious list of 2025 Inclusive Channel Leaders. The annual list honors vendor, distributor and solution provider executives who are […]
Skyhawk Security mentioned in the Gartner® Emerging Tech: Tech Innovators for Emerging Sectors in Intelligent Simulation
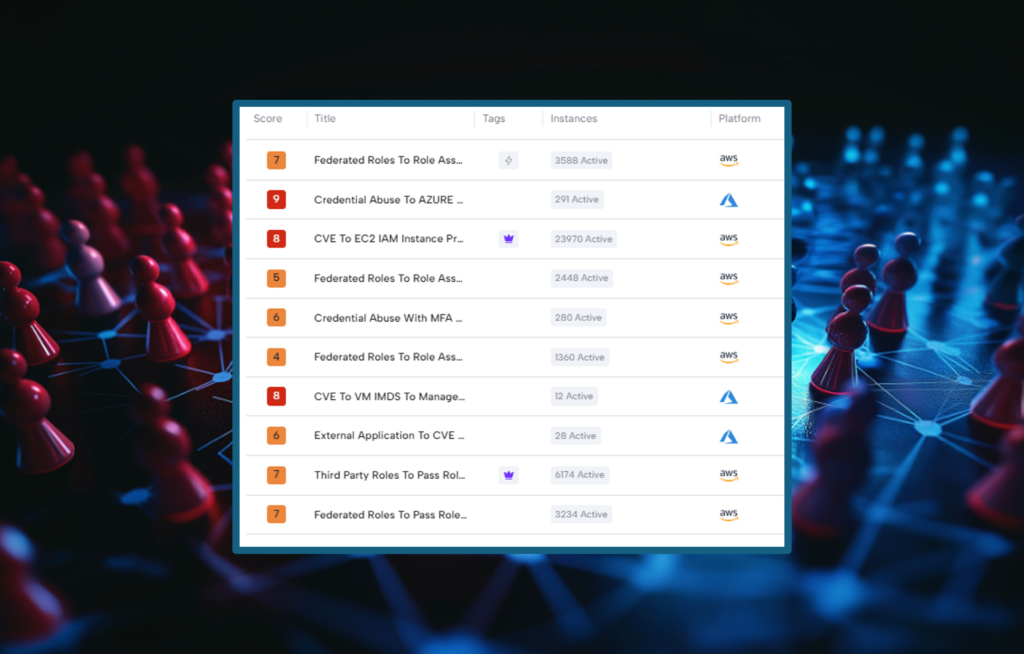
In our opinion, this research discusses how intelligent simulation helps organizations stay ahead of competitors. There are many ways that organizations can leverage intelligent simulation, for Skyhawk Security, our Continuous Autonomous Purple Team simulates attacks based on the specific configuration of the cloud attack surface, crown jewels, and cloud architecture. These attacks are customized for […]
Skyhawk Security and AWS: Better Together Cloud

Skyhawk Security revolutionizes cloud security with a preemptive strategy, which enables enterprises to stop attacks and prevent cloud breaches, through all layers, from the application to cloud. Skyhawk’s Continuous Autonomous Purple Team SaaS platform, is built on two main pillars: Cloud Threat Detection and Response – an agentless CADR, provides cyber defense, built on a […]
Skyhawk Security Launches Partner Program to Drive Growth And Deliver Preemptive AI-Driven Cloud Security at Scale

Program enables partners to meet escalating cloud threats with proactive solutions that eliminate alert fatigue and deliver tangible business outcomes Skyhawk Security, the originator of cloud threat detection and response (CDR), today announced the official launch of its partner program. The global initiative reinforces Skyhawk’s channel-first strategy, empowering value-added resellers (VARs), MSSPs and consultants to […]
Skyhawk Security Obtains Cloud Security Alliance STAR Level 1 Certification

Skyhawk Security has obtained Cloud Security Alliance (CSA) Security, Trust & Assurance Registry (STAR) Level 1, meaning that Skyhawk has publicly documented its compliance with CSA’s Cloud Controls Matrix (CCM). CSA STAR Level 1 (self-assessment) documents the security controls provided by various cloud computing offerings, helping users assess the security of the cloud providers they […]
Skyhawk Security Mentioned in the Gartner® Emerging Tech: Techscape for Startups in Cloud and Application Security
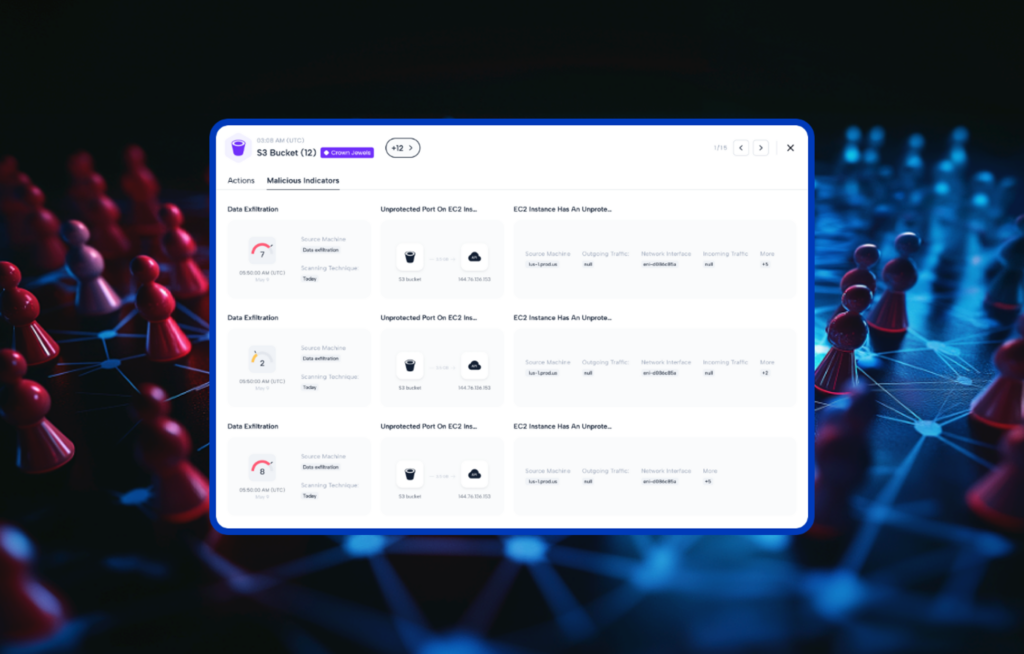
Skyhawk Security recently announced at RSA 2025 an expansion of our AI-Powered Purple Team to secure cloud applications and how they interact with the cloud infrastructure they are hosted on. This new capability identifies weaponized risks in cloud applications, the way these interact with the cloud infrastructure, the blast radius (reachability analysis), potential impact on […]
Cloud Security: Whose job is it?

There are several reasons why cloud security is so challenging, and the leading issue is roles and responsibilities. In the cloud there are three main groups that interact when securing the cloud: Cloud Security Team, Security Operations Center, and DevOps. These teams do not report to one another or manage one another so clear communication […]