Cloud Security: Whose job is it?

There are several reasons why cloud security is so challenging, and the leading issue is roles and responsibilities. In the cloud there are three main groups that interact when securing the cloud: Cloud Security Team, Security Operations Center, and DevOps. These teams do not report to one another or manage one another so clear communication […]
Another RSA Conference in the Books

As Skyhawk Security wraps up another RSA, we can reflect on the conversations, learnings, and fun. The conversations at the booth are always good, and it is clear that organizations are looking for a preemptive approach to cloud security. Several people discussed the overwhelming number of alerts they get from their Cloud-Native Application Protection Platform. […]
How Skyhawk Security Could have Prevented the Ransomware Attack on DDP Law
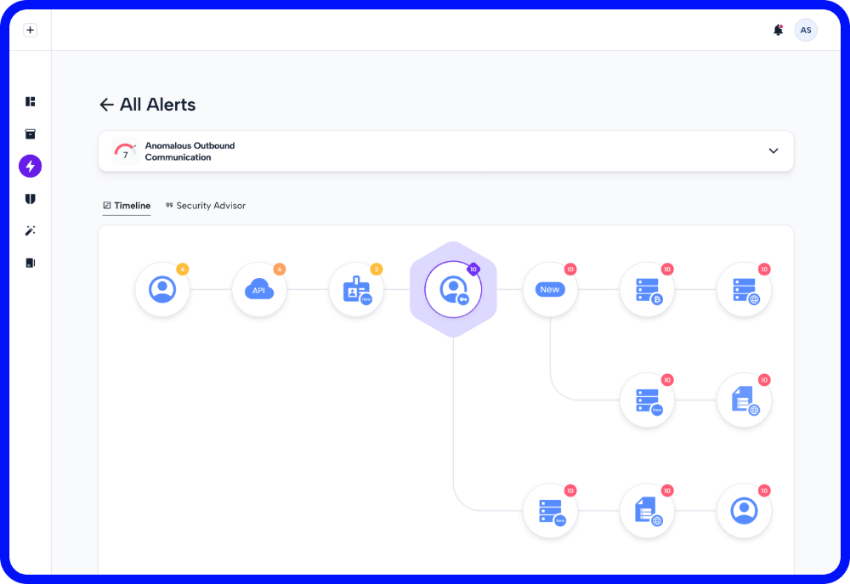
This blog was written by Asaf Shahar, VP, Products at Skyhawk Security The UK Information Commissioner’s Office (ICO) recently fined Liverpool-based law firm DDP Law £60,000 following a ransomware attack that exposed highly sensitive criminal case data. The investigation revealed critical security gaps: the absence of firewalls, lack of multi-factor authentication, unpatched systems, and most […]
Skyhawk Security mentioned in Gartner® Emerging Tech: Building Preemptive Security Solutions to Improve Threat Detection (Part 2)
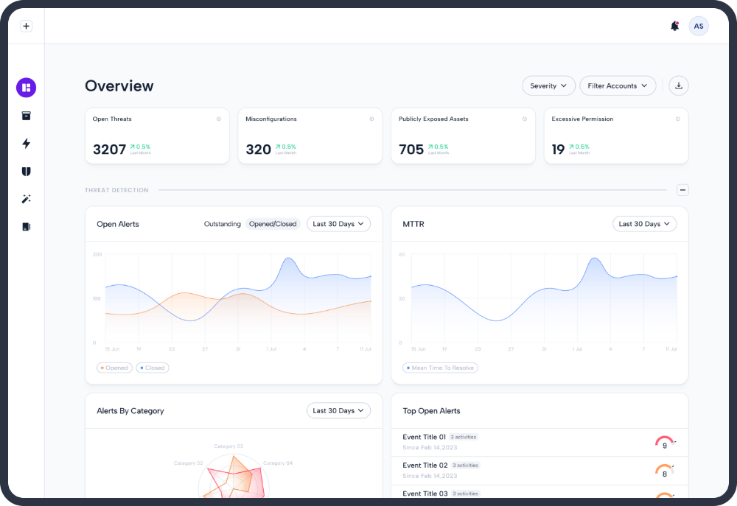
Skyhawk Security is at the collision of two trends within cloud security – for more than a decade it is clear that the cloud is perimeter less, attackers are logging in and not breaking in, and in addition, threat actors are using AI to generate more accurate and deadly attacks at higher volume and velocity, […]
Credential Theft Endangers Cloud Environments in 2025

In an increasingly cloud-dependent business landscape, a disturbing trend has emerged that threatens the very foundation of cloud security: credential theft. Recent incidents and reports indicate a dramatic surge in credential theft attacks and subsequent abuse. This indicates potentially devastating implications for cloud environments where a single compromised credential can provide access to vast troves […]
Operationalize Your Cloud-Native Threat Exposure Management (CTEM) Program
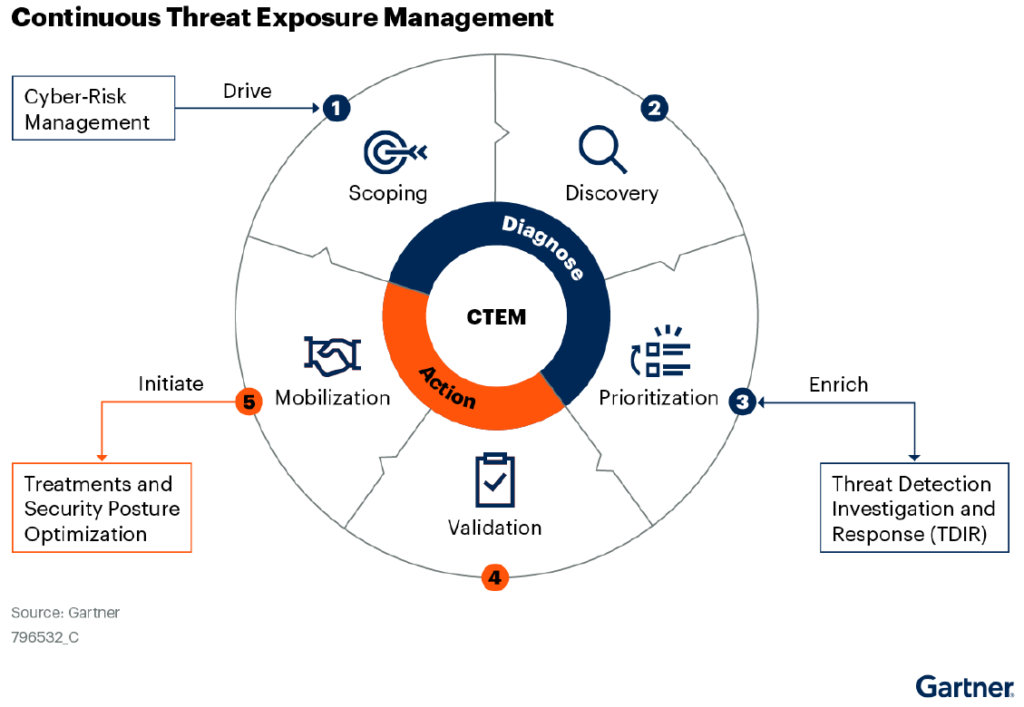
Continuous evolving clouds with continuously evolving threats need continuous threat exposure management (CTEM). This programmatic approach to managing threat exposures can help organizations dramatically reduce breaches. Many organizations are well on their way. According to a Gartner Peer Insights survey, 75% of respondents either have a CTEM program in place or are working on implementing […]
2025 Cloud Awards: Skyhawk Security named a Finalist in Cloud Security Awards – AGAIN

For the second year in a row, Skyhawk Security stands out in a competitive market! The organization is proud to announce that it has been named a finalist in the 2025 Cloud Security Awards program in two categories: Best Cybersecurity Solution Best Use of AI in a Cloud Security Solution Operated by global cloud […]
Skyhawk Security Hires Channel Veteran Jennifer Duman to Lead Global Partner Program

TEL AVIV, Israel, April 9, 2025 – Skyhawk Security, the originator of cloud threat detection and response (CDR), proudly announces the appointment of its new Channel Director, Jennifer Duman. She brings more than 20 years of experience to the role, with a proven track record of accelerating revenue growth for startups and building successful channel […]
Skyhawk Security mentioned in the 2025 Gartner® Emerging Tech: Techscape for Detection and Response Startups

Skyhawk Security started in the 3rd generation of Cloud Threat Detection and Response (CDR) platforms at its inception in May of 2022, supporting AWS, Azure, and Google Cloud to deliver a robust Preemptive Cloud Security Platform. The several layers of machine learning models sort through thousands of events, log information, telemetry, and even use information […]
Early Disruptive Trends in Cybersecurity: Preemptive Cybersecurity Solutions

In recent Gartner® research, Emerging Tech Disruptors: Top 5 Early Disruptive Trends in Cybersecurity for 2025, it is noted that there will be a shift from detection and response to preemptive cyber defense using key AI-advancements like Simulation Digital Twins. Strategic Planning Assumption: By 2030, preemptive cybersecurity solutions will account for 50% of IT security […]