The cloud revolution has taken the business world by storm, and the thunder is still roaring. From the smallest companies to Fortune 500 enterprises, organizations are launching their data, workloads, and applications into the cloud. And gleefully reaping the benefits. However, as with most revolutionary technologies in the past, the rushed pandemic-fueled race to digital transformation led most organizations to neglect information and cyber security in their roadmap.
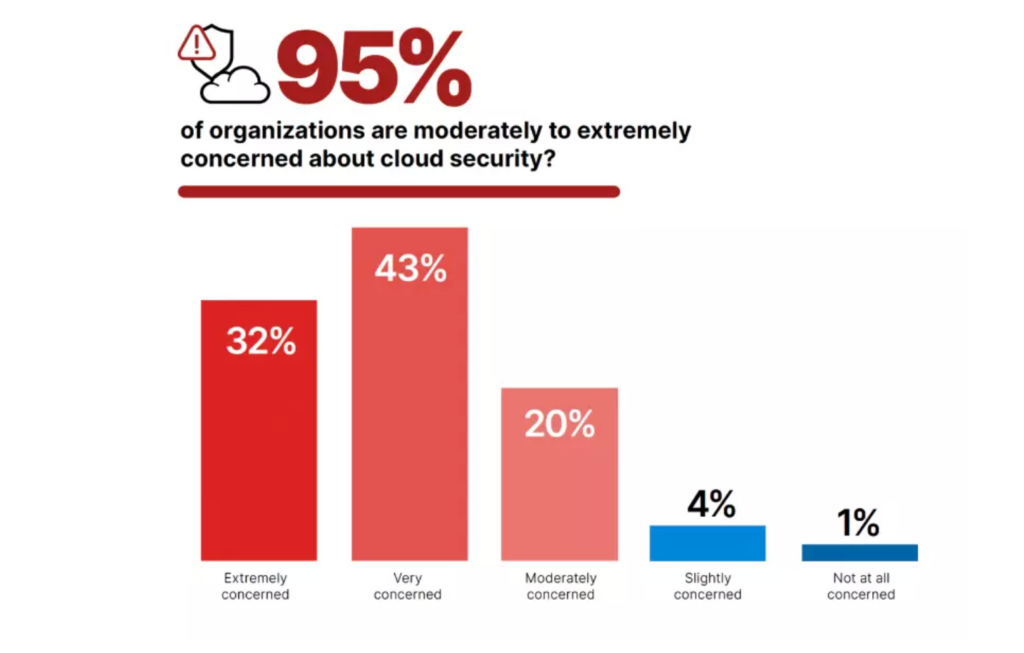
As many as 80 percent of organizations that spend over one million dollars annually on cloud infrastructure admit needing a dedicated security team to protect their cloud assets and resources. Left to pick up the slack are information security teams that are, on average, responsible for 32,190 devices (including 28,872 cloud hosts) per team. So it’s no wonder that most IT and security leaders are not confident in their organization’s ability to ensure secure cloud access.
But not all is bleak. With suitably skilled infosec professionals aboard, along with advanced tools and automated processes employed, most organizations can make the most of the cloud without exposing the business to cyber risk. But how can you tell if your business is equipped with everything necessary to maintain your security posture as cloud services use grows to include more critical business processes and infrastructure?
Let’s meet the Cloud Security Maturity Model (CSMM) and discover how to use it to empower your overall cloud security strategy and information security teams.
What is a CSMM, and who needs one? An Overview of the Cloud Security Maturity Model
The Cloud Security Maturity Model (CSMM) is a framework that helps organizations evaluate and improve their security posture. Unlike GDPR or PCI-DSS, it is not a single set of regulations but rather a list of general criteria that enable organizations to gauge the security of their cloud resources.
CSMM aims to facilitate business-oriented discussions about cloud security requirements, priorities, and strategies, looking at both the current and future use of cloud computing. It can help businesses assess their cloud security capabilities to craft a better-informed roadmap, considering evolving cloud security threats and industry best practices.
It’s worth noting that there’s no single one-size-fits-all cloud security maturity model. For example, the model offered by IANS and the Cloud Security Alliance assesses the state of your cloud security program against 12 categories over three domains. AWS offers its own homebrewed Security Maturity Model Assessment Tool (in Excel). Tata Communications focuses its model on multi-cloud environments and challenges with a 23-question survey to determine your cloud security maturity quotient.
The 5 Levels of a Cloud Security Maturity Model
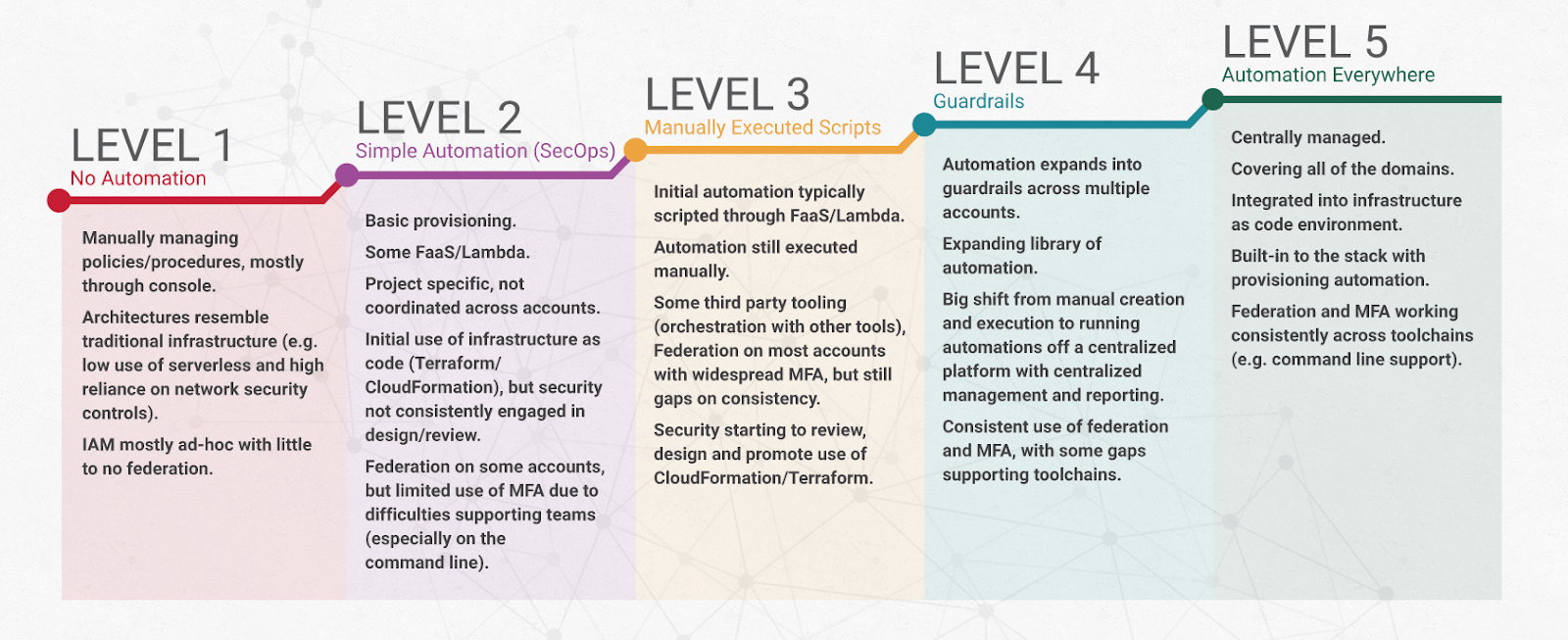
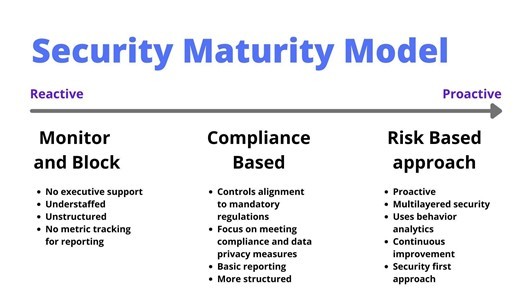
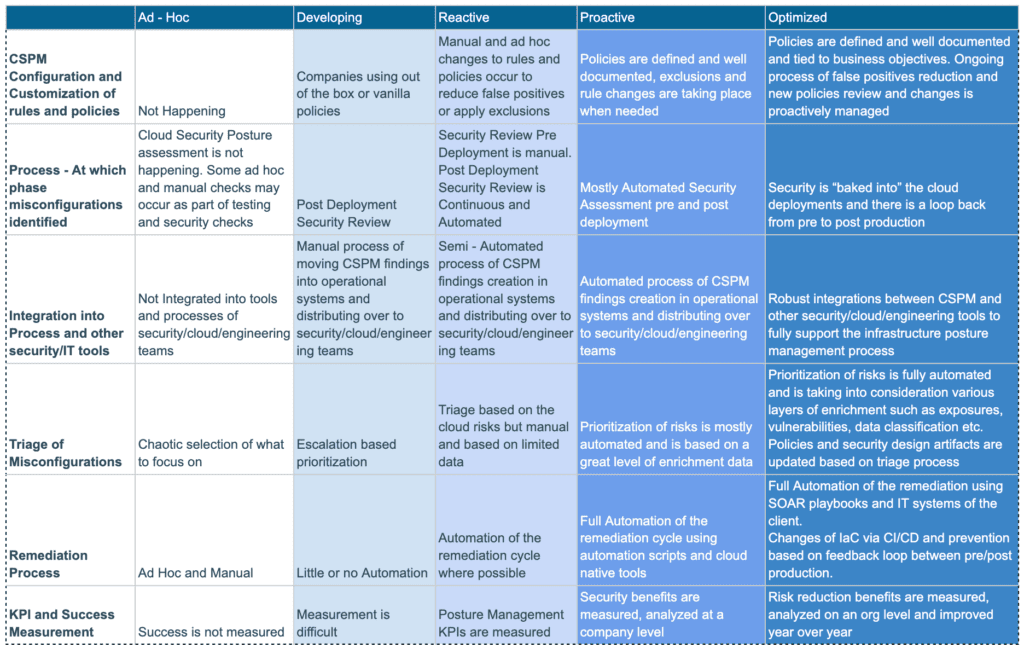
Traditionally, a CSMM consists of five levels of maturity. Each group represents a stage in the development of cloud security capabilities. For example, the model proposed by IANS Research and the Cloud Security Alliance looks like this:
Before we discuss the topic of cloud security maturity assessment, it’s worth drilling into each level traditionally found in a CSMM.
Level One: Basic / Initial
Organizations on this level don’t have a formal cloud security roadmap or strategy, with uncoordinated and unstructured ad hoc efforts, manual security controls (like scanning), and undocumented policies. Level one organizations either don’t consider cloud security a priority or lack the resources to help them meet cloud security challenges, restraining their efforts to regulatory compliance.
Level Two: Intermediate / Developing
The organization has established some cloud security policies and procedures at this level, but their application and formality must be more consistent. Level two organizations are aware of cloud security risks and threats and are taking their first steps to mitigate them.
Level Three: Advanced / Defined
Having defined, established, and implemented a cloud security roadmap, an organization is well on its way to a fully realized and optimized cloud security posture. At this level, organizations have integrated active monitoring and management of cloud security across all cloud environments. In addition, Level Three organizations pay more attention to policy documentation, implementation, automation of controls, and self-auditing against industry standards.
Level Four: Leading / Managed
Organizations at this maturity level have a resilient and scalable cloud security strategy, with advanced security controls and practices that may go beyond industry standards. Level Four organizations have comprehensive policies, widespread implementation, high automation, and business reporting. They continuously research, develop, and adopt cutting-edge cloud security technologies, tools, and practices.
Level Five: Visionary / Optimized
The only way forward is to understand that there’s no such thing as 100% secure and optimizing the processes, strategies, and approaches in place. The optimized and fully mature organization has a strategic vision for its cloud security. It is pushing the boundaries of what is possible to stay ahead of potential threats and risks.
Reaching the highest level of cloud security maturity means that information security processes are continuously monitored and optimized with cutting-edge technologies and tools. For example, Skyhawk Security’s Synthesis Platform offers runtime visibility into cloud security and ML-based detectors to understand normal behavior in ‘peacetime’ while contextualizing real threats in runtime.
Assessing cloud security: How mature are you?
Having understood the different levels of cloud security maturity, you should be able to produce a rough estimate of your current cloud security maturity level. You can also use one of the (many) self-assessment tools and surveys, including the ones mentioned above.
Regardless of the tool or specific CSMM approach you choose to employ in your cloud security journey, it’s essential to address the gaps in skill, knowledge, and tools while aiming to empower your teams to handle the increasingly complex world of cloud security.
The challenges in achieving cloud security maturity
According to surveys, only a handful of businesses (circa five percent) can claim to have leveled their cloud security maturity up to five. In comparison, 84 percent of organizations say they are at only an entry-level maturity (level one or two). Even in security-aware organizations, cloud maturity can be surprisingly low due to a lack of proficient cloud security professionals or the pace at which attack surfaces can grow when multi-cloud environments get even more complex.
One of the main bottlenecks to cloud security maturity is the growing and increasingly versatile workload that lands on the shoulders of SOC teams and infosec professionals in organizations of all sizes. Adding to that are alert fatigue and organizational reluctance to adopt a security-first culture that plague established businesses and startups alike.
One of the first steps in improving cloud security is investing in a CSPM (Cloud Security Posture Management) tool that detects misconfigurations and enables you to prove compliance with security standards such as PCI, SOC, and HIPPA. If you’re new to CSPM – Skyhawk offers it free on up to 1000 assets.
Leveling up in Cloud Maturity with Skyhawk
While you can’t automate security culture, you can optimize your cloud security strategy with innovative solutions like the Skyhawk Synthesis Security Platform to empower your security teams with relevant, contextualized realerts. Eliminating the “noise” of alerts from multiple cloud service providers and security tools while contextualizing the relevant alerts to actionable fixes can make the difference between levels of cloud security maturity, regardless of the specific model or self-assessment tool you choose to employ.
Schedule a demo to discover how Skyhawk can lighten the workload on your SOC teams and enable proactive cloud security.