Cybersecurity has always been a game of cat and mouse between cyber criminals and information security teams in organizations. Though it isn’t always clear who the cat and the mouse are in this scenario. As infosec professionals, are we doing the chasing or the escaping? Perhaps a bit of both?
In 2023, we are faced with an onslaught of increasingly sophisticated organized cybercrime gangs and a distressing shortage in cybersecurity skills across industries. Add to that the ever-growing attack surface of cloud assets and applications and the dependence of businesses on access to their online resources, and you have yourself a very expensive perfect storm brewing.
More than ever, businesses today are forced to take preventative action to avoid falling victim to professional cybercrime gangs. Gangs that are actively looking to exploit every vulnerability, flaw, and misconfiguration in your cloud services and applications. This article explores critical Threat Detection and Response methods you can use to detect and mitigate risks successfully.
What is Threat Detection and Response (TDR)?
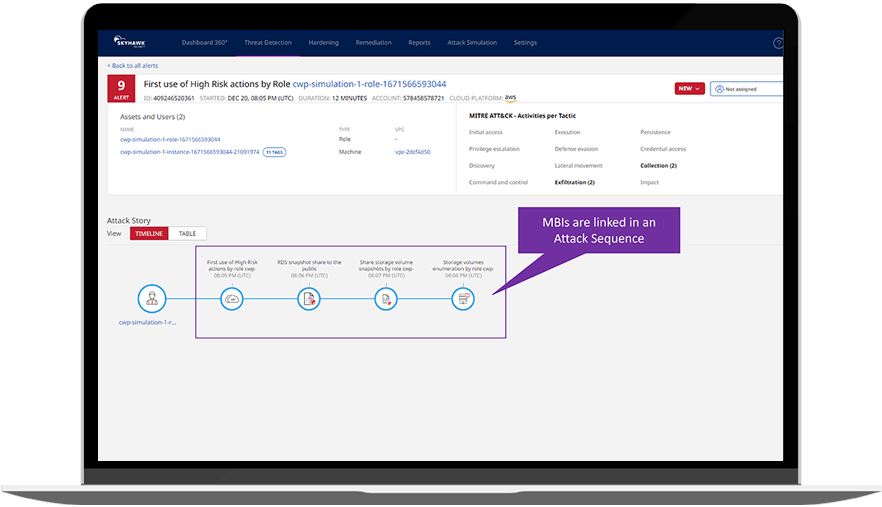
Threat detection is the proactive investigation of potential risks to an organization’s systems. Once detected, the threats are analyzed and responded to accordingly. The reason that detection and response are unified under one term is apparent: once your team detects and assesses threats, it must address them immediately in one way or another. However, this must be a real threat, not a one-off event or false positive. Chasing false positives is a significant problem for organizations, resulting in poorly distributed resources and time wastes. Skyhawk notifies you only when there is a real alert.
TDR tactics and tools aim to proactively prevent attacks on digital business assets rather than respond to attacks after they have been launched. Aided by automation and AI/ML-powered tools, TDR often entails continuous monitoring for threats through log scanning, user and system behavior analysis, and then the implementation of measures to prevent the uncovered threats from turning into vectors in an attack.
What risks does Threat Detection and Response cover?
Companies’ defensive technologies mitigate the majority of known vulnerabilities and risks. However, these technologies and solutions protect against known threats to commonly employed technologies, services, and frameworks. When it comes to unknown dangers that may be specific to an organization or stemming from malicious insiders, TDR solutions are crucial to discovering and neutralizing potential cyber threats.
The list is ever-evolving as malefactors find new ways to overcome defenses and exploit misconfiguration errors. This is especially true in cloud computing and cloud security posture management. Detecting threats in complex cloud environments is challenging. The potential attack surface is broader, making it increasingly difficult to maintain complete visibility into cloud assets, applications, and services.
The speed at which threats become attacks makes it almost impossible to list and categorize all the risks and threats addressed by TDR. However, some notable examples today include:
- Advanced Persistent Threats (APTs)
- Insider threats
- Zero-day threats
- Spear-Phishing
- Mixed threats
Why you need to employ efficient threat detection and response methods
Early detection and risk reduction
First and foremost, TDR tools and methods enable organizations to detect security threats early. Discovering and addressing threats before they become attack vectors can significantly reduce incidents’ likelihood, impact, and cost.
Automation and efficiency
Threat and response tools can automate many manual tasks like log analysis. They can also employ AI/ML capabilities to lighten the workload on SOC and information security teams by performing analysis of user and service behavior patterns in runtime. You can also offload some of the research work to global security experts by adopting frameworks such as MITRE ATT&CK to gain access to examples of adversaries’ behaviors and TTPs (tactics, techniques, and procedures).
Visibility and compliance
TDR tools and methods grant organizations visibility into the security posture of their applications, data stores, on-premises/cloud assets, distribution, and usage of permissions. Complete visibility doesn’t only enable infosec professionals to identify potential threats faster and respond more effectively. It also helps organizations meet regulatory requirements for data protection and privacy (like HIPAA, PCI-DSS, and GDPR).
5 Threat Detection and Response methods baffling cyber attackers
As noted in the introduction to this article, cybersecurity is a cat-and-mouse game. Becoming the cat in this hunt entails out-thinking the many mice interested in your cheese. It would be unwise of you to underestimate the ingenuity and persistence of well-organized hungry mice.
Regarding proactive approaches to threat detection and response in a cloud-native environment, some methods are more likely than others to surprise your adversaries and, ideally, deter them from attempting to launch an attack against your digital assets.
1. Behavior Analytics
Attackers don’t usually think they’re being watched. This allows you to leverage AI/ML to process immense amounts of behavioral data collected in real-time across cloud assets, employee accounts, and endpoints and use it to flag suspicious behaviors that merit alerting your security teams.
2. Intruder traps
Creating a gated and tempting playground for attackers is an effective way to understand the risks you face and where they are coming from. Intruder traps and honeypots do precisely that: life-like systems are intentionally compromised to lure attackers into exploring vulnerabilities. They can deflect attackers’ attention from the actual system and simultaneously study attackers’ journeys to analyze the attack and mitigate future risks.
3. Threat Intelligence
With the data you’ve gathered from your traps and honeypots, as well as public threat intelligence feeds, you can predict (at least to some extent) the behavior of future attackers. Unlike behavior analytics, which strives to classify behavior as malicious or legitimate, threat intelligence employs AI/ML to gain actionable insights from masses of logs, flags, and alerts.
4. Threat Hunting
You don’t expect the adversaries to do all the work for you, do you? Threat intelligence is not always enough. Sometimes you need to get aggressive and not just proactive in seeking out hidden vulnerabilities and misconfigurations in your business cloud assets, user permissions, virtual networks, data stores, and applications.
It may feel like going out looking for trouble. Still, with the aid of automated tools and a predefined response and remediation plan, you’ll be able to find the gaps before malefactors do and fix them promptly.
5. Threat alert optimization
Infosec and SOC teams are understaffed, swamped, and burning out fast, and cybercriminals know it. Furthermore, they seek to exploit alert fatigue and “cry wolf” to conceal their malicious activities.
Generating floods of false positives to confuse your defenses and exhaust your teams is not an innovative tactic. However, today it can be circumvented with alert optimization in your threat detection and response strategy. But that’s not the only reason to employ threat alert optimization.
Skyhawk’s Synthesis Security Platform offers an agentless multi-cloud solution that leverages ML and three layers of context to correlate all attack vectors in real time. A passive listening tool that classifies activities to determine a baseline for normal user behavior doesn’t only lighten the load on your security operations teams. It also paints a complete picture of your business data and cloud security posture when combined with threat intelligence and threat hunting in your TDR strategy.
Fix Threat Detection and Response with Skyhawk
Half of security engineers and practitioners say that half of the alerts they receive are false positives, and roughly as many have seen the number of daily alerts they receive triple. For cybercriminals, this presents an opportunity to penetrate systems unnoticed while your SOC dismisses yet another failed user login alert.
Effective and efficient threat detection and response require accuracy and speed that are impossible to achieve without employing intelligent automation tools. With Skyhawk, you can rest assured that your teams are dealing with accurate alerts and incidents across your cloud and applications. Request a demo and get Cloud Security Posture Management 100% free.