Did you know cloud attacks increased 75% over the last year?
Or, that human error was the leading cause of cloud breaches at 55%?
And 75% of businesses state that more than 40% of data stored in the cloud is sensitive?
And finally, misconfigurations present the greatest risk for web applications, and by 2026 non-patchable attack surfaces will represent more than half of an enterprise’s total exposure.
If these statements concern you, book a meeting or visit Skyhawk Security at Booth 2267 at RSA.
Skyhawk Security is very excited to be at RSA! We cannot wait to speak with you about our proactive approach to cloud security, Continuous Proactive Protection. It is our AI-based autonomous purple team that helps strengthen and increase the accuracy of our Cloud Threat Detection and Response.
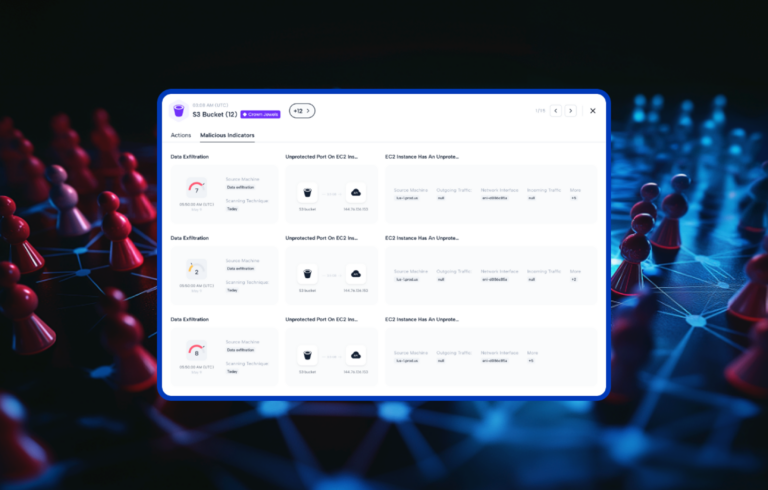
So, let’s start with our Threat Detection. Skyhawk Synthesis Security Platform leverages three layers of AI to detect incidents and threats in your cloud before they become a full-blown cloud breach. Skyhawk’s machine learning models sort through logs and telemetry to identify related events and activities, which are then correlated into malicious behavior indicators. Check out this 2-minute video to hear from one of our customers.
The malicious behavior indicators are correlated into an attack sequence. This helps identify realerts that actually pose a threat to your cloud. Using these layers of AI, we are able to identify unknown unknowns, check out our blog to learn more.
In March of 2023, we incorporated ChatGPT and other LLMs to more accurately and faster detect threats, 78% faster to be exact.
Finally, we would like to introduce you to our new proactive approach to cloud security. Continuous Proactive Protection continuously analyzes customer cloud infrastructure, proactively runs attack simulation against it and uses the results to prepare verified detections, validated automated response and remediation recommendations to ensure the cloud has the most up to date security defenses in place. This continuous protection process includes learning and automated adaptation of threat detection methods. This enables security teams to take a proactive and adaptive approach to their security strategy for the very first time, check out 3-minute video to learn more.
PS Skyhawk Security is a FINALIST in FOUR categories by the Cloud Awards.