In recent months, the debate over agentless vs. agent (or sensor-based) cloud security has witnessed an amplified discussion.
According to Forbes, an update of the Falcon Sensor from CrowdStrike causes an endless loop of bluescreens on Microsoft systems. This agent incident impacted businesses across the globe, have experienced unprecedented system downtimes, affecting critical sectors such as airports and hospitals.
In the past decade, the cloud has become a critical component of every organization and while on-premises deployments were dependent on agent-based technologies, the cloud enabled an agentless approach, providing near real-time detection by consuming cloud telemetries and logs.
The CrowdStrike incident underscores the agent vs. agentless debate for Cloud Threat Detection and Response (CTDR).
Some vendors might tell you that their sensors are not introducing kernel risk but most of the agent downsides are still applicable to their agent (eBPF) based solutions.
The Downside of Agent-Based Security Solutions
- Operational complexity: Like any part of the infrastructure, whether physical or virtual, agents require updates and maintenance to ensure they function properly. This requires resources and time – something many security teams are lacking. Today’s incident shows the operational risk of relying on agent-based CTDR.
- Resource consumption: Agents require system resources to run and must be kept to a minimal footprint. The resources that agents consume mean higher cost on the customer side, in memory and CPU profiles on the machines, or potentially slowing down critical applications, services, and business projects.
- Point of Failure: The drawback is what the world is experiencing today – agents introduce another point of failure. Updates and other changes to these points in the infrastructure can cause serious issues.
- Services that cannot be protected with agents: In the cloud, many services are managed by the cloud vendor, thus you cannot install an agent – making the agentless approach the only one applicable. Agents are simply not relevant in these cases and agent-based solutions will be blind to managed services (Databases, FaaS Managed Kubernetes), with cloud native threat detection being the only alternative.
- Agent enforcement risk: One of the core challenges in cloud threat detection and response is the response part. While agents include enforcement capabilities, they introduce a risk of enforcement being unpredictable and may also introduce supply chain risk if fallen into the wrong hands.
The Skyhawk Security Difference: Agentless Solutions
At Skyhawk, our approach was that CIOs and CISOs look on ways to reduce the number of agents they have and do not need more. We therefore advocate for an agentless approach to CTDR, which eliminates the complexities and vulnerabilities associated with agents, while maintaining robust security capabilities. Skyhawk Synthesis Security Platform offers a proactive approach to your cloud security for the very first time, while simplifying management and operations.
- Ease of deployment and management: Agentless solutions are easier to deploy and manage. They leverage existing infrastructure and require minimal configuration, reducing the operational burden on IT teams. Without the need for continuous updates and maintenance, organizations can focus on core security objectives rather than managing agent-related issues.
- Holistic incident level observability at cloud run-rime: Agentless solutions offer comprehensive visibility into cloud environments without requiring context input unique to agent-based systems. By integrating with cloud-native services and utilizing API-based monitoring, these solutions provide real-time insights into potential threats and incidents.
- No impact on detection capabilities: Contrary to the belief that agents are essential for effective threat detection, agentless solutions can achieve comparable, if not superior detection capabilities. By analyzing cloud telemetries and logs such as network traffic, Audit logs, DNS logs and more, agentless CTDR can identify and respond to threats with precision and speed.
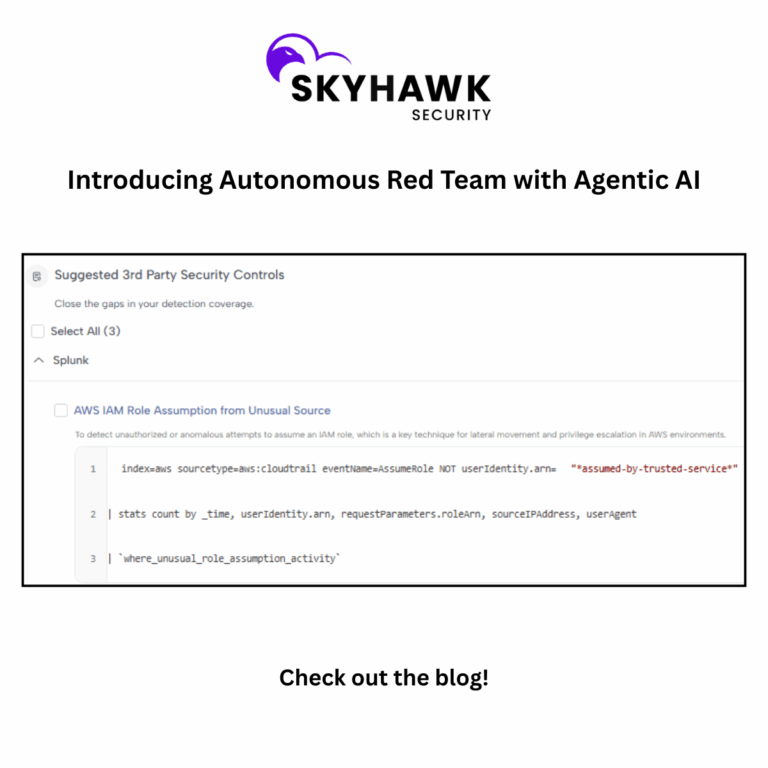
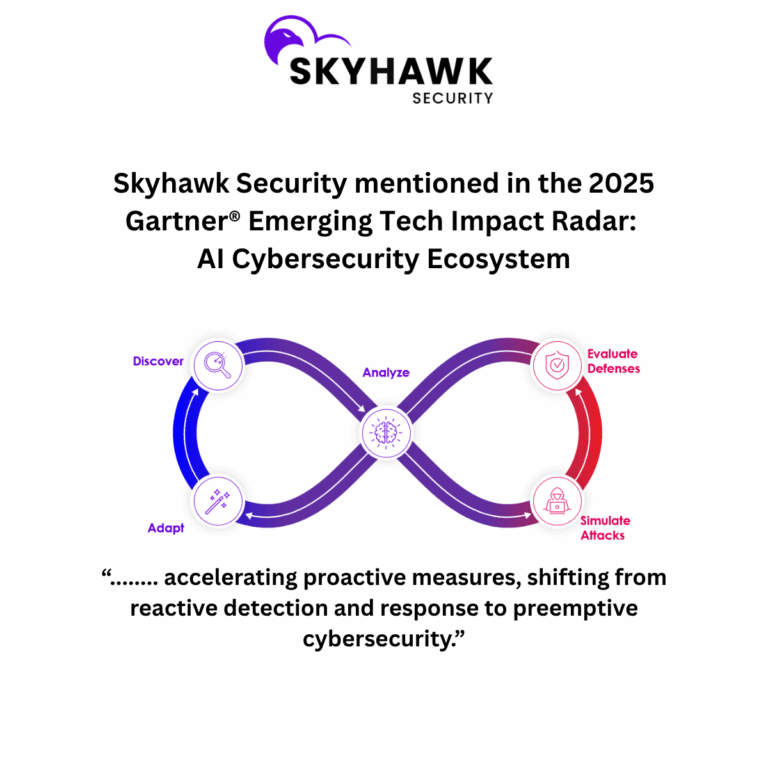
- Proactive detection, verified and secure enforcement: Skyhawk Security’s Autonomous Purple Team exemplifies proactive detection and verified response by simulating proven weaponized attack scenarios tailored specifically for customers’ cloud footprints and running them against Skyhawk’s CDR. This proactive approach ensures that security measures are continuously tested, evaluated, and optimized, and that enforcement through automated response is done without the overhead, limitations, and risks of agents. Furthermore, it helps cut through all the misconfigurations and vulnerabilities alert noise by pinpointing critical assets which are proven to be weaponized-ready, focusing the remediation effort on where it is most necessary and effective, while preserving business continuity.
- Protect against AI-based attacks: Skyhawk’s AI-based Autonomous Purple team delivers a superior measure of strength to customers, in a world where Gen-AI creates weaponized risks at higher volume and velocity.
Skyhawk’s Cloud Threat Detection and Response (CDR), leverages a multi-layer AI-based approach to identify and stop cloud threats before they become breaches. The AI-based Autonomous Purple Team analyzes your overall cloud security and identifies weaknesses, and then prioritizes them by the business value of the asset behind the weakness.
The recent CrowdStrike incident serves as a stark reminder of the risks associated with agent-based CTDR solutions. Skyhawk Security’s agentless approach offers a compelling alternative, simplifying operations while maintaining robust security. As the cybersecurity landscape evolves, embracing agentless solutions can help organizations achieve resilient and effective threat detection and response without the operational overhead and vulnerabilities of agents.
Now is a good time to discuss how agentless solutions like ours can prevent similar disruptions. Contact us today.
No one escaped this issue, here are some additional articles which highlight how far-reaching this issue is:
- CISA
- Major US Hospitals
- NHS
- Olympics
- Transportation impacts: According this to this article, 28,000 flights have been cancelled and/or delayed, and counting.
- Banking