This post about ML in cybersecurity was written by Jennifer Gill, VP Product Marketing at Skyhawk.
Securing a cloud while meeting the need of developers and the business and supporting compliance initiatives, is difficult to say the least. Analyzing trends across user behavior, application usage, cloud performance, for a single account and then across clouds, this makes things even more difficult. Skyhawk Security leverages advanced machine learning (ML) techniques and artificial intelligence (AI) to build models for ongoing behavioral analysis of the runtime for more accurate threat detection.
Now you have likely heard from many, many security vendors that they are also using AI and ML to identify threats. In this blog, we will walk you through Skyhawk Security’s ML, how we are unique, and why our ML is many steps ahead of the market.
Skyhawk Synthesis Security Platform leverages AI and ML for cybersecurity in three major ways:
- A personalized model for your environment: The platform will create a ML model per customer cloud, for the applications in the cloud, and for the users who access the applications in the cloud. This ensures that any interesting behaviors that are raised are in fact, a deviation from what is normal for this cloud. This personalized model reduces false incidents and ensures that alerts are activities that should be investigated.\
- MBIs (Malicious Behavior Indicators): These are indicators that we develop based on repetitive suspicious and malicious activities that the platform observes. Once the platform observes a behavior on an ongoing basis, AI and ML capabilities analyze the behavior and create an MBI. An MBI alone is not usually indicative of an attack, but it is indicative of an interesting activity. The platform creates new MBIs continuously as we see new and interesting behaviors that could pose a threat to the environment. Skyhawk’s advanced artificial intelligence and machine learning techniques create new MBIs all the time based on new behaviors and activities.
- Identifying Actual Threats/Incidents with the Attack Sequence: The platform aggregates MBIs into a sequence of events which shows how a breach or attack has unfolded. The attack sequence has two purposes. First, they show the overview of how a threat actor penetrated the environment. Attacks do not occur because of a single event; the attack is a series of choreographed events executed slowly and meticulously so as not to draw attention. Second, the attack sequence helps reduce the noise as we only raise these to a level of alert once a defined threshold has been reached, flagging the sequence as a threat or incident that requires investigation. The sequences are analyzed with advanced AI tools for anomaly detection to further reduce false incidents
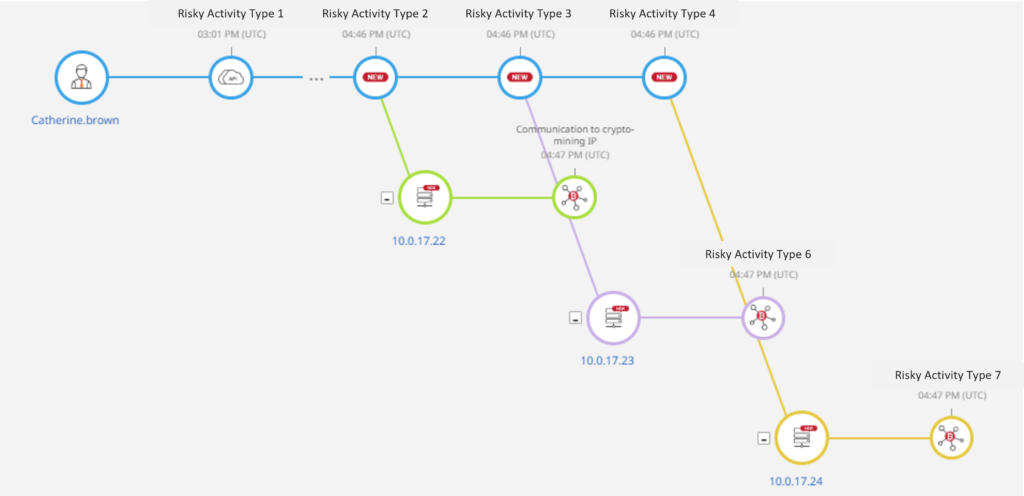
Figure 1. Example of an Attack Sequence
In this example, we have renamed the MBIs to generic names, but you can see how the attack developed over time. Here instances were created to then start malicious crypto mining activities.
All these elements deliver predictive results that dramatically reduce false incidents, so security teams react only to malicious and threatening activities. Ensuring that security teams are responding to actual incidents eliminates alert fatigue. This is also part of the secret sauce – we are constantly executing per-sequence behavioral modeling to evaluate MBIs and the behavioral sequences to see if there is an issue. No one else does this. Other security vendors look at a data point and once it is deemed not a threat, it is dismissed forever. But attacks are rarely executed in a single event; an attack is comprised of several events. Skyhawk Security knows this, which is why we are always looking at the sequence and never dismiss interesting data points.
How do we build MBIs?
Let’s say we are building an MBI to identify suspicious communication behaviors – maybe something like outbound communication that looks threatening or strange. We would analyze more than 400 million VPC flow logs – modeling the MBI over millions of data points. Algorithms are designed showing how we define the problem. Patterns are analyzed across the entire customer base to identify trends and confirm malicious behavior. An MBI is created to represent the malicious indicator so that it can more readily be recognized and sequenced.
Skyhawk Synthesis leverages AI and ML for cybersecurity in advanced ways to better identify actual threats to increase the productivity and morale of the SOC. We do not look at one point in time to determine if there is a malicious activity or event happening, we analyze many data points. This dramatically reduces false positives and false negatives. As we never dismiss interesting data points, MBIs, or other events, and keep evaluating them within our models, this also ensures that nothing is missed while again, reducing false incidents. Skyhawk Security will detect the real threats in your cloud environment – the realerts.