With the exploitation of vulnerabilities on the rise, many organizations are evaluating vulnerability management solutions. However, vulnerability management provides only a partial picture of what is happening in the environment. Organizations need to take a more comprehensive approach, looking not just at the vulnerability, but the exploitability of the vulnerability, and the business value of the asset behind it. The full business and exposure context of the vulnerability is needed to effectively secure the business. Many organizations are evolving their VM management tools to continuous threat exposure management programs (CTEM), so they can get a better understanding of the organization’s overall threat profile.
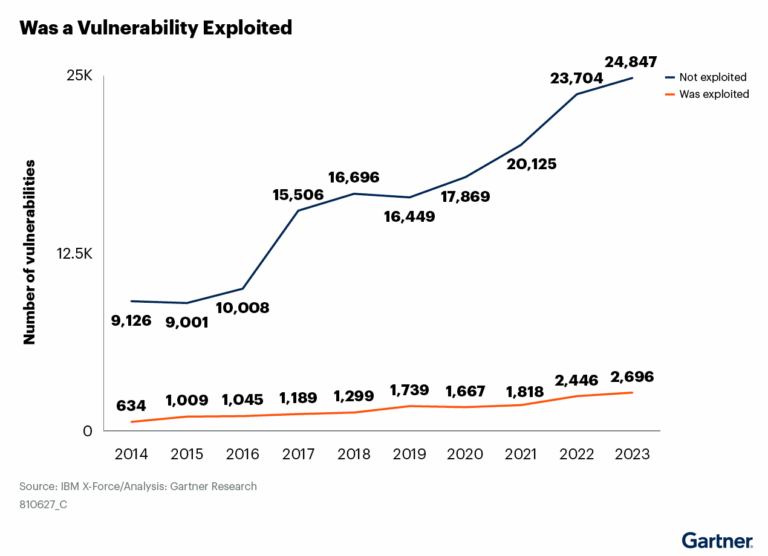
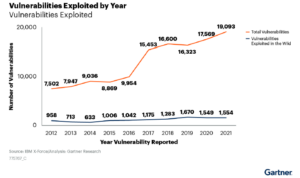
Vulnerability Exposure is on the Rise
Gartner®, The Top 5 Elements of Effective Vulnerability Management, Jonathan Nunez, January 9, 2024.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
We can see that vulnerabilities have just about doubled in the last 10 years or so and the exploitation of those vulnerabilities has increased by 50%. The math is working in the security teams favor, but ignoring the vast inventory of vulnerabilities that could be exploited would be a huge mistake. It is impossible to manage Security teams need to manage vulnerabilities and in the context of the threat exposure of the business.
What is Vulnerability Management (VM)?
VM tools scan enterprise networks and establish a baseline and trending of vulnerability conditions for devices, applications and databases; identify and report on the security configuration of IT assets; discover unmanaged assets; support specific compliance reporting and control frameworks; support risk assessment and remediation prioritization; and support remediation by IT operations groups.
What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management is a programmatic approach to managing threats in the context of your business. We have a blog that talks about CTEM 101 and the top 10 CTEM questions. There are three key attributes in the programmatic approach of CTEM that you do not see in other security disciplines.
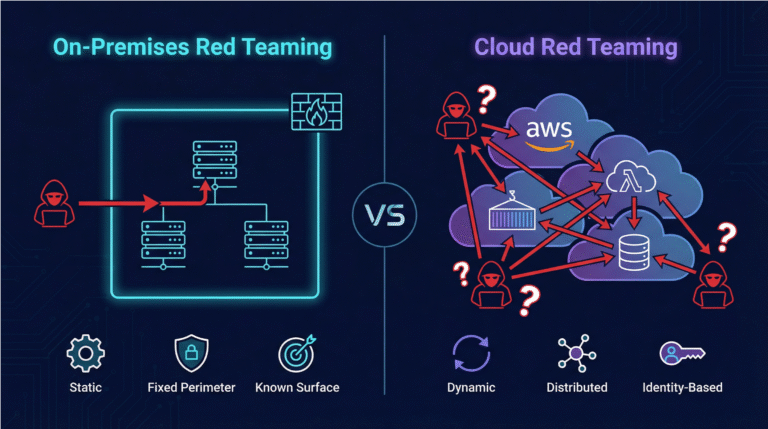
- Continuous: The continuous aspect of CTEM is different from other approaches, and this aligns particularly well with CTEM for cloud. Cloud architectures are changing rapidly and often to meet changing business needs and requirements. This is why organizations move to the cloud. However, organizations that invest in cloud, need a security framework that takes into account the frequency of this change.
- Feedback: It is not enough to just continuously evaluate the cloud security and cloud architecture – the feedback needs to be implemented and used to update the cloud security. What vulnerabilities need to be addressed, what posture issues, permissions, and more to update the cloud security. This continuous evaluation of cloud architecture to improve cloud security reduces the overall threat exposure of the cloud, reducing the exposure of the business.
- Information-driven alerts: Threat actors are aware of deficiencies in patch management and lack of prioritization. In other words, if they know medium –severity vulnerabilities rarely get addressed, it presents a path of potentially least resistance. This is not the case for Skyhawk. It does not just look at the alert and simplicity or sophistication of the alert. It looks at the alert and the value of the business asset behind it. This information enables security teams to prioritize alerts and prevent cloud breaches.
Vulnerability management is not enough for today’s enterprises, especially if they are in the cloud. Once a vulnerability has been identified and resolved, chances are the cloud architecture has changed so significantly that the fix is no longer required or dated.
Skyhawk Security: Leading the Way with CTEM
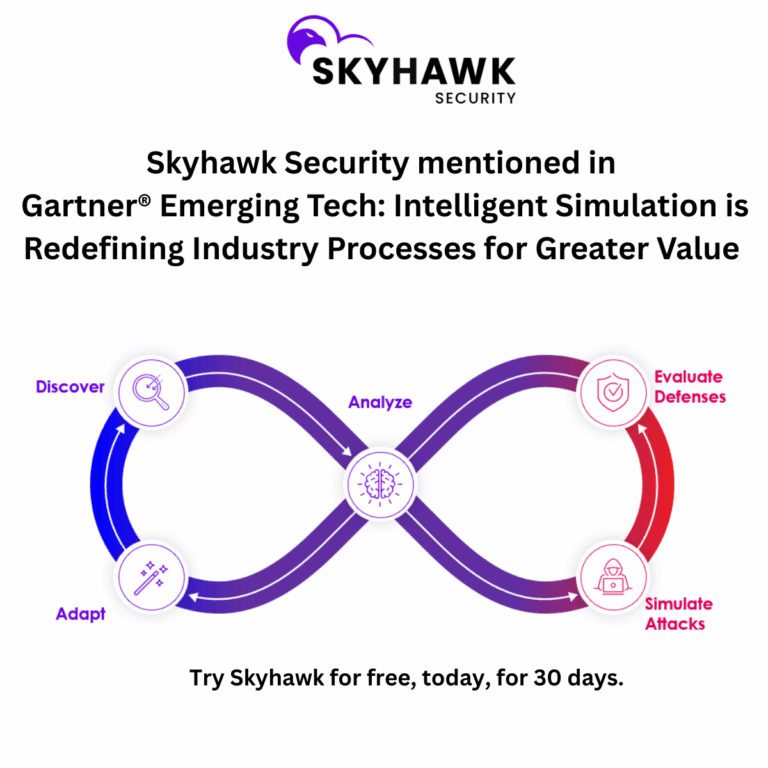
Skyhawk Security’s platform is at the forefront of Continuous Threat Exposure Management, offering an AI-driven, proactive approach to cloud security that is both innovative and effective. Central to this is the Autonomous Purple Team—a unique feature that combines the strengths of both red (offensive) and blue (defensive) teams to continuously assess and improve your cloud security posture.
Autonomous Purple Teaming: Unlike traditional security approaches that rely on separate red and blue teams to test defenses and respond to incidents, Skyhawk’s Autonomous Purple Team merges these functions into a continuous, automated process. The platform continuously analyzes your cloud infrastructure, running attack simulations that mimic the tactics, techniques, and procedures of threat actors. This not only identifies vulnerabilities but also provides actionable insights on how to strengthen defenses immediately. By simulating attacks on an ongoing basis, the Autonomous Purple Team ensures that your security measures are always tested and validated against the latest threats.
- Verified Alerts and Automated Responses: Skyhawk Security enhances the effectiveness of its Autonomous Purple Team by ensuring that all alerts are pre-verified. This means that security teams receive only actionable intelligence, significantly reducing the risk of responding to false positives. The platform’s automated responses are also verified, allowing for immediate and precise remediation of threats. This integration of verified alerts and automated responses helps prevent security incidents from escalating into breaches, providing peace of mind that your cloud environment is secure. This is a key component of CTEM, and Skyhawk Security delivers it.
- Tailored AI driven incident detection solutions: Skyhawk Security’s multi-layered cloud incident detection AI approach is designed to work hand-in-hand with the Autonomous Purple Team. Custom-built machine learning models, updated daily, ensure that malicious activities are detected within minutes, preventing an incident from becoming a breach, without increasing false positives or negatives. These machine learning models are customized to identify threats in your cloud, including unknown unknowns.
Embrace CTEM with Skyhawk Security
In an era where cloud environments are increasingly complex and dynamic, organizations need more than just traditional vulnerability management. Skyhawk Security’s platform, powered by the Autonomous Purple Team, offers a proactive, continuous, and automated approach to threat management and incident detection that is essential for safeguarding your most valuable cloud assets. By integrating real-time attack simulations, verified alerts, and automated responses, Skyhawk Security provides a robust solution that keeps your organization ahead of the curve, ensuring comprehensive protection against evolving cyber threats to stop cloud breaches.