Skyhawk Synthesis Security Platform mentioned in the 2024 Gartner® Emerging Tech Impact Radar: Preemptive Cybersecurity
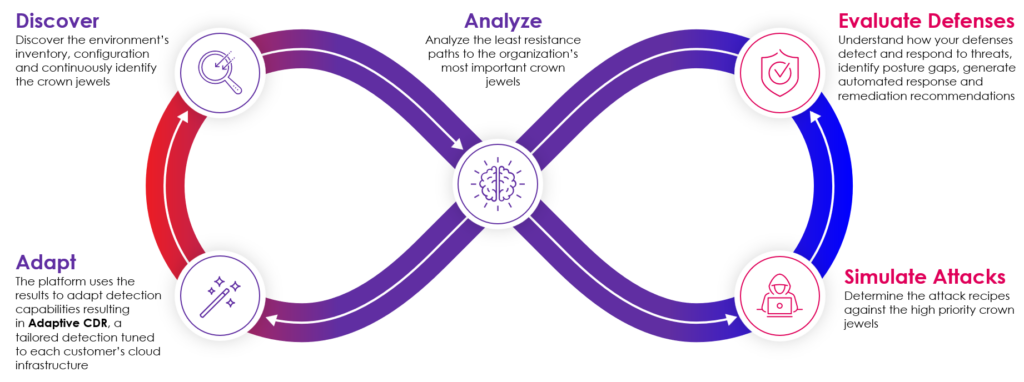
Skyhawk Security’s AI-based Autonomous Purple Team enables organizations to take a proactive approach to cloud security, preempting threats so security teams can be prepared for what threat actors are going to do. Through AI-based rehearsals, which leverage a Simulation Twin so there is no impact to production, the platform is able to prepare verified automated […]
How did the Chinese manage to penetrate the entire communications infrastructure of the United States? How will the privacy of US citizens improve?

We may have recently been exposed to the largest cyber campaign of all times, in which China managed to completely penetrate the communications infrastructure of its great rival, the United States.In doing so, gained access to huge amounts of invaluable information. The attack is so serious that the US government is in a panic – […]
Your Identities are your vulnerability.

The global cloud market continues to grow rapidly, growing 23% year-over-year. This year, Google captured 13%, up from 10% last year. Google complements this impressive growth rate with an emphasis on privacy and security. The commitment to security is clear, as Google is the first cloud service provider mandating Multi-Factor Authentication (MFA) on all cloud […]
The Next Insider Threat Resides in the Cloud

An insider threat is a security risk posed by individuals with authorized access to an organization’s systems. This could include employees, contractors, or third-party vendors. Insider threats can be intentional or unintentional, and they can cause significant damage to an organization’s reputation, finances, and intellectual property. How Cloud Computing Amplifies Insider Threats Increased Access: Cloud […]
Skyhawk Security re:Invent Recap

Re:Invent has come to a close and we had a great week! We kicked off the week with our product announcement. Did you know that most threat actors (70%) are logging into the cloud – they are not “breaking in”. Today, threat actors are using leaked credentials and API keys to log into the cloud, […]
Skyhawk Security Interactive Cloud Threat Detection and Response Supports Cloud Native Zero Trust
Skyhawk Security is proud to announce the expansion of its cloud threat detection and response capabilities with Interactive CDR. This new capability expands the team that can verify if an activity is malicious or not, by going to the alleged source of the activity, incorporating principles of Zero Trust. This crowdsourcing of threat verification reduces […]
New Enhancements to Skyhawk Security
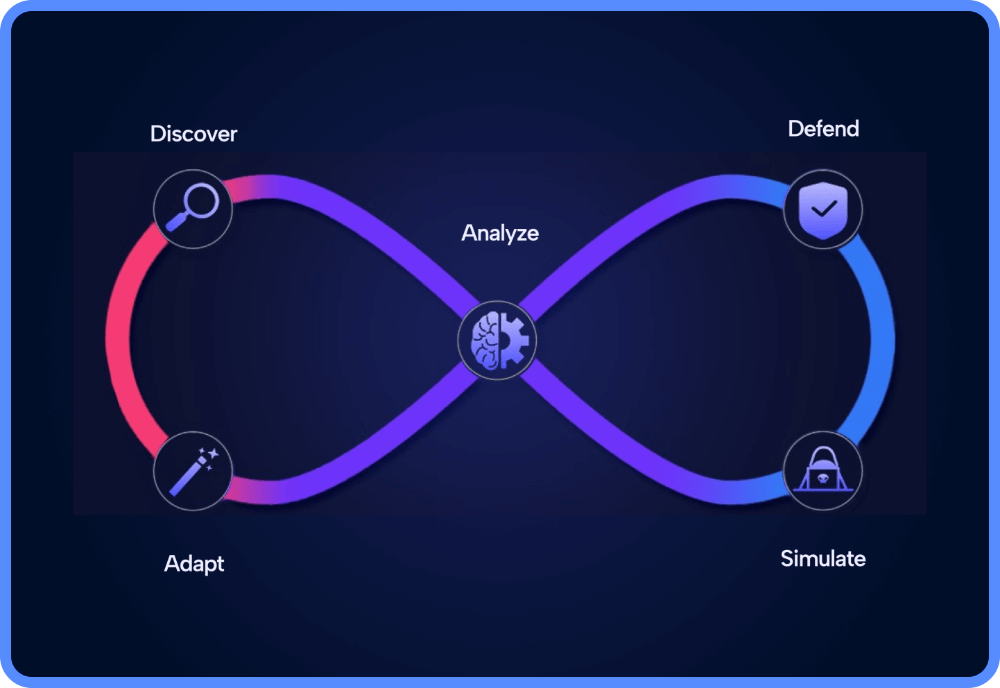
Skyhawk Security announces the availability of new features and integrations of its Autonomous Purple Team, aimed at extending detection and improving security validation as well as pre-validating threat detection alerts, to effectively manage the security of your cloud. The company now offers free 30 days self-subscription to allow everyone to experience its Adaptive CDR and […]
Why Continuous Monitoring is the Key to Cloud Security

By Asaf Shahar, VP, Product at Skyhawk Security Securing cloud environments presents unique challenges due to their constantly evolving nature. CERT-IL’s alert on public cloud threats (ALERT-CERT-IL-W-1810) underscores common vulnerabilities—exposed credentials, service misconfigurations, and inadequate tenant isolation—frequently exploited by attackers. This blog delves into why continuous monitoring is essential for cloud security, with a particular […]
Cloud Credential Theft: Advanced Techniques and Evolving Defenses

By Asaf Shahar, VP, Product at Skyhawk Security As cloud security strategies evolve, attackers are staying a step ahead, moving beyond traditional credential theft tactics like phishing to adopt more sophisticated methods- some of which we’ve witnessed in the past. Credential theft in cloud environments can lead to severe consequences, including privilege escalation, data breaches, […]
Stop by Skyhawk Security’s booth at re: Invent!

AWS re:Invent is less than a month away – stop by booth #2152 to learn about Skyhawk Security and our award-winning AI-based Autonomous Purple Team. With Skyhawk’s Continuous Proactive Protection, our customers have realized: Significant Time Gains: Our customer has shared with us that they have realized hours back in their day, as they do […]