Security companies are overwhelming security teams with cloud threat detection and response tools, but what does this really mean? What is cloud threat detection and response and what are the capabilities that security teams should look for in a cloud threat detection and response platform? This blog will go over the top capabilities for cloud threat detection and response platforms (CDR Platforms).
What is CDR? What should the platform achieve?
CDR stands for cloud threat detection and response. CDR products detect threat actors that are in your environment and prevent them from breaching your environment. The goal is to prevent the breach, keep your company’s name out of the Wall Street Journal, ensure there is no bad press, and most importantly, that your customers’ and employees’ data has not been compromised.
There are three main types of breaches, which we discuss in our “Threats we Detect” Whitepaper, located here, that CDR products detect and stop:
- Business disruption: The goal of some threat actors is to hurt an organization or brand, and this is done by bringing down the website, preventing the company from servicing customers, etc.
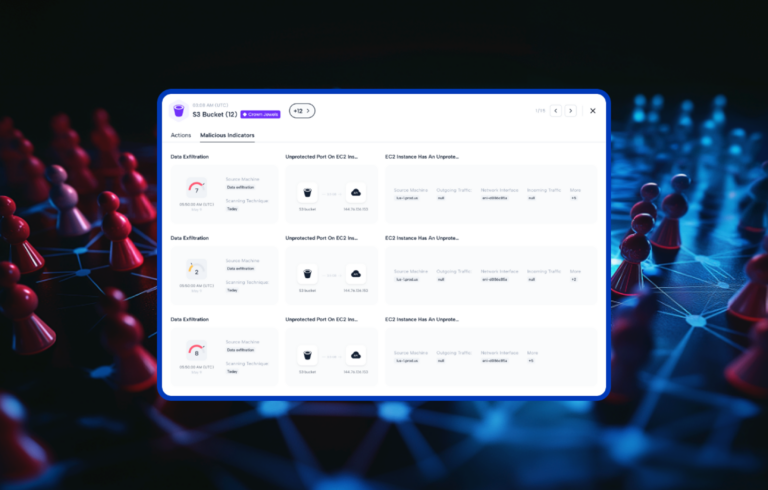
- Stealing data (exfiltration): This is the most common type of breach as organizations typically steal data, such as employee or customer data, to then steal money from back accounts, set up credit cards, unbeknownst to the person involved, or to demand a ransom for the safe return of the data.
- Malicious use of assets: Finally, the third main type of breach is malicious use of assets. For example, a threat actor may steal compute power in an organization’s cloud for crypto mining or other activities to generate funds.
The typical goal of threat actors is to generate revenue to fund other deceptive activities.
Key Features and Capabilities for CDR
These are the key features that security teams should be looking for are as follows:
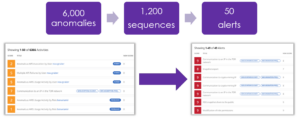
- Real alerts, or Realerts. If you ask any security team what their chief issue is – too many alerts. And it isn’t just too many alerts – it is too many alerts which are meaningless. According to a 2020 survey, 70% of security teams have seen security alerts more than double. Many security platforms narrowly scope their alerts so they don’t miss anything, however, this causes alert fatigue.The solution is to look for platforms that contextualize events, behaviors, and activities, so when an alert is presented to the security team it is a realert. Alerts are not typically a single event. Threat actors have been lying in wait, quietly moving around the cloud. A real alert will correlate all this information and provide the evidence to the security team so they understand that his is an actual threat and could become a breach if action isn’t taken. Skyhawk leverages generative AI to identify these threats up to 78% faster and to ensure accuracy in detection.
Sort through anomalies, to sequence events into alerts that are actually threatening your business.
- Automatic remediation, when appropriate. Security teams are notoriously understaffed. Automatically addressing security incidents can help alleviate the burden that security teams are already suffering as well as ensure a consistently executed resolution. Automation eliminates errors and accelerates the solution to the threat.
- Protect security team productivity. This aligns with the two points above. When security teams are overwhelmed with noisy alerts the security team cannot be productive. A true CDR platform will present only realerts which are threatening their environment so the security team does not waste their precious time chasing noise. Realerts mean security teams are working on real threats to their cloud. Additionally, automation ensures consistency in resolving specific issues and also enables security teams to focus on more complex threats where automatic remediation cannot be used.
- Agentless, runtime monitoring. It is critical to have a cloud native agentless solution. Maintaining and tracking agents puts an unnecessary management burden on already stressed security teams. Additionally, if the security solution is relying on agents, this means only information that the agents collect is used to locate security issues. Look for platforms that collect and analyze logs. This ensures a full view of the behaviors in the runtime to prevent cloud breaches.
- Ideally, part of a complete, cloud-native security platform. Finally, when trying to detect threats and prevent breaches, you want to have a solution that can support multiple cloud platforms (AWS, Azure, GCP, Kubernetes etc.). Most organizations are using multiple clouds and containers and have to learn a new way of securing the environment per cloud. A complete cloud security platform will also include other capabilities like managing the attack surface and posture of the cloud.