The sky’s the limit for cloud computing. As new cloud-native applications like containers, microservices, and APIs grow in popularity, the cloud’s scalability and adaptability make it attractive for businesses. Emerging technologies such as generative AI and Web3, which require powerful computing capabilities, are also bringing the cloud’s growth to a whole new level.
While the cloud is generally safe, the more companies rely on it, the more attractive it becomes for cybercriminals. Almost 27% of businesses experienced a security breach in their public cloud infrastructure over the past year, with nearly a quarter of these breaches resulting from their cloud infrastructure’s security misconfigurations.
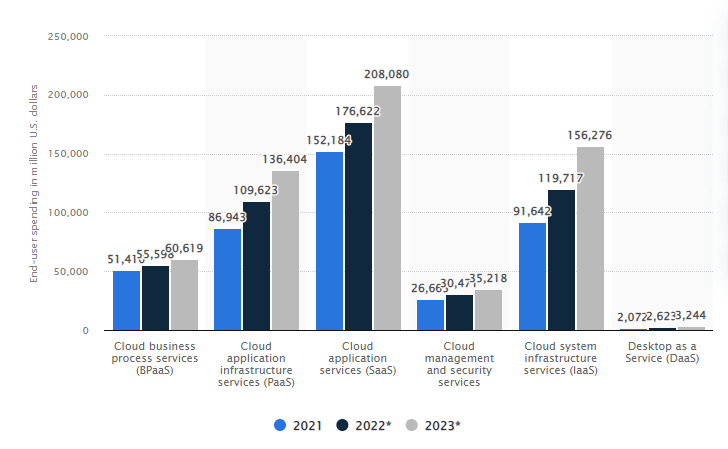
Growth in Global Public Cloud Services 2021-2023
Cloud Detection and Response (CDR) is a relatively new approach to cloud security that enables businesses to identify and remediate cloud attacks in real time. This article takes you through the ins and outs of CDR, including some best practices for implementing a successful CDR framework.
A complete overview of Cloud Detection and Response (CDR)
The CDR framework is a set of processes organizations apply to safeguard their cloud from security incidents in SaaS, PasS, and IaaS applications. It serves SMBs and large enterprises, but the approach differs depending on the organization’s size.
Large organizations with security operations centers (SOCs) or incident response (IR) teams use one of two CDR frameworks:
- MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) – A globally accessible knowledge base of tactics that attackers use in their campaigns. Its cloud matrix includes cloud-based techniques for the primary cloud service providers (CSPs).
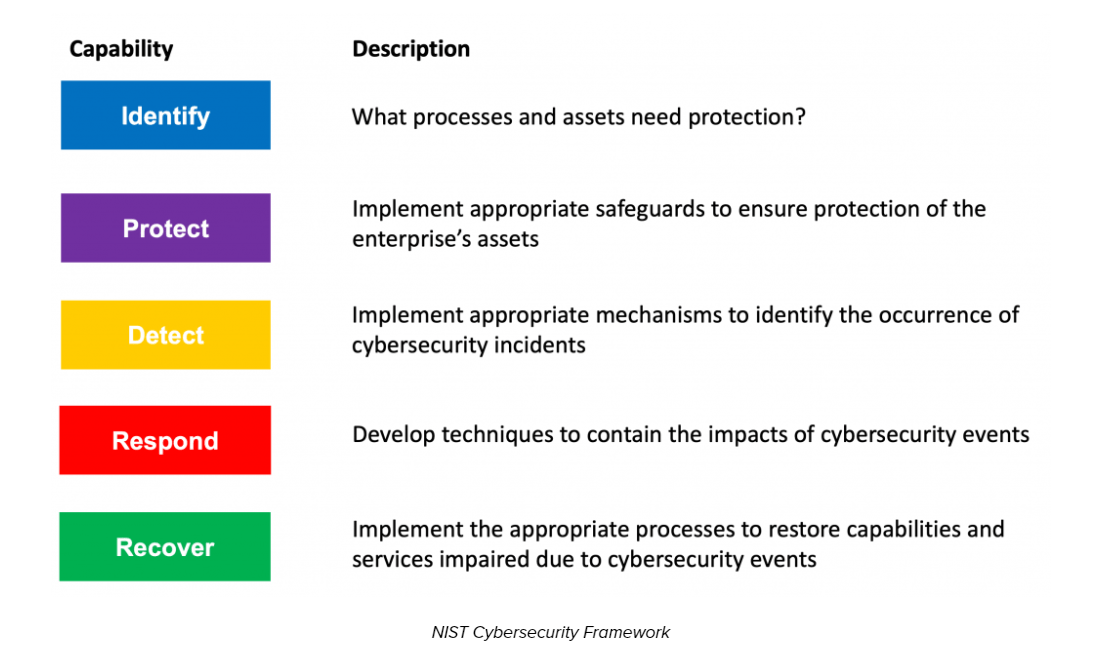
- NIST CSF (National Institute of Standards and Technology) – A voluntary framework that provides guidelines and standards for organizations across industries, categorizing all activity into five core functions.
The NIST Cybersecurity Framework – 5 Core Functions
SMBs often rely on their in-house security team or outsource CDR to an external group such as managed detection and response (MDR).
Why you need a Cloud Detection and Response (CDR) framework
As organizations migrate to the cloud, traditional EDR, NDR, and XDR security solutions have proven unadaptable. Not only have CDR frameworks proven to deliver complete visibility into cloud data and assets, but they also provide enterprises with prioritized alerts to distinguish between actual security incidents and merely abnormal user behavior.
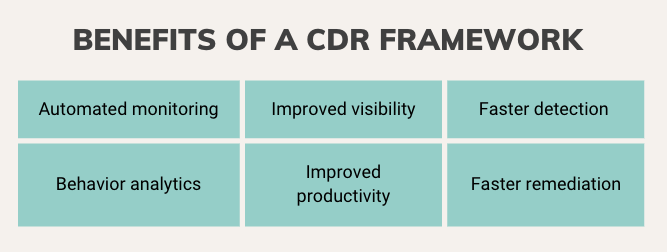
CDR frameworks deliver many benefits to organizations:
- Automated monitoring. Manually monitoring threats is impossible as risks evolve and organizations scale, storing applications, programs, and data across many CSPs.
- Improved visibility. Organizations must see the dangers and threats in all cloud layers, from the infrastructure, operating, and application levels to the identity, API, and data levels.
- Faster detection (almost real-time). Continuous monitoring of network traffic and workload events and prioritized alerts allow for near real-time detection of security risks resulting from misconfigurations in systems or applications.
- Behavior analytics. CDRs can manage and process the data produced in the cloud using machine learning models to detect abnormal behavior or suspicious activities that could indicate a breach. For example, it can alert your SOC team when excessive privilege has been granted in your IAM solution or unauthorized changes have been made to your cloud configuration.
- Improved productivity of SOC teams. As a CDR framework is integrated into an organization’s security team, it enables SOC and IR teams to adopt automated systems such as SIEM, SOARs, and ticketing systems.
- Faster remediation. Adopting these automated systems improves productivity, workflows, and remediation time, minimizing the damage incurred from a data breach or attack.
Challenges of implementing Cloud Detection and Response Framework (CDR)
With all these benefits, CDRs still present some challenges. For example, they are difficult to implement in multi-cloud environments, a critical aspect to consider, as 90% of organizations have a multi-cloud strategy. Plus, organizations must find a solution that will scale on demand as their business scales. Lastly, security teams need better visibility into the permissions used, how a configuration exposes their assets, and how threat actors access them.
7 Best Practices for a Cloud Detection and Response Framework
1. Have a well-defined security strategy
An effective security strategy includes both identifying the threats that your organization needs to defend against as well as any tools that could assist it in doing so. The threats and the proper tools necessary to detect and respond to them should be reviewed continuously. Your organization should also evaluate your security team’s readiness regarding the tools, techniques, and skills it possesses in the event of an attack.
2. Understand your responsibilities
Cloud services operate based on the Shared Responsibility model. That means all customers – whether SaaS, PaaS, or IaaS – are responsible for data security, access, and compliance. At the same time, CSPs are responsible for physical security, virtualization layers, network controls, and other areas they control.
3. Apply the principle of zero trust
The Zero Trust approach enables organizations to improve security by allowing employees to work when, where, and how they want. It does this by verifying and securing every identity and enforcing the least privilege.
Unfortunately, many cloud administrators grant users excessive permissions to increase productivity. Cloud Infrastructure and Entitlement Management (CIEM) manages overused and unused privileges, operating on the concept of POLP, or the Principle of Least Privilege, an extension of the Zero Trust principle. With POLP, users have access to only what they need and only for the time that they need it.
4. Test incident response
If you have never experienced an incident, how do you know if you’re prepared to resolve it in the best way possible? Not only must organizations have an IRP plan in place in the event of a security incident, but they must test it regularly to make sure it is aligned with evolving business, compliance, and regulatory requirements and is suitable for both on-premises and cloud environments.
5. Achieve deep visibility of your cloud
With multiple security solutions in different parts of the cloud, organizations lack visibility into risks and threats posed, such as misconfigurations, excessive permissions, and how threat actors may be able to access an asset.
Skyhawk Security delivers complete visibility through its Runtime Hub, an ongoing analysis of the users’ behaviors in the cloud to differentiate between normal and suspicious behaviors. Through AI and machine learning, it analyzes, sequences, and scores individual events, correlating multiple events into a single storyline to detect real alerts only.
6. Develop workflow integrations
Integrating solutions such as SIEMs, SOARs, and ticketing systems and incorporating CDR solutions into this workflow assist SOC and IR teams in effectively automating and increasing productivity and improving remediation time. Security teams will also benefit by incorporating automated alerts into their activities.
7. Share your security policies with all relevant stakeholders
If only your IT department is aware of your security policy, how will your SOC and cloud infrastructure team know what to do in the event of an attack? It’s not enough to develop a security policy within your organization; you must also document your security processes so they can be shared across your organization.
Level up your cloud security with a robust CDR framework
By combining all of the elements of a robust CDR framework with these best practices, you’ll be able to gain a better picture of the actual threats your organization can remediate. Tools like Skyhawk can assist your organization with all the heavy lifting so that you gain runtime visibility, automated monitoring, detection in almost real-time, faster remediation, and improved productivity to go a step beyond simply enhancing your organization’s security posture.
Want to learn more about how Skyhawk can help you develop a CDR framework for your organization? Get a demo today!