If your organization made it through 2022 without a single major cybersecurity problem in which sensitive data was compromised, you are part of a lucky minority. Cybercrooks are quick to follow as more businesses take their data, workloads, and operations to cloud-based infrastructure and services.
Last year, as many as 7 in 10 organizations in the US and Canada admitted to having digital assets compromised through an unknown, unmanaged, or poorly secured Internet-facing asset. And the bigger your attack surface, the higher likelihood you have to be targeted.
You can’t shrink your attack surface. The expansion of attack surfaces results from digital transformation and business growth in light of changing market conditions and priorities. What you can do is reduce risk and manage your attack surface by employing Attack Surface Management strategies, tools, and processes. What does attack surface management mean? And how do you make it work in 2023? Let’s dig in.
What is Attack Surface Management?
To define the term Attack Surface Management (ASM), let’s start by clarifying what an attack surface is and what managing it entails.
What is an attack surface?
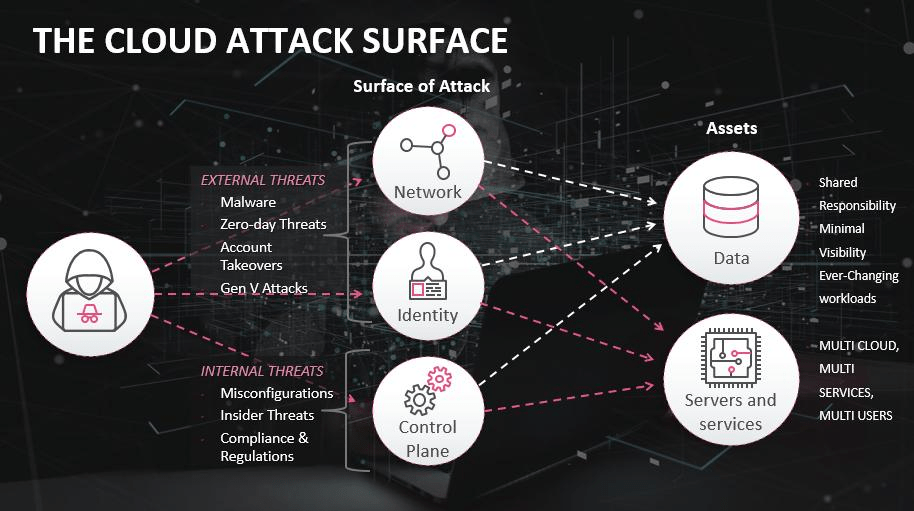
An organization’s attack surface includes all the components of the business that malefactors can compromise to gain access to sensitive corporate assets and resources. The attack surface is a holistic term that covers three categories of attack surfaces: digital, physical, and the social engineering attack vector we fondly call people.
Digital attack surface
An organization’s unprotected cloud and on-premises infrastructure is accessible to any cybercriminal with an Internet connection. There are various potential vulnerabilities across your digital attack surface that can serve as attack vectors. For instance, weak passwords, misconfigurations, unpatched software, poorly secured Internet-facing assets, shadow IT, and obsolete resources.
Physical attack surface
The physical attack surface of an organization includes hardware that can be stolen or compromised locally (like with an infected USB stick). However, it also pertains to data printed on paper, ideas written on a whiteboard near the window, and poorly secured 3rd party BYODs introduced into the corporate network.
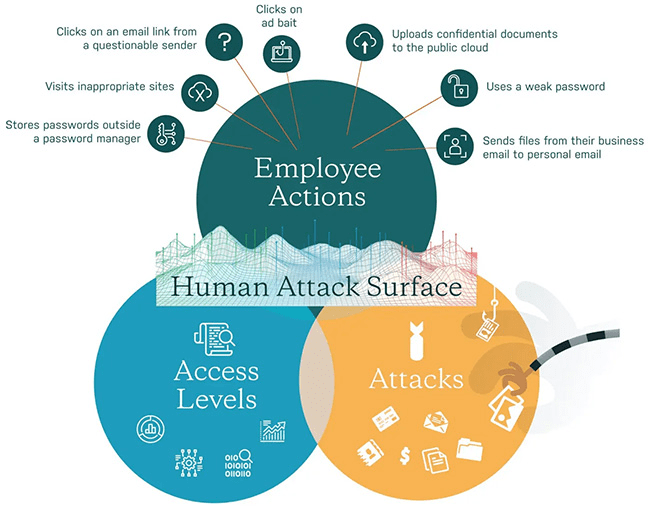
Human attack surface
The most complex attack surface that is also the hardest to manage is social engineering attacks. People can be tricked into handing over cloud service admin credentials or leaving the office doors open. There is a lot that malefactors can achieve by abusing people’s trust and naivety.
Phishing is the best-known type of social engineering attack, but cybercrooks have been known to employ other sophisticated techniques to mislead even the most tech-savvy users.
It’s important to remember that your attack surface is dissimilar from any other business’s and different from what it may have been yesterday or last week. Your attack surface management strategy must be uniquely suited and built for your company’s needs and future plans.
How can you manage an attack surface?
Now that we’ve defined an attack surface, you might think: “Why are we not discussing attack surface elimination, minimization, or reduction? Why management?”
The answer to that question is critical to understanding what is included under the ASM umbrella of tools and strategies. Attack surface management describes the continuous discovery, mapping, inventory, risk analysis, classification, prioritization, monitoring, and threat mitigation encompassing all company assets containing, transmitting, or processing sensitive data.
Performing the aforementioned activities may require integrating new tools in your infosec stack or implementing new policies using tools you already employ. To estimate what new tools you may need in your journey to successful attack surface management, it helps to look at ASM as a cyclical step-by-step process.
How Attack Surface Management works
The goal of ASM is to ensure that infosec teams always have a complete and current inventory of exposed assets and to accelerate the teams’ response to threats that present the most significant risks to the business. To accomplish that, attack surface management entails a series of actions that can be grouped into five steps.
1. Asset discovery
The first step of any attack surface management process is the discovery of all Internet-facing digital assets that contain or process sensitive data. Some of these assets may be owned and maintained by your organization, while others are in the hands of cloud providers, IaaS and SaaS services, business partners, and other third parties. Therefore, you must identify and map out all known, unknown, external, and rogue assets to gain complete visibility into the extent of your attack surface.
2. Inventory and classification
Now that you’ve identified and mapped out all your business’s digital assets, you need to evaluate the levels of risk posed by each resource. Fingerprint and contextualize the technologies in use, the content, the users and services accessing the assets, and their interactions with third parties.
3. Analysis and prioritization
Once you identify your digital assets, you must analyze them for vulnerabilities and prioritize them by exploitability and potential impact on the organization. This step entails defining actionable risk scoring of potential threats across your attack surface – essentially evaluating your security posture.
This step ensures that the most critical issues and vulnerabilities are prioritized for mitigation and remediation without overloading your infosec and DevSecOps teams with unnecessary tasks and alerts.
4. Mitigation and remediation
By now, your team should be able to address the vulnerabilities in order of priority and implement the necessary controls and tools to protect your digital assets. Remediation and mitigation usually entail integrating security controls, implementing policies and best practices (such as zero-trust), and bringing previously unknown or unmanaged assets into the corporate infosec protection envelope.
5. Monitoring
The last step in the ASM process runs constantly and consistently from day zero. Security risks in the organization are continuously evolving. Therefore, businesses must equip themselves with continuous attack surface monitoring solutions that identify the security gaps between the attack surface map created in the first step of the process (discovery) and the state of vulnerabilities and exploitable attack vectors in real-time.
The role of ASM in monitoring extends to the cybersecurity ecosystem to alert security teams of newly discovered exploitable vulnerabilities that demand immediate attention.
Why you need to manage the attack surface of your cloud
Once upon a time, business networks had clear boundaries, protected by advanced firewalls and allowing access only through encrypted VPN connections. In 2023, traditional asset discovery and risk assessment frameworks and tools simply don’t cut it.
Digital business infrastructure today is complex and mercurial, extending far beyond the familiar walls of corporate networks and on-premises servers. Your attack surface today extends to any place your data is stored or processed and its journey in transit between the different components of your cloud infrastructure.
One of the main benefits of attack surface management for cloud-native companies is the perspective it takes – that of a malefactor – to evaluate and remediate exploitable vulnerabilities. ASM solutions aim to provide real-time visibility into these threats and monitor for newly emerging threats while providing context for prioritization.
Moreover, a successful ASM strategy is critical for communicating value to the C-suite. While the board may not care about CVE-some numbers, they want to know about vulnerabilities that can potentially negatively impact the business and how much it will cost to fix them.
7 Requirements for Successful Attack Surface Management
1. Get a complete picture of your attack surface
The discovery of all potentially vulnerable assets is not what it used to be in the old days of firewalled on-premises servers and encrypted, remote access. Today, your attack surface is much more dynamic, with entry points that appear and disappear with a single line of code in some obscure Policy as Code pipeline.
To get a complete view of your attack surface, you must monitor the data at rest, in transit, and runtime, especially regarding cloud-based resources and applications.
2. Automate asset and vulnerability discovery
Manual asset discovery in a dynamic environment is impossible. To effectively map and manage your attack surface, you must arm yourself with advanced ASM tools that discover and map out potential internal and external entry points on the attack surface in near real-time (instead of scheduled vulnerability scanning).
It’s important to remember that different ASM tools serve other purposes. So, for example, some solutions also can enable DevOps teams to monitor, provision, and secure digital assets in CI/CD pipelines. Others may focus on regulation-compliant management of sensitive user data.
3. Reduce false positives
The impact of alert fatigue on the effectiveness and burnout of infosec teams is immeasurable. False positives aren’t only irrelevant notifications that alert you of vulnerabilities that don’t exist in your systems. False positives also mean unactionable alarms that fail to provide the context necessary to take preventive or remediation measures.
By employing an attack surface management solution that uses context to correlate all your specific attack vectors in real-time, you can make it much easier for your infosec, IT, and DevSecOps teams to address issues promptly.
4. Ensure risk-based prioritization
Risk-based prioritization gives your teams a coherent sense of order and direction for tasks and assignments while first addressing the most critical vulnerabilities. The alert fatigue mentioned above is another reason to ensure all vulnerabilities are analyzed, contextualized, and given a risk score.
A comprehensive ASM framework (including asset discovery, threat intelligence, and ongoing cloud threat detection) should provide decision-makers with detailed and actionable insights to understand and act upon without overwhelming them with notifications and alerts.
5. Build security awareness
Human error is the leading cause of cybersecurity breaches. No ASM tool or framework can bulletproof your systems against human error. However, you can create a practical framework to reduce human error and manage your attack surfaces with the proper protocols, policies, processes, and awareness training.
6. Consolidate alerts
It can be nearly impossible to make sense of it all between false positives, dozens of various monitoring and reporting tools, and automatic notifications to Slack channels and email messages. Plus, attacks don’t tend to produce one or more alerts when they take place. They generate many warnings over time – just long enough for us to miss the connection between them.
You can use advanced root-cause analysis and mitigation tactics at the right time by employing an ASM solution that contextualizes and correlates activities into clear potential attack sequences.
7. Measure value
Lastly, setting KPIs and goals for your attack surface management strategy is essential. Measuring the success of your ASM strategy will also help prove the value of ASM to your overall infosec strategy when communicating value to the C-suite and board.
Enhance your ASM strategy with ML-enhanced Cloud Threat Detection by Skyhawk
Success in attack surface management today means keeping up with the evolving ecosystem of cloud services and emerging threats. Skyhawk offers not only Cloud Threat Detection and Response (CDR) but also entitlement management and regulatory compliance to ensure you can protect all your cloud assets with a single ML-powered cloud security platform.
To learn more about how Skyhawk can help secure your cloud, schedule a demo today.