Blackhat 2024 wrapped up last week and we had quite a show! We advanced our Purple Team, creating a new asset for our partners to advance their sales and spread the news on Skyhawk, discussed our automated response capabilities with prospects, which is a clear differentiator, and had great conversations at the booth!
Free Purple Team Assessment finds threats in one hour
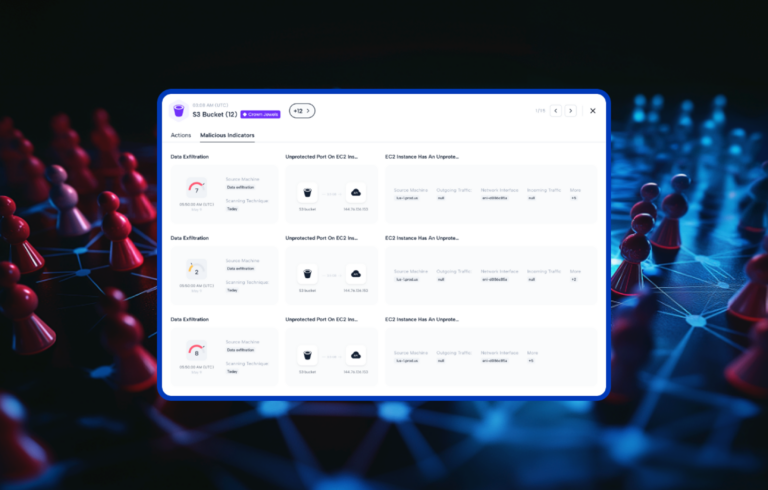
At re: Invent, we announced the Purple Team and at Blackhat, we announced the free Purple Team Assessment. In just one hour, Skyhawk Security will collect logs, telemetry, and other information to identify the threats within your cloud, and then prioritize them by the business value of the asset that the threat makes vulnerable. This information ensures organizations can address the issues that would cause the greatest harm to the business. The Purple Team Assessment predicts where threat actors will go, so those issues can be fixed to prevent the cloud breach.
If you would like to get more information on the free assessment, fill out the form on the page.
Automated response is a clear differentiator
Skyhawk Security’s automated response enables organizations to leverage automation safely and effectively. With the AI-based purple team, you can see what the AI-red team simulated to get to your crown jewels. The platform will then create an automated response to stop the threatening behavior. Everything is verified in the AI simulation, so security teams can confidently leverage the response. Check out the blog for more.
Top Questions at the booth
- What do you mean when you say purple team?
-
- We say Purple Team because we have a red team and a blue team “fighting” each other and these blend to create the purple team. These are completely AI-based teams and the execution of the “fight” happens in a Simulation Twin so it will not impact production. The purple team leverages business priority rules and automation to identify the crown jewel assets that if breached, would cause damage to your company. We prioritize threats based on the business value of the asset so you know what to fix first. Check out the Purple Team page for more information.
- What is the Purple Team Assessment? What does that mean?
-
- If you give us one hour, we can help you identify threats in your cloud and then prioritize them based on the business value of the effort. Check out our press release for more information. At the end of the assessment, we will give you a report to clearly communicate to senior leadership how the Purple Team will help you. This is a completely free assessment.
- How many people are part of the red team and the blue team?
-
- We do not have a red team or blue team staffed with people, it is all AI-based. Check out this 3-minute video to learn more about the purple team and how we use AI that is continuously running to find weaknesses in the cloud attack surface to prioritize and fix threats. The team at Gestalt IT also mention how using AI for red and blue teaming is a great use case.
- How do you collect the data? Is it agents?
-
- We do not use agents. We collect data from logs, telemetry, even security tools like AWS GuardDuty. We sort through all this information and correlate it into an attack sequence, weeding out benign events and focusing on what is a threat. Alerts from Skyhawk need your attention. They are verified alerts.
- Will this help with alert fatigue?
-
- Yes! As stated, Skyhawk Synthesis Security Platform sorts through thousands of events, logs, telemetry, and input from other security tools and surfaces verified alerts. In this blog, you can see a real customer environment where the platform sorted through 60,000 events to deliver 50 verified alerts. SOC teams are overwhelmed if they are presented with 60K events, but they can address 50 verified alerts.
- What is used for threat detection? Is it just patterns?
-
- Skyhawk Synthesis leverage AI in several ways to detect threats. First, three layers of machine learning models process logs, telemetry, and many other data sources. These machine learning models are customized for the cloud and are updated daily for three reasons:
-
-
- To prevent drift
-
-
-
- To ensure that threat actors cannot reverse engineer them
-
-
-
- And finally, to ensure that as your cloud architecture evolves and changes, the threat detection models are also aligned to ensure your cloud security is aligned with the cloud architecture.
-
-
- Additionally, Skyhawk Synthesis integrated ChatGPT and other LLMs to evaluate the attack sequence and detect threats up to 78% faster. In fact, we were the first security company to use ChatGPT in this way.
- The Purple Team is another way we leverage AI in our platform, and there are other ways as well – contact us to learn more!
Action at the booth.
Thanks to the Cloud Security Alliance, we had a Certificate of Cloud Security Knowledge (CCSK) to raffle off at the booth. Congratulations to the winner! We had many very good conversations, and several security experts were very interested in the AI-based Autonomous Purple Team, and seeing the report from the Assessment showed that this is real. We look forward to following up with everyone who stopped by the booth!