The year is 1985. The movie Back to the Future is released, and the crowds are pouring to see Marty McFly travel through time. If you were in high school back then, it just might be that your school records were now stollen. How?
In December 2024, PowerSchool, a leading K-12 education technology company supporting numerous schools across North America, experienced a significant data breach. The breach was identified on December 28, 2024, when unauthorized access was gained to PowerSchool’s customer support portal, known as PowerSource, through compromised credentials.
This unauthorized access exposed personal information of students and educators, including names, contact details, dates of birth, medical information, Social Security numbers, and more.
Currently, the company serves over 60 million students across 4 states and more than 18,000 schools. However, expanding the reach and impact of this breach, is the fact that schools have uploaded historical data to the system as well. For instance, some schools in Canda state that they have data dating back to 1985. That’s four decades of data – compromised.
How the Breach Happened?
Attackers used stolen login credentials to gain unauthorized access to the PowerSource portal. According to some speculations, these belonged to a service account and were not secured by MFA. Once inside, the attackers accessed sensitive personal information, which included data on students and educators, and then exfiltrated this information, leading to the data breach.
The breach impacted many school districts in the U.S. and Canada, including several large districts in Virginia, California, and Toronto. The total number of affected schools and individuals is still not fully known.
PowerSchool reportedly paid a ransom to prevent the publication of the stolen data following a cybersecurity breach. The company stated that it received assurances from the attackers that the data had been deleted and no additional copies existed. At this point, the stolen data has not been published on the darknet, but that does not assure the angry parents and students. The company now faces 23 lawsuits over this huge Data Breach.
From Ransomware to Data Theft
PowerSchool data breach did not cause any operational disturbances to the company’s services. The breach primarily involved the theft of sensitive personal data rather than disrupting the functionality of PowerSchool’s platforms or its ability to serve schools.
This suggests that the attack was focused on data theft rather than ransomware designed to lock systems or prevent access to services. This also indicates that hackers knew what they were doing, and when to do it, executing their plans in the midst of the holiday season, when the schools were on vacation and vigilance was lower.
Breadth, Depth, and Length of the Incident
Many security incidents have a decent “blast radius”, but few encompass so many people over such a long time period with such high-value data. According to some reports the breach impacts a staggering number of 62.4 million students and 9.5 million teachers. It includes students and teachers from 40 US states and Canada. In some cases, the data goes way back. In Canada, data from 1985 was compromised and in California’s Menlo Park City School District there was data from 2009 stolen. From Ontario, the following data was compromised, including :
- First, middle, and last names
- Date of birth
- Gender
- Health card number
- Grade level and school information
- Start/end date as a student
- Ontario Education Number
- EQAO accommodation information
- Medical information (i.e., allergies, conditions, injuries)
- Home addresses
- Home phone numbers
- TDSB student number
- TDSB email address
- First Nations, Métis, and Inuit information
- Residency status
- Principal/vice principal notes (including discipline notes)
Lessons Learned
This may seem like this a monstrous hacking operation, conducted by proficient hackers, and therefore, impossible to stop. But there were several steps that the hackers took that defenders using a modern, AI-based cloud detection system could have identified and acted earlier. In particular, the massive exfiltration of data should have been identified and alerted to security operators. AI-based systems could have been used to run simulations prior to the incident, map potential breach routes and plan proper responses prior to the incident.
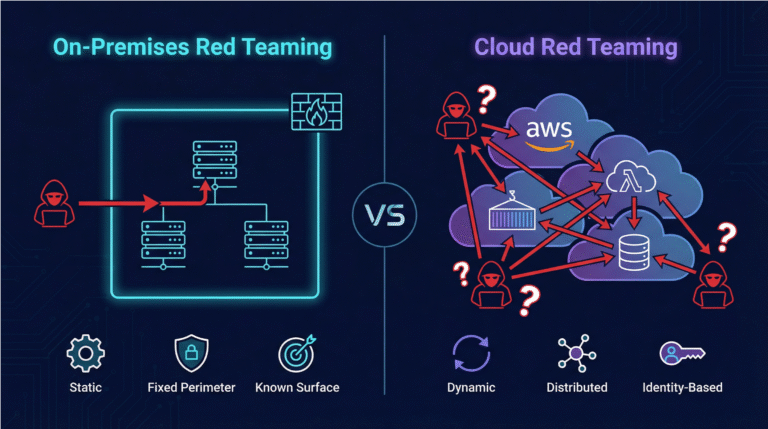
Skyhawk’s AI-based Autonomous Purple Team enables a proactive approach to Cloud Security for the very first time.
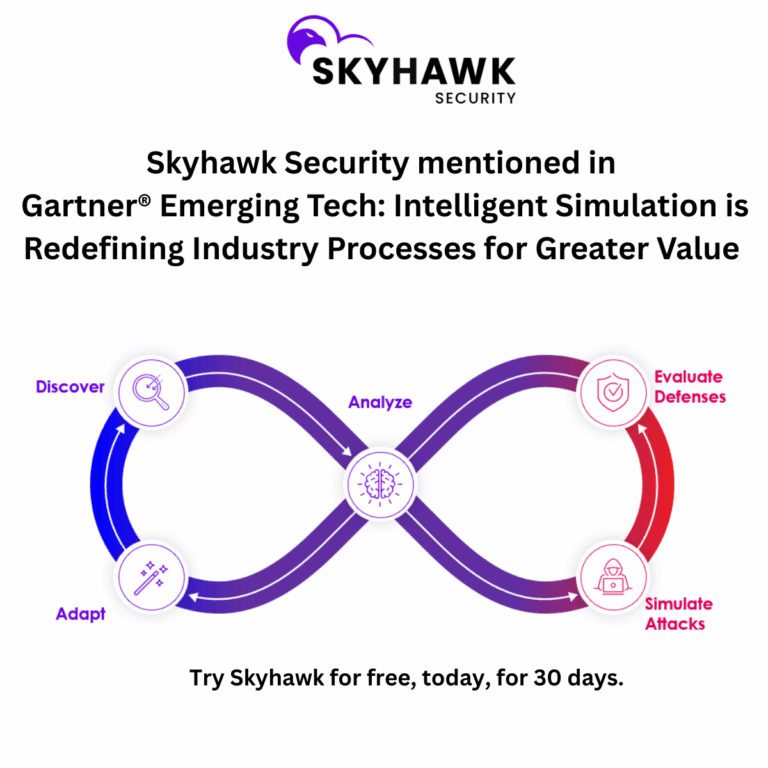
Skyhawk Security’s Continuous Proactive Protection helps organizations discover their crown jewel assets and then the GenAI-based red team and blue team see how defenses hold up against an attack. This helps organizations prioritize the ease of penetrating their defenses along with the value of the data assets at the end of the attack, so they know where to start updating their security posture, threat detection, and response and remediation.
As Skyhawk is continuously evaluating the cloud as it updates, organizations can truly realize the value of the cloud. Skyhawk’s AI-based autonomous purple team is constantly evaluating defenses as the cloud architecture evolves, ensuring your most valuable cloud assets are protected.
Skyhawk Security is not a one-stop shop for your Cloud-native CTEM framework, but it does deliver a significant portion of the capabilities. Many organizations already have too many security tools, so adding several tools to implement this framework is not feasible, but implementing one more product is.
Read more about our Purple Team here!
Or check out our Free Purple Team Assessment!