Part 2: Prevent Cloud Breaches with an AI-based Purple Team
One of the reasons security teams are not successful is they are always looking back, looking back at the breach or the exposure or the alert. They are not able to look forward to prevent the breach, exposure, or alert from happening in the first place – until now. Skyhawk Security’s AI-based Autonomous Purple Team […]
Part One: You do need CDR, Proactive CDR.
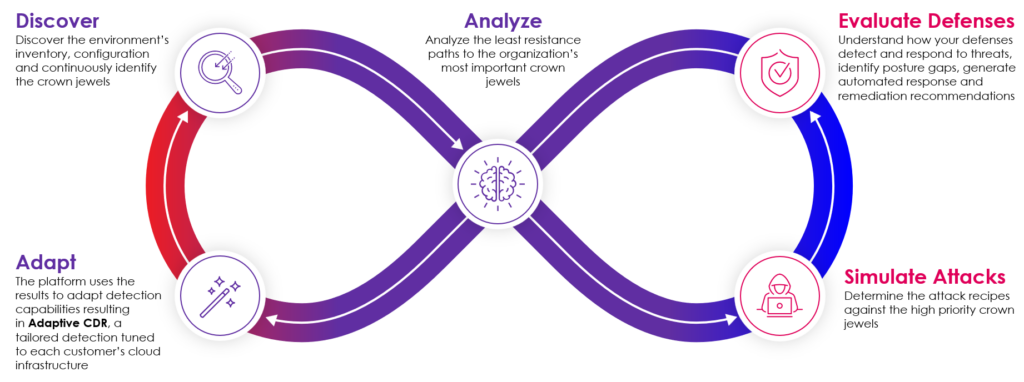
At Skyhawk, we have always known that CSPM, and even the next-gen of CSPM known as CNAPP, is not enough. In fact, by 2026, 50% of the attack surface will not be patchable, meaning CSPM/CNAPP solutions will not be effective. This is especially the case with cloud. Cloud surfaces are more difficult to patch as […]
Why Switch to a GenAI-Based Purple Team for Enhanced Cloud Cyber Defense?

Skyhawk Security announced our Continuous Proactive Protection solution at re: Invent in 2023. The response has been nothing short of spectacular – and the feedback we are getting is – you had me at GenAI-based Purple Team. Many organizations have red teams and blue teams that are constantly simulating attacks and evaluating defenses to […]
RSA 2024: Skyhawk Security Wins Innovator Award and Launches CTEM – Purple Team

Summary: RSA 2024 was a remarkable event for Skyhawk Security, filled with exciting announcements, significant achievements, and valuable conversations. Here’s a recap of our highlights and major accomplishments. RSA 2024 Highlights I hope you are all recovered from RSA! We had a great conference – lots of productive conversations at the booth, good analyst meetings, […]
Operationalize Your Cloud-Native Threat Exposure Management (CTEM) Program
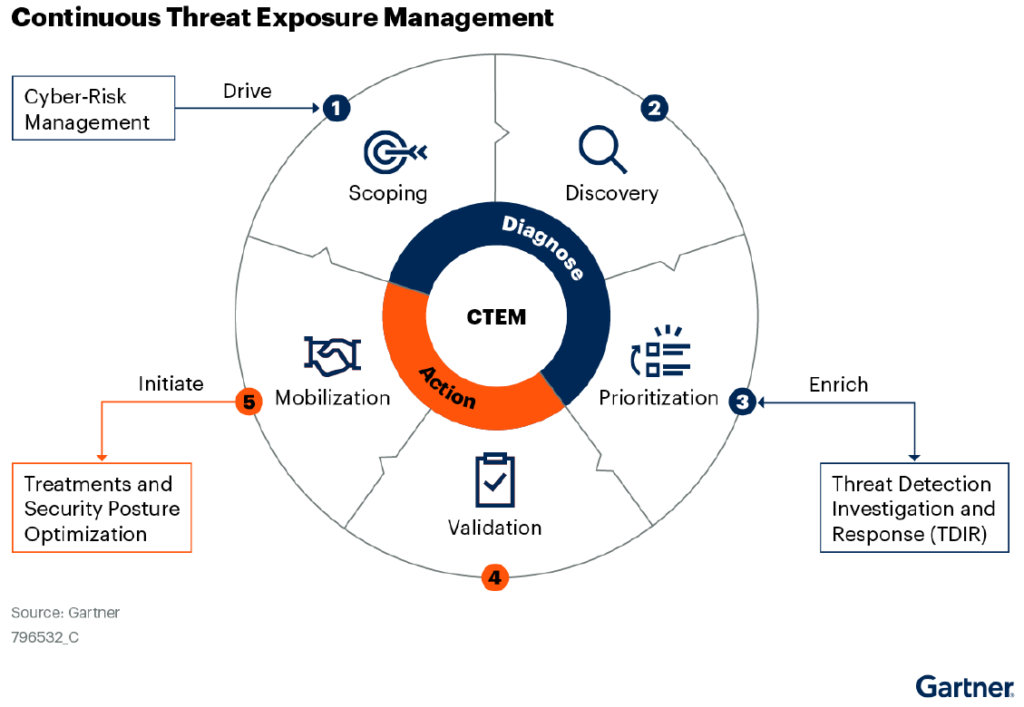
Continuous evolving clouds with continuously evolving threats need continuous threat exposure management (CTEM). This programmatic approach to managing threat exposures can help organizations dramatically reduce breaches. Many organizations are well on their way. According to a Gartner Peer Insights survey, 75% of respondents either have a CTEM program in place or are working on implementing […]
2024 Cloud Awards: Skyhawk Security a Top Finalist with Advanced Cloud Solutions

Skyhawk Security stands out in a competitive market! The organization is proud to announce that it has been named a finalist in the 2024 Cloud Security Awards program in four categories: Cloud Security Innovator of the Year Best Use of AI in a Cloud Security Solution Best Security Compliance in Enterprise Best Vulnerability Scanner/Assessment Solution […]
Skyhawk Security was at Cybertech – What did you miss?

The Cybertech conference of 2024 was supposed to mark the tenth year of the event that has long been considered the most significant in the local industry. The event that started as an event by Israelis, for Israelis, has long since become the “showcase” of the local industry, where established companies such as Checkpoint, large […]
Skyhawk Security is Exhibiting at RSA

Did you know cloud attacks increased 75% over the last year? Or, that human error was the leading cause of cloud breaches at 55%? And 75% of businesses state that more than 40% of data stored in the cloud is sensitive? Or that valid accounts are being used to attack your cloud, and these attacks […]
Managing the Unseen Attack Surface

US National Institute of Standards and Technology (NIST) defines “Attack surface” as: The set of points on the boundary of a system, a system element, or an environment where an attacker can try to enter, cause an effect on, or extract data from, that system, system element, or environment. However, this definition is predominantly relevant […]
The Perfect Storm: Lack of Security and Cloud Skills

It is a fact that the security industry suffers from a chronic shortage of skilled employees. This global shortage, which ISC2 estimates at 4 million professionals. The global workforce is estimated at 5.5 million people, meaning it nearly needs to double itself to keep up with growing demand. This is so profound that 71% of […]