Businesses rely on the cloud to store their most important data. While it’s true that cloud computing enables a much more efficient way to store and share data, you can’t blindly trust that your assets are safe.
Securing credit card data is particularly important for retailers and e-commerce sites that process credit cards. For these companies, protecting data and ensuring regulatory compliance in the cloud come with added requirements – specifically the Payment Card Industry Data Security Standard (PCI DSS) – that can easily overload IT and security teams. There is no wonder why less than 30% of organizations are fully PCI DSS compliant, as shocking as this figure is.
So how do you go about making sure that your assets are protected? This article will guide you through the PCI DSS’s official goals and requirements. Plus, you can download our free checklist to use on your day-to-day.
What are the PCI DSS compliance requirements?
The Payment Card Industry Data Security Standard, better known as PCI DSS, is a set of standards ensuring cardholders’ security of personally identifiable information (PII). Any business that stores, operates, or processes cardholder data must meet these requirements.
The PCI requirements started as a response to rising online payment fraud. First, the major credit card companies set their security practices to protect consumers. However, as business owners started accepting multiple card payments, meeting various compliance requirements for each card became difficult.
In 2004, five PCI DSS founding members — American Express, Discover Financial Services, JCB International, Mastercard, and Visa banded together to formulate the first PCI standard. Since then, PCI DSS requirements have revised its standards many times. The latest version, PCI DSS 4.0, was released in March 2022.
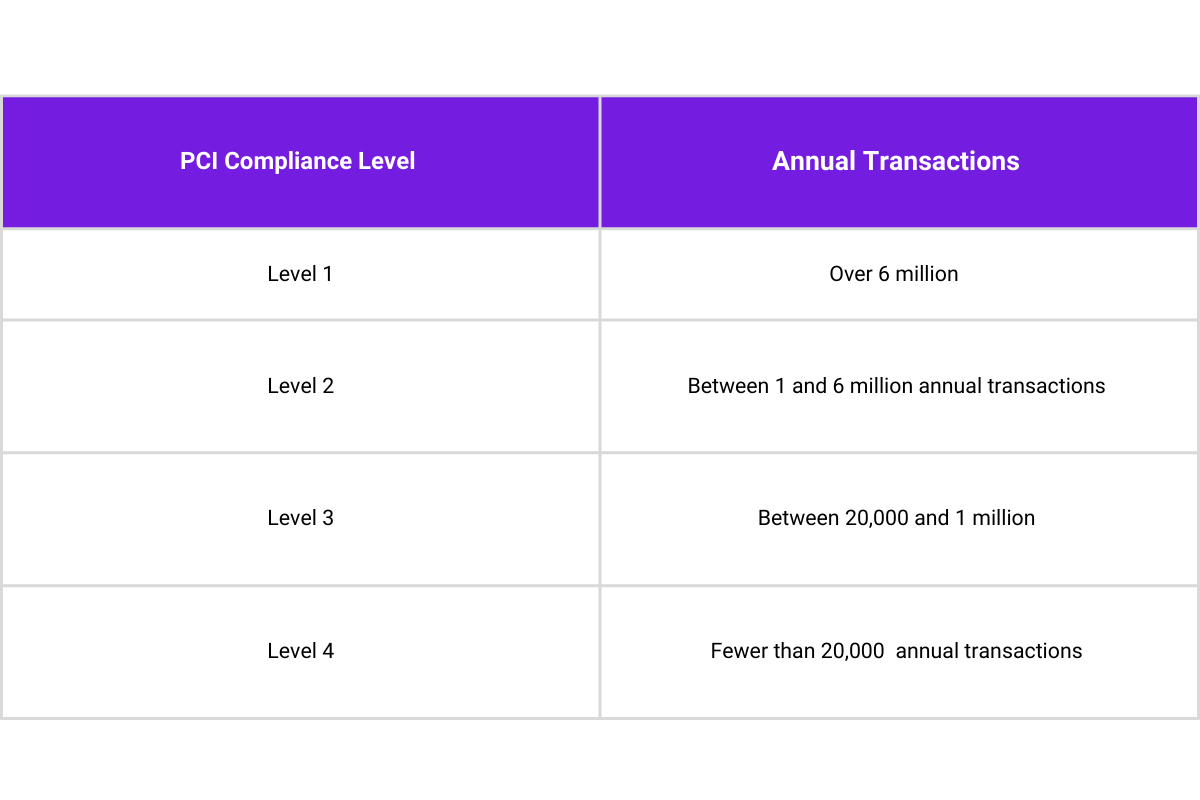
PCI compliance levels
PCI requirements become stricter, and compliance becomes more challenging the more transactions a company processes—fines for non-compliance range from anywhere between $5,000 and $100,000 a month until compliance is met. The acquiring bank may also set stricter compliance requirements for the future, stop any business with the merchant, or increase its transaction fees due to non-compliance.
The table below details the four levels of compliance:
PCI Requirements Compliance Checklist
As a whole, the PCI requirements work together to protect cardholder data, which include the primary account (PAN) number on the front of the card, the security code, the data stored on a card’s chip, and any Personal Identification Number (PINs) entered by the cardholder.
These requirements are grouped into six goals, with different steps to achieve each.
Goal #1: Build and maintain a secure network and systems
As global online payments surpassed $81 billion in 2022, hackers have more opportunities to execute payment fraud than ever. Putting the proper controls in place can help prevent them from gaining unauthorized access to your organization’s network and systems.
1. Install and maintain a firewall configuration
Firewalls protect cardholders and defend against malicious threat actors who wish to gain access to your organization’s email, internet, and e-commerce systems.
It’s not just installing that firewall but maintaining it that helps your organization meet PCI requirements. This includes configuring rules and criteria for your firewalls and routers to create a standardized process to restrict inbound and outbound traffic from “untrusted sources.” You should document the process so that it is clear to your IT and security teams how cardholder data flows between systems and networks. Review these configurations every six months.
2. Don’t use default passwords
Default passwords are one of the easiest ways to hack into your network and systems, as most default passwords of network devices are widely publicized in the hacker community. Ensure you change the default passwords of vendor-supplied systems, such as firewalls and servers, as quickly as possible. Equally, don’t offer default passwords to new users to avoid having users with weak passwords accessing your application.
Goal #2: Protect cardholder data
Organizations are required to protect the payment card information of cardholders, including the physical, local, or online storage of data, whether transmitted internally or in public to an ISP or server.
3. Protect stored cardholder data
Data (including data in the cloud) cannot be stored unless necessary for the business. Any data that must be stored must be encrypted. Card PAN numbers must be masked so that only the last few digits are visible to the merchant.
4. Encrypt transmission of cardholder data
Just as crucial as protecting stored data is the protection of transmitted data. PII and other sensitive data transmitted over unencrypted networks such as chats, emails, or forum sessions is an open invitation to malicious actors. This includes data encryption over secure protocols such as SSL, SSH v1.0, and early TLS, as they have known vulnerabilities.
Goal #3: Maintain a vulnerability management program
Payment card infrastructure systems are a perfect target for malicious threat actors since they have the potential to offer an enormous reward. Vulnerability management programs are, therefore, one of the most critical aspects of defending against security incidents.
5. Protect all systems against malware, and use and update anti-virus software
Malware, a type of software that attempts to steal PII from your organization’s system, is one of the most common causes of security incidents for SMBs. Defend against malware by installing up-to-date, advanced anti-virus software on any device or equipment (i.e., desktop, laptop, servers) with access to your network and systems.
6. Develop and maintain secure systems and applications
Put a proper risk assessment in place to deliver full visibility into your existing security environment. After this is complete, you will have a more comprehensive understanding of which security patches provide your organization with maximum protection against exploitation.
Goal #4: Implement strong access control measures
Access control measures restrict what users can see in your IT environment. Users should be permitted access to cardholder information only on a need-to-know basis based on the principle of least privilege.
7. Restrict access to cardholder data by business need-to-know
Restrict access of cardholder data to users based on their job title, seniority, or specific need. This protects against misuse from inexperienced or new users and those with malicious intent.
8. Identify and authenticate access to system components
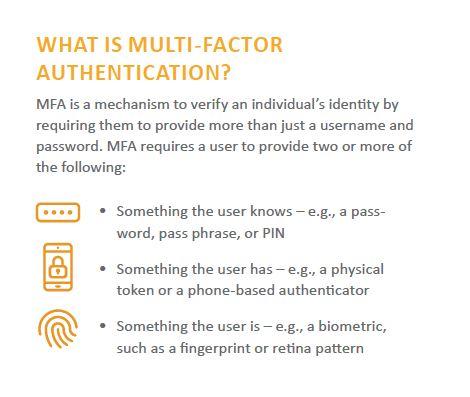
Create unique user IDs and passwords for each individual with access to cardholder data. Malicious actors should not be able to guess them easily. Access should also only be available through multi-factor authentication (MFA).
9. Restrict physical access to cardholder data
Your organization’s servers, computers, and data centers are physical locations that store data. Limit these areas to employees by mandating the use of badges and keylocks.
Goal #5: Regularly monitor and test networks
To ensure your organization can continuously discover vulnerabilities, you’ll need to monitor and test your networks regularly, including testing and maintaining system components, processes, and legacy, cloud-based and third-party software.
10. Track and monitor all access to network resources and cardholder data
Establish a logging process to track access to devices that store, process, and transmit cardholder data so that your organization can troubleshoot and properly investigate if a security incident occurs. Logs must be reviewed daily, and you should hold audits of network activities dating back one year.
11. Regularly test security systems and processes
Conduct quarterly vulnerability management scans and annual penetration tests. Ensure wireless access points are secure and eliminate unauthorized wireless devices since these are the most common methods attackers gain access to networks.
Goal #6: Maintain an information security policy
Just like installing and maintaining firewalls, it’s not enough to build a security policy – your organization must also maintain it.
12. Maintain a policy that addresses information security for all personnel
Your organization must communicate its security guidelines to employees, executives, and third-party vendors. Security awareness training programs, regular security policy reviews, and internal background checks are all parts of such training.
Achieve the highest level of PCI compliance in the cloud
As of 2022, 60% of all business data is stored in the cloud. With the increasing reliance on cloud services, overlooking cloud security is not a risk worth taking. But you can’t do everything yourself, and you can’t expect your cloud service provider to do everything, either.
You need a CSPM (Cloud Security Posture Management) solution that can make regulatory compliance as easy as possible. A solution that enables you to verify compliance, understand the requirements of various regulatory frameworks (PCI DSS included), and detect misconfigurations to prevent accidental (and costly) breaches.
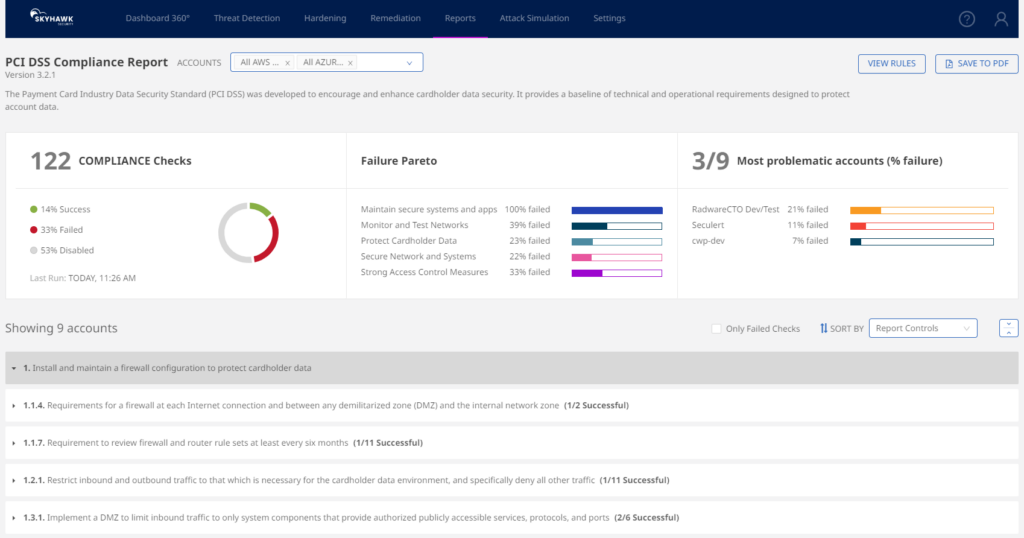
In the image above, you can see how Skyhawk Security’s Synthesis Platform can assess, across all of your cloud assets, if your environment is PCI compliant. Users can run regular reports to share with their teams and leadership to validate and prove compliance. In the example above, Skyhawk helps the user run 122 different compliance checks for PCI and then shows which passes or fails, as well as how to fix those issues. This is part of Skyhawk’s CSPM offering and is completely free for up to 1000 cloud assets.
Want to learn more about how your organization can meet PCI compliance in the cloud? Download our simplified PCI DSS Compliance Checklist today.