For Cybersecurity Month, you can try Skyhawk for free!
In honor of Cybersecurity month, Skyhawk Security is offering a free 30-day subscription to the complete platform. Why try Skyhawk Security? Your Security and Development teams are overwhelmed with the number of CNAPP findings. There is a constant argument between security and development regarding what is a true finding vs a false one. This puts […]
The Rationale behind Autonomous Purple Team Technology
When Skyhawk set out to develop a new cloud security solution it was already clear that traditional security paradigms were not appropriate for cloud environments. Traditional security was built to secure on-premises environment. These environments were protected by numerous security means (firewall, sandbox) and malicious software was introduced by USB drives, email or clicking on […]
How the cloud amplified supply chain risk and what you can do about it?

As seen from recent security incidents involving cloud-based systems (for instance- numerous cyber incidents in the healthcare sector), reliance on cloud services can amplify cybersecurity risks associated with third parties and the supply chain. For example, some organizations allowed external contractors access to their Snowflake accounts for customization. Some contractors had very lax security posture […]
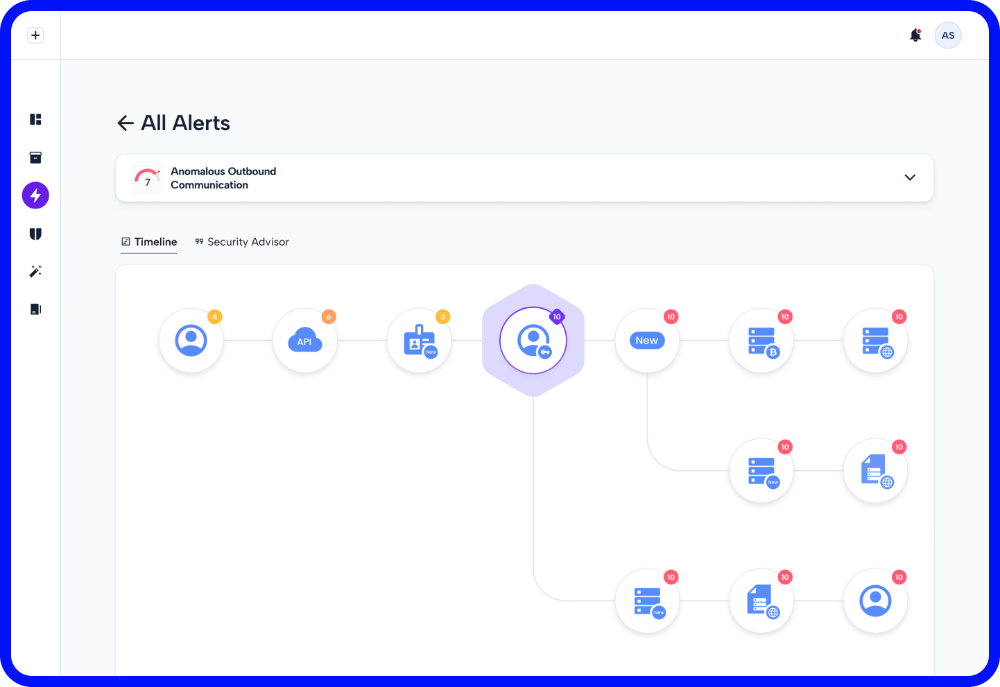
Continuous Threat Exposure Management (CTEM) versus Traditional Vulnerability Management
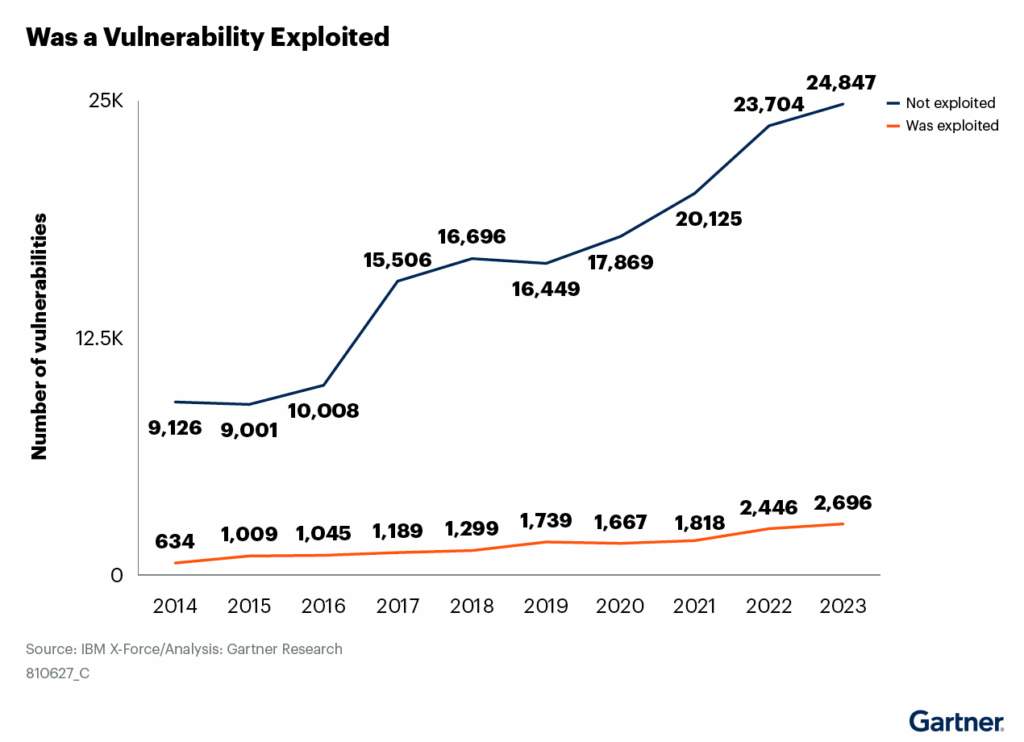
With the exploitation of vulnerabilities on the rise, many organizations are evaluating vulnerability management solutions. However, vulnerability management provides only a partial picture of what is happening in the environment. Organizations need to take a more comprehensive approach, looking not just at the vulnerability, but the exploitability of the vulnerability, and the business value of […]
The Top 10 Questions on Continuous Threat Exposure Management (CTEM)
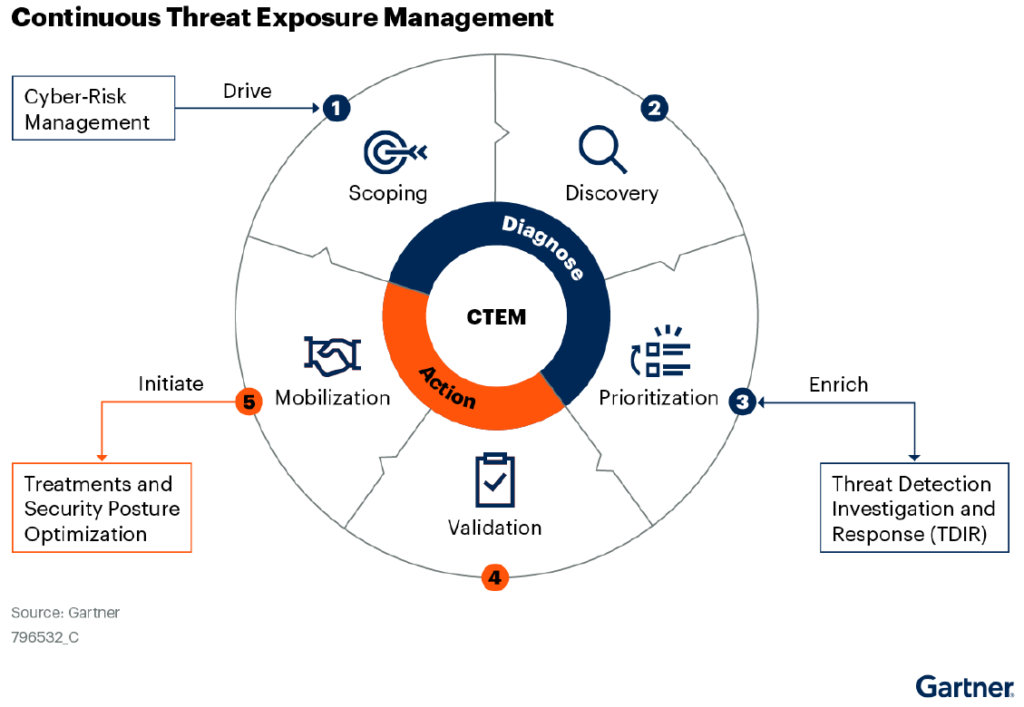
Cloud security teams are evolving their security approach, going beyond alerts and looking at the threat exposure with a business context. This enables the cloud security team to prioritize security gaps based on the value of the asset behind it. It also makes it easier for the CISO to clearly communicate what the threat exposure […]
That’s a wrap on another Blackhat

Blackhat 2024 wrapped up last week and we had quite a show! We advanced our Purple Team, creating a new asset for our partners to advance their sales and spread the news on Skyhawk, discussed our automated response capabilities with prospects, which is a clear differentiator, and had great conversations at the booth! Free Purple […]
Verified Automated Response eases the Burden of the SOC

Today’s security team is overwhelmed with alerts. On average, the SOC has 4,500 daily alerts. These need to be resolved fast and at machine speed. SOC, DevSecOps, DevOps, and Cloud Security teams cannot manually address all these alerts, automation needs to be used to effectively manage the threat exposure, but how can you trust the […]
Agent versus Agentless Cloud Security: Learnings from the CrowdStrike Sensor Failure

In recent months, the debate over agentless vs. agent (or sensor-based) cloud security has witnessed an amplified discussion. According to Forbes, an update of the Falcon Sensor from CrowdStrike causes an endless loop of bluescreens on Microsoft systems. This agent incident impacted businesses across the globe, have experienced unprecedented system downtimes, affecting critical sectors such […]
Want to be a CISO? We can help.

At the RSA conference there was a CISO panel, talking about the perils of becoming a CISO. Joe Sullivan, the CISO of Uber who just avoided jail time but did have to pay a $50,000 fine has noticed a real shift in the questions that he is being asked. Things have changed from, “What do […]
Hackers are ready for Euro 2024 finals kick offs! Will they be eliminated or score?

Euro 2024 viewership has been strong throughout the event and millions of visitors and viewers of the games themselves are also expected. Berlin alone is expected to host 2.5 million tourists during the month of the games. Such a large and central event that generates huge sums of money is of course a very lucrative […]