Cybersecurity Awareness Month: What about the cloud?

October is Cybersecurity Awareness Month, and on this last day, let’s talk about cloud security. What started as a United States government initiative some 23 years ago, continues to this day under the leadership of CISA. The agency, which routinely deals with serious tasks such as guiding critical infrastructure in cyber defense and protecting the […]
What can we learn from recent cloud security breaches?

Over the past year there have been several prominent cyber incidents involving the cloud. These incidents have illustrated the dependency of organizations on the cloud, the vulnerability of the cloud, and the motivation of attackers to utilize this to their advantage. But if we look closer, we can also identify some lessons that can be […]
Cloud Hacking, From Russia with Love

Russian hackers are shifting their interest to the cloud, and have successfully breached cloud infrastructure. This is what a joint advisory issued by the U.K.’s National Cyber Security Centre (NCSC), the NSA, CISA, the FBI, and cybersecurity agencies from Australia, Canada, and New Zealand (also known as “The Five Eyes”) The advisory details recent tactics, […]
What does the new NIST password guidelines mean for cloud security?

The common joke around security folks is that everyone knows what a password is, but remembering their own passwords is challenging. Despite these challenges, passwords are an essential security mechanism. NIST is updating its recommendations regarding passwords policy, presenting is an opportunity to learn why passwords were created and why do we need them. How […]
Real Customer Scenarios: See how Skyhawk Security Stopped the Breach
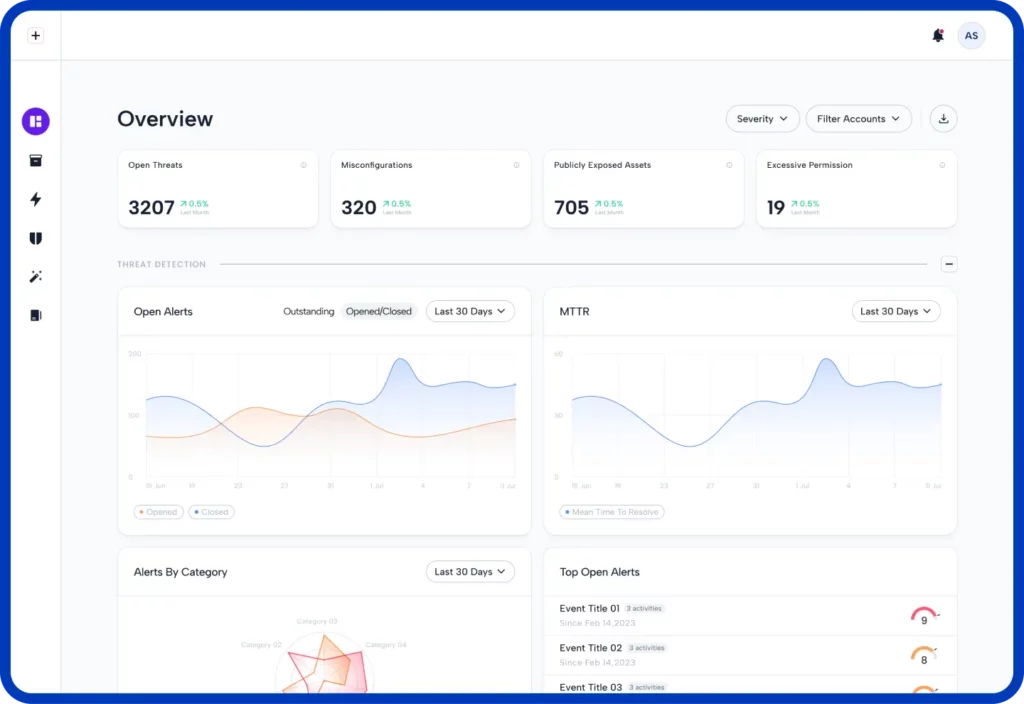
When evaluating a cloud security solution, it is imperative to know how well it will detect threats in time to prevent a breach. Here are three examples out of many in which our customers were able to detect an incident and stop it in time to prevent a full-blown breach. Incident 1: Trying to take […]
For Cybersecurity Month, you can try Skyhawk for free!
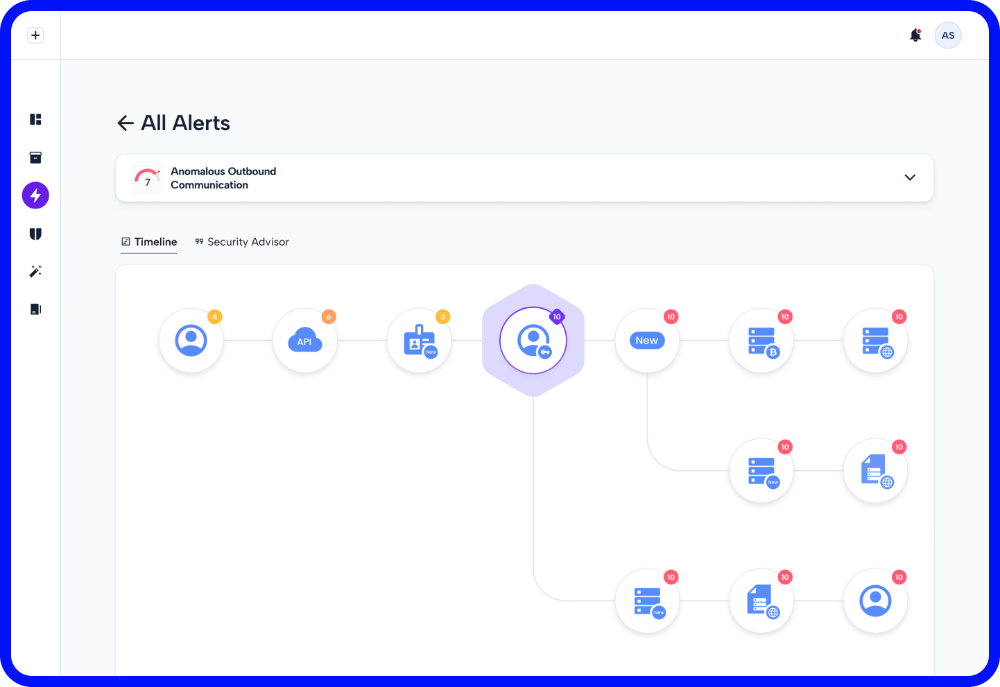
In honor of Cybersecurity month, Skyhawk Security is offering a free 30-day subscription to the complete platform. Why try Skyhawk Security? Your Security and Development teams are overwhelmed with the number of CNAPP findings. There is a constant argument between security and development regarding what is a true finding vs a false one. This puts […]
The Rationale behind Autonomous Purple Team Technology
When Skyhawk set out to develop a new cloud security solution it was already clear that traditional security paradigms were not appropriate for cloud environments. Traditional security was built to secure on-premises environment. These environments were protected by numerous security means (firewall, sandbox) and malicious software was introduced by USB drives, email or clicking on […]
How the cloud amplified supply chain risk and what you can do about it?

As seen from recent security incidents involving cloud-based systems (for instance- numerous cyber incidents in the healthcare sector), reliance on cloud services can amplify cybersecurity risks associated with third parties and the supply chain. For example, some organizations allowed external contractors access to their Snowflake accounts for customization. Some contractors had very lax security posture […]
Continuous Threat Exposure Management (CTEM) versus Traditional Vulnerability Management
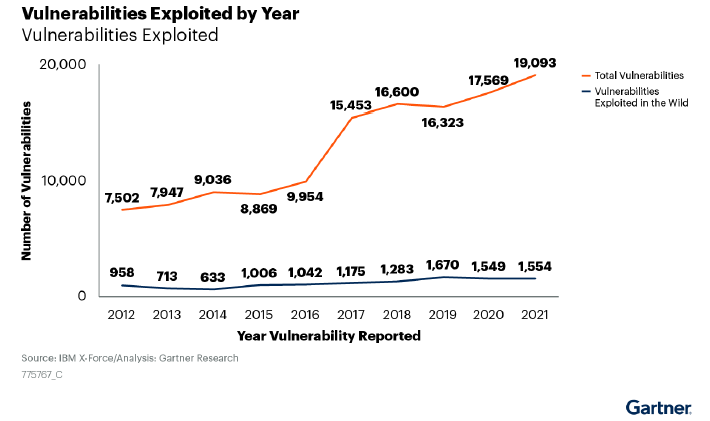
With the exploitation of vulnerabilities on the rise, many organizations are evaluating vulnerability management solutions. However, vulnerability management provides only a partial picture of what is happening in the environment. Organizations need to take a more comprehensive approach, looking not just at the vulnerability, but the exploitability of the vulnerability, and the business value of […]
The Top 10 Questions on Continuous Threat Exposure Management (CTEM)
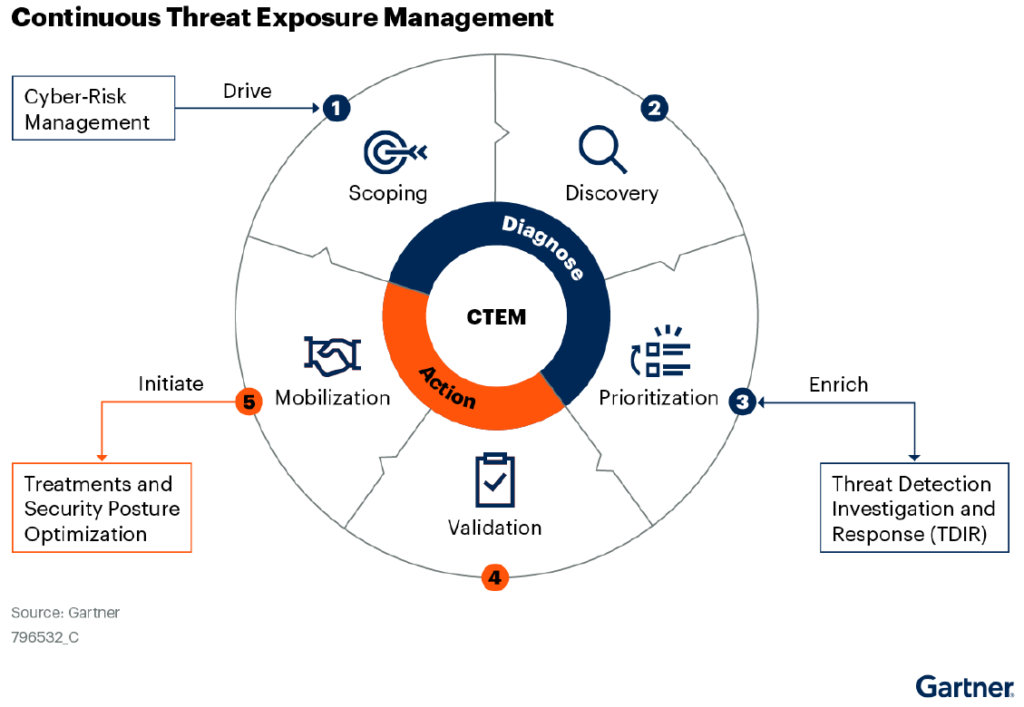
Cloud security teams are evolving their security approach, going beyond alerts and looking at the threat exposure with a business context. This enables the cloud security team to prioritize security gaps based on the value of the asset behind it. It also makes it easier for the CISO to clearly communicate what the threat exposure […]