Infrastructure-as-Code is a game-changer for automating cloud resource management – and it’s as popular as ever. AWS quickly got a piece of the pie by launching AWS CloudFormations, a tool that lets you model, manage and provision your AWS cloud resources by leveraging Infrastructure as Code.
If that wasn’t enough – AWS also launched AWS Security Groups to provide additional visibility and protection into your resources. That is handy for organizations as, according to a recent study, 89% of organizations aren’t confident in their ability to protect sensitive data in the cloud.
However, regrettably, you can’t outsource security and call it a day. You still need to properly configure your AWS Security Groups to ensure they are working for you and not making security any more complex than it needs to be. This article discusses seven essential steps to configure AWS Security Groups, including an overview of how AWS Security Groups rules work.
An overview of AWS Security Groups
AWS Security Groups are a crucial component of securing your AWS infrastructure and provide granular control over your cloud resources’ network traffic, allowing you to specify which traffic is allowed and which is not. This enables you to enhance your AWS cloud security by restricting unauthorized access and reducing the blast radius of potential attacks.
Several other benefits include:
- increased visibility into your resources
- simplified configuration and management
- the ability to comply with industry standards and regulations
By leveraging AWS Security Groups as part of your overall security strategy, you can help ensure the protection and compliance of your cloud infrastructure.
AWS Security Groups rules
AWS Security Group rules are critical in this security framework, ensuring that your network traffic flows only between trusted sources and destinations and that malicious activity is blocked. They are instructions that dictate how traffic is allowed or blocked within a Security Group and can be configured for both inbound and outbound traffic. By default, all traffic is denied unless a rule explicitly allows it.
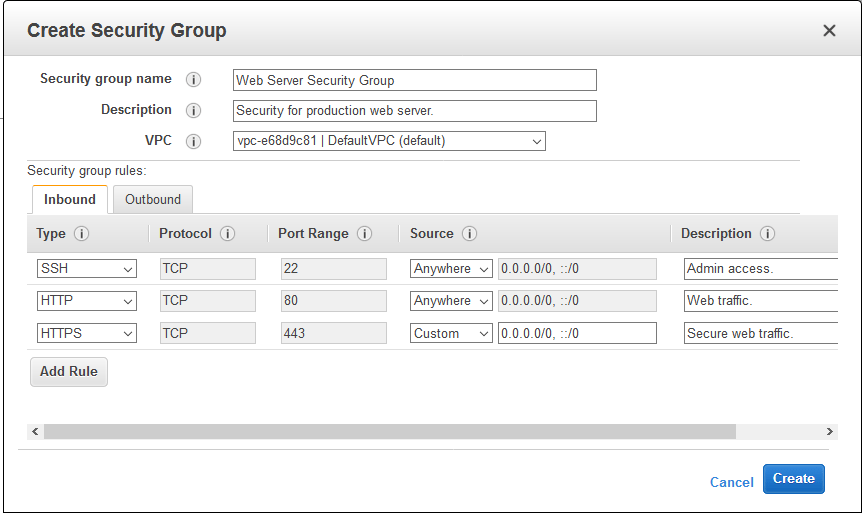
The information included in a Security Group Rule consists of the type of traffic being allowed (e.g., SSH, HTTP, or HTTPS), the protocol used for the traffic (e.g., TCP or UDP), the port range for the traffic (e.g., 80 for HTTP traffic), and the source/destination IP address, CIDR block, or Security Group ID for the traffic source or destination. Having this level of granularity in Security Group Rules goes a long way in maintaining security and compliance in your cloud infrastructure.
7 Essential steps to configure AWS Security Groups
1. Edit inbound and outbound rules
AWS Security Groups allow you to edit your inbound and outbound rules to control traffic in and out of your EC2 instances. All inbound traffic is blocked by default, while all outbound traffic is allowed. You can create custom inbound and outbound rules to open specific ports, protocols, and IP ranges for traffic that needs to flow in and out of your instances. By editing these rules, you can ensure that your EC2 instances only communicate with authorized sources and are protected from potential threats.
Follow the steps below to modify inbound and outbound rules:
- Head to the Security Groups section in the EC2 console and select the Security Group you wish to change.
- From there, access the “Inbound Rules” or “Outbound Rules” tab, and click the “Edit” button.
- Apply any necessary changes to the rules and hit “Save” to apply them to your Security Group.
Remember to regularly review and update your Security Group rules to ensure they align with your security policies and protect your instances effectively. Additionally, follow the principle of least privilege and only permit essential traffic for better security.
2. Tag your security groups
You can add up to 50 tags per security group, each containing a key and value that describes a specific attribute or property. By tagging your security groups, you can identify and filter them based on their purpose, environment, or management team. You can also use them for cost allocation, resource tracking policies, and searching for specific security groups in the AWS Management Console or CLI.
Follow the steps below to tag your AWS security groups:
- Navigate to the EC2 dashboard and select Security Groups.
- Then choose the group to tag, and click Edit.
- Go to the Tags tab, and click Add/Edit Tags.
As a best practice, use consistent naming conventions and base the tags on the group’s function. Be mindful not to over-tag, as it can make management difficult. Also, avoid using special characters or spaces in your tag keys or values.
3. Tag your security group rules
Properly tagging your security group rules is crucial for simplifying the management process and identifying specific rules quickly. For this, navigate to the “Inbound Rules” or “Outbound Rules” tab in the Security Groups section of your EC2 dashboard, and add tags to your desired security group rules by selecting the “Edit” option and scrolling down to the “Tags” section.
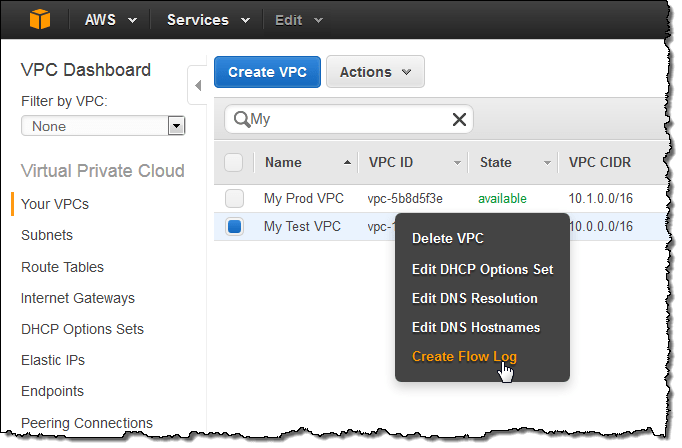
4. Enable AWS VPC Flow Logs
Enabling AWS VPC Flow Logs is crucial to securing your AWS infrastructure. It captures vital information about IP traffic, including source and destination IP addresses, ports, protocol, bytes, and packets transferred.
To enable it, here’s what you have to do:
- Create an S3 bucket to store the logs.
- Create a VPC Flow Logs resource.
- Specify the VPC and traffic type, and configure the log settings.
Flow Logs provide visibility into network traffic, helping you monitor network performance, detect issues, and improve security. However, they can generate significant data, so you must plan for storage and analysis accordingly.
5. Don’t use large port ranges
Avoid using large port ranges when configuring Security Groups. Instead, specify individual ports or smaller ranges of ports for each rule. This approach can help reduce the risk of unauthorized access to your resources by minimizing the attack surface.
Large port ranges can expose your resources to potential attackers, as a single rule allowing traffic from any source IP address to any destination IP address over a wide range of ports (e.g., 0-65535) could be exploited. Limiting rules to only the necessary ports for your application can significantly reduce the likelihood of such attacks.
6. Add descriptions to groups and rules
Including clear and detailed descriptions is critical when creating security groups and rules. Descriptions help your team understand each group’s purpose and rule’s nuances, enabling easier management and ensuring compliance with regulations.
Adding descriptions is simple – you can include them when initially creating the security group or rule or edit them later. Investing time in crafting helpful designations will save time in the long run by improving the efficiency and accuracy of your team’s security management.
7. Restrict permissions to the IAM console
It’s essential to restrict permissions to only necessary users and services to reduce the likelihood of unauthorized access to your AWS resources. One effective way to achieve this is by utilizing AWS Identity and Access Management (IAM) to create specific policies that define the permissions granted to each user or service.
Furthermore, IAM can simplify access management at scale by enabling the creation of groups with pre-defined permission sets. By enforcing permission restrictions specifically to the IAM console, you can significantly minimize the risk of data breaches or other security incidents resulting from unauthorized access.
Is AWS Security really enough?
Cloud providers operate under a Shared Responsibility Model. While they are responsible for securing their underlying infrastructure and services, customers are responsible for protecting their data, applications, and identities. However, many businesses may not fully understand the extent of their responsibility, which can lead to significant security gaps.
One of the most significant gaps is in securing accounts and identities. AWS offers robust identity and access management (IAM) services, but it’s up to customers to ensure that only authorized users and applications can access their resources. Large organizations with numerous employees, contractors, and partners requiring access to different infrastructure parts may find this particularly challenging.
Beyond AWS Security Groups: strengthening your cloud security
AWS security groups are a valuable tool but not a complete solution, so you must take a proactive approach to security to avoid getting caught in an attacker’s web. Skyhawk Security offers comprehensive cloud security, including activity monitoring, entitlement management, and real-time detection and remediation of alerts. With it, you can have peace of mind knowing your entire infrastructure is covered.
The best part? Skyhawk offers FREE Cloud Security Posture Management (CSPM) to detect misconfigurations and manage compliance and governance for up to 1000 assets. Request a demo and get your free CSPM today.