Skyhawk Security’s Preemptive Cloud Security Platform operationalizes Continuous Threat Exposure Management (CTEM) and covers key cloud use cases including Unified Vulnerability Management, Red Team-as-a-Service, and Cloud Threat Detection and Response (CDR).
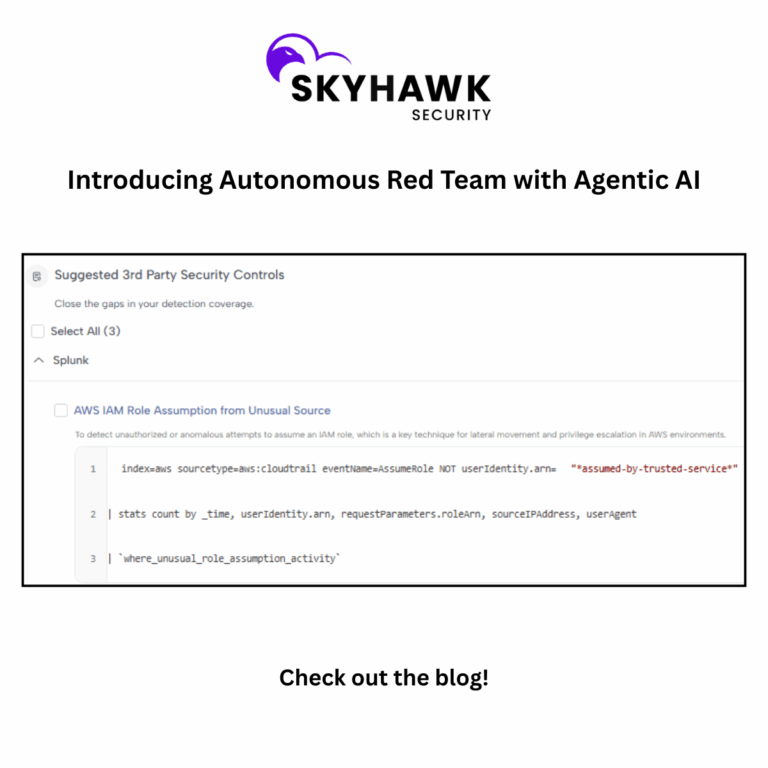
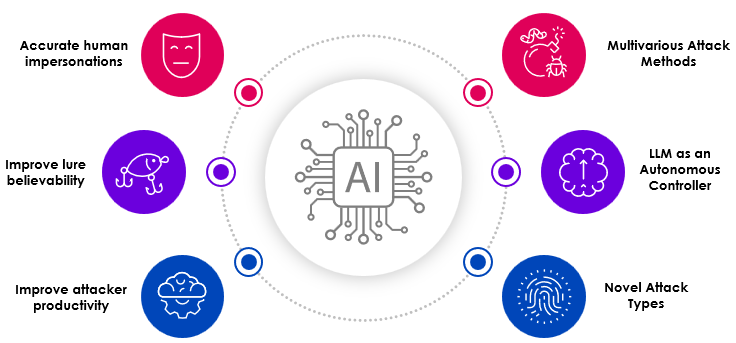
A key capability of Skyhawk Security which enables the use cases above is Autonomous Adversarial Emulation. Skyhawk executes customized attacks designed for your specific cloud architecture and security controls to find gaps in your security and validate your security controls. These customized attacks are created with an AI-based red team, aligning very well to Autonomous Adversarial Emulation (AAE).
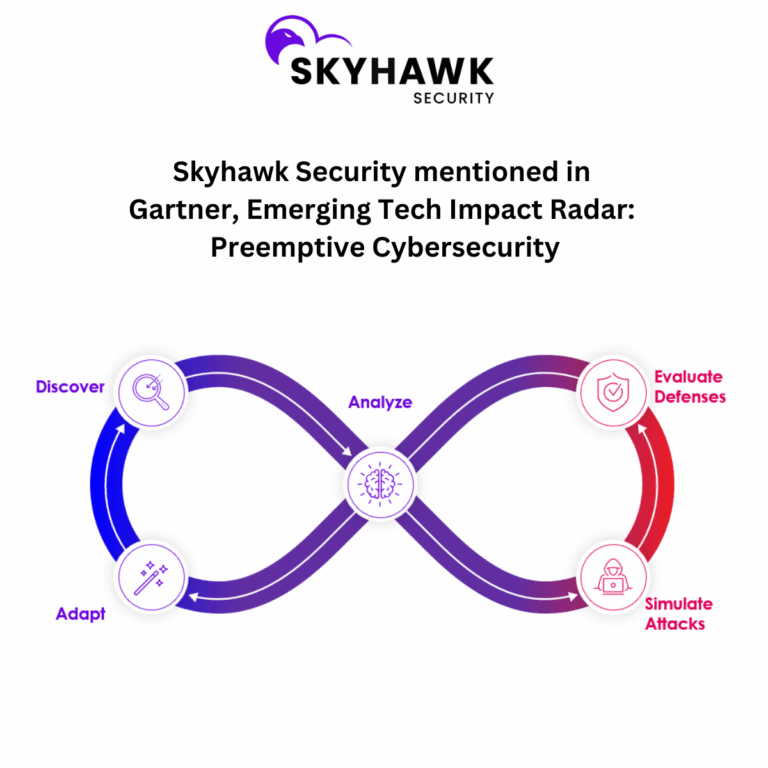
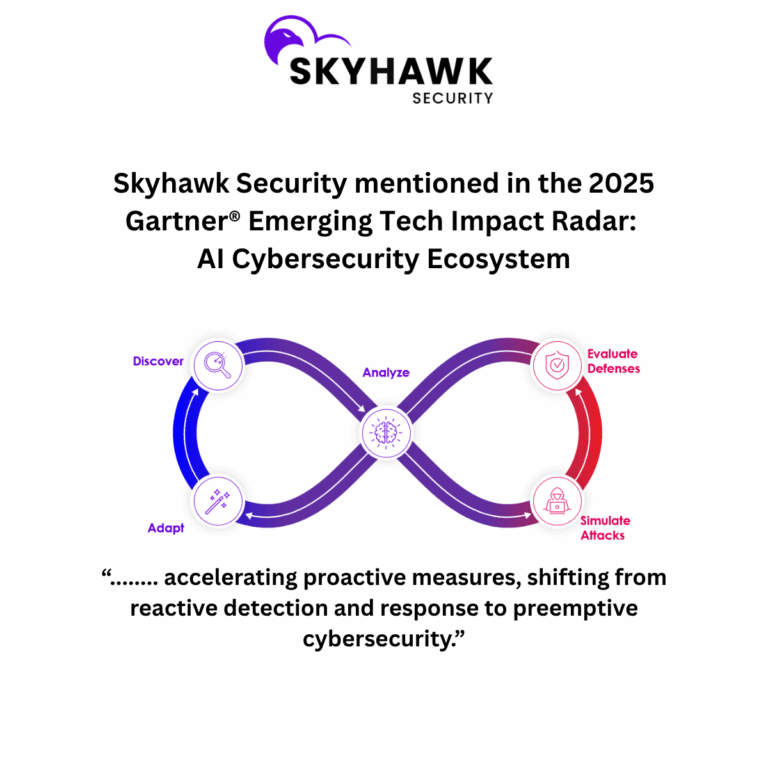
According to Gartner, “Autonomous adversarial emulation (AAE) combines predictive machine learning models with historical and simulated threat actor behavior to perform real-time emulation and simulation of cyberattacks. AAE employs generative models and may utilize AI agents that are context-aware to carry out specific tasks and objectives. These tasks include collecting evolving threat intelligence, identifying exploitable vulnerabilities within the environment, and autonomously creating and executing tailored attack playbooks. The ultimate goals are to demonstrate possible breaches and provide comprehensive guidance for preemptive attack resilience improvements.” The report also mentions, “Traditional cybersecurity based on a reactive detection and response approach is struggling against emerging AI threats and failing to keep pace in many cases. C-level executives must embrace a new preemptive strategy to neutralize threats before they can cause harm.”
Skyhawk Reduces Business Risk with Autonomous Adversarial Emulation
- Unified Vulnerability Management: Understand how vulnerabilities and posture findings can be used together to compromise business critical assets, so security teams focus on cloud risk reduction.
- Non-disruptive Red Team-as-a-Service: Validate security controls and confirm where your security controls are vulnerable so adjustments can be made to reduce business risk.
- Operationalize Continuous Threat Exposure Management: Operationalize continuous threat exposure management (CTEM) to prioritize threats, exposure, vulnerabilities, and other cloud security findings, to ensure what the security team addresses, reduces cloud risk.
- Cloud Threat Detection: Security teams waste no time on incident candidates; Skyhawk identifies threats in real-time so they can be immediately resolved to prevent a breach.
We can prove it.
We have a 30-day free trial. We can get you onboard in minutes and then you can see the value for yourself.
Book a meeting with us at re:Invent!
If you don’t know where to start with your preemptive cybersecurity strategy, try Skyhawk Security for free – sign up today!
Gartner subscribers can read the full report at www.gartner.com.
Gartner, Emerging Tech Impact Radar: Preemptive Cybersecurity, by Emerging Tech and Trends Security Research Team, Published October 7, 2025.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.