At Skyhawk, we have always known that CSPM, and even the next-gen of CSPM known as CNAPP, is not enough. In fact, by 2026, 50% of the attack surface will not be patchable, meaning CSPM/CNAPP solutions will not be effective. This is especially the case with cloud. Cloud surfaces are more difficult to patch as they need to be accessible to ensure access to data and applications. Additionally, businesses leverage the cloud as it is flexible and agile, keeping it secure as it changes is very challenging. So, you definitely need cloud threat detection and everyone understands that. However, you need threat detection that takes a proactive approach to prevent the breach, not threat detection that simply assists in incident (read breach) response.
Why CSPM is Not Enough
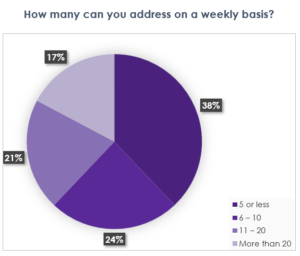
We have seen customers who have put their faith in CSPM get burned. They believed that if they achieve zero critical CNAPP alerts, or at least address most of them, they will be safe. There will be no breaches or issues. There are two issues with this. The first is closing out most of these alerts is an impossible goal. In a survey we conducted during a webinar with almost 100 attendees we found the following:
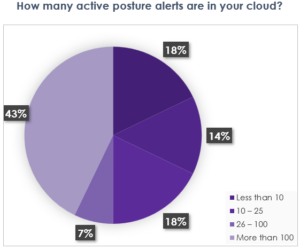
The second issue is, threat actors do not wait for you to address your alerts before they attack. One of our customers was using a very famous CNAPP platform before they were a customer estimated the work to address all their CNAPP alerts would take 5 engineers about 12 months to complete – and they learned the lesson the hard way that threat actors do not wait. Unfortunately, they found out on social media that their cloud was breached. They are now a customer.
Reactive versus Proactive: Skyhawk’s unique approach to cloud threat detection
The goal of CDR is to detect threats – hence threat detection – but you need to detect the incident before it becomes a breach. Some vendors are providing incident response, after the breach so you can investigate what happened, after the horses run out of the stable. This is fine – but don’t you want to prevent the breach altogether? This is what being proactive means.
Skyhawk Security’s Continuous Proactive Protection, an AI-based Autonomous Purple Team, finds the most pressing issues in your cloud and then prioritizes them based on the business value of the asset behind the security issue.
- Discovers the environment’s inventory, configuration and identifies the crown jewels
- Analyzes the least resistant paths to the crown jewels
- Simulate attacks against the environment to identify gaps in security
- Understand how your defenses respond to the attack
- Adapt your threat detection to ensure it is aligned to your cloud infrastructure
This completely AI-based approach does not take a break and continuously evaluates your security to ensure your organization can fully take advantage of the cloud. As your cloud architecture changes to meet your changing business requirements, Skyhawk Security updates your security to align to your cloud architecture.
It is the best solution for your cloud to prevent cloud breaches.
Industry Validation
What confirmation do we have that we are the best?
That is a pretty bold statement. So, how are we backing it up? We recently were awarded Cloud Security Innovator of the Year by the Cloud Awards. AND, we made it to finalist in all four categories that we submitted for: Cloud Security Innovator of the Year, Best Use of AI in a Cloud Security Solution, Best Security Compliance in Enterprise, and Best Vulnerability Scanner/Assessment Solution.
You can see the other finalists here, some were even mentioned above.
Here is the link to our press release for our win.
Check out Part 2 to learn how our AI-based Purple Team prevents cloud breaches with Simulation Twins, which helps surface security gaps, and design accurate auto-response and auto-remediation to prevent cloud breaches.