SBIs and MBIs from Skyhawk Security – what are they? What do they mean and why do you care?
SBIs are suspicious behavior indicators and individual events, and MBIs are malicious behavior indicators correlating a sequence of SBIs that together are raised to indicate an alert. Differentiating between these two types of behaviors communicates to security teams when action is required to reduce risk in their cloud and prevent a breach.
Suspicious behavior indicators (SBIs) are events or activities that are precursors to MBIs. They are interesting data points that are monitored and consistently reviewed should there be a change in business risk. In the Skyhawk product we label them as activities. These are interesting events which have not yet been sequenced into an alert.
Malicious behavior indicators (MBIs) are activities that Skyhawk has identified as risky behaviors that require an investigation and may pose a threat to your business based on our own AI and ML modeling of what is normal for your cloud. The platform leverages log data to build Attack Sequences. Skyhawk Synthesis leverages MBIs and sequencing to detect incidents and breaches because there are typically several steps that resulted in the actual breach.
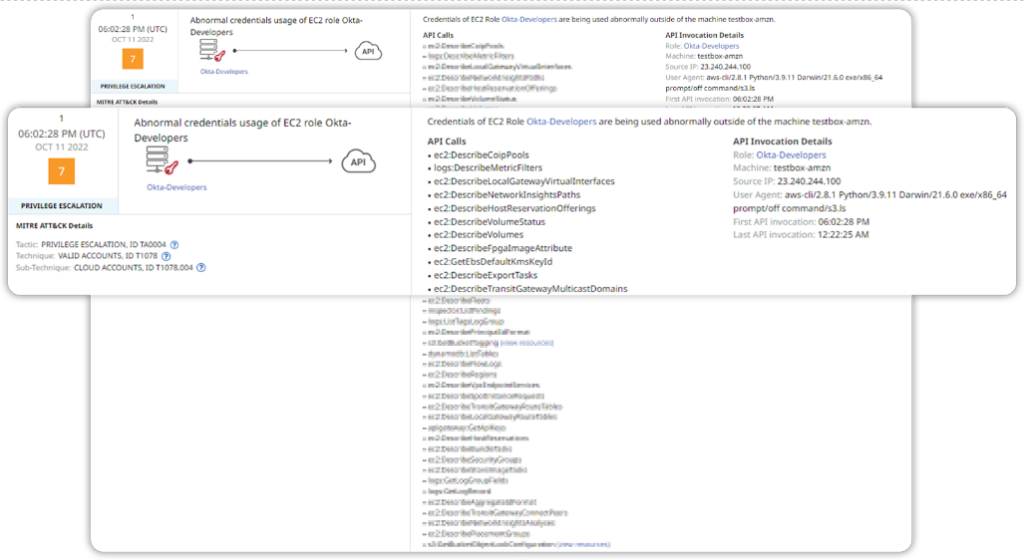
MBIs correlate multiple activities into a single threat. Other solutions will alert on every single API call in this list. The security analyst team would then have to correlate each of these activities to understand how these are malicious, the relationship between them, and how they are impacting the environment. This could take days! Skyhawk Synthesis correlates all these activities into a single event, an MBI. This saves the security team an enormous amount of time.
Figure 1: Many API calls are correlated into a single MBI, automatically.
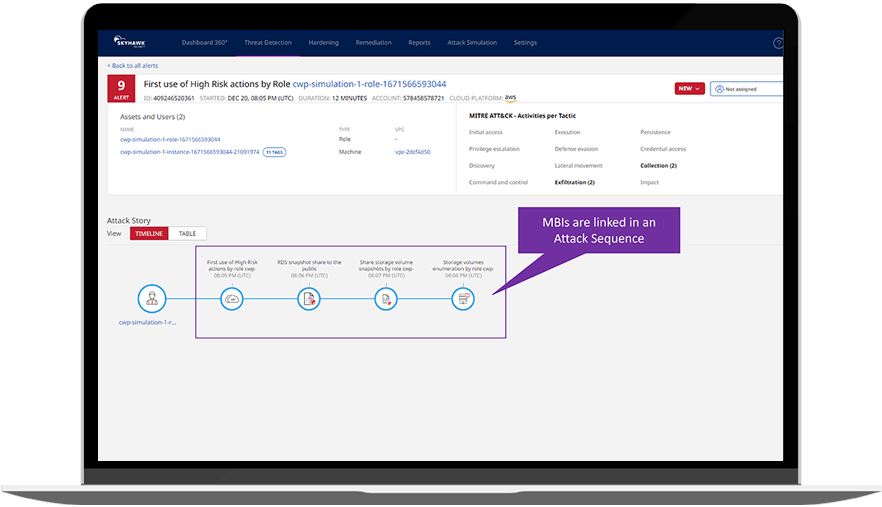
These behavioral sequences show how an incident unfolded. Not all sequences represent an alert, incident, or breach, but they do represent a sequence of behaviors that Skyhawk Synthesis is monitoring. These sequences are consistently scored as SBIs are added, and they are raised to a Realert – an incident that requires investigation once the risk score reaches a pre-defined threshold. An Attack Sequence gives context to a series of SBIs and the aggregation of the SBIs helps us understand the specific details of what is happening in the runtime.
Skyhawk Security eliminates this work from the SOC team with the clear classification of SBIs and MBIs. Our Skyhawk Synthesis Security Platform looks at the behavior in the cloud runtime and creates a baseline of what is normal. It will then flag issues as suspicious or malicious as they deviate from the baseline that was personally designed for your cloud. The AI and ML constantly review the risk of this sequence and once it reaches a threshold contextualized for your cloud, the SOC team is alerted in real-time that something requires an investigation.
Figure 2: MBIs are correlated into an attack story and once a risk threshold is reached, they are raised to an alert that requires the attention of the security team.
How does Skyhawk make this simple?
There are three main ways Skyhawk greatly simplifies the security in your environment regarding responding to alerts with the attack sequence.
- Correlate multiple activities into a single MBI: There is no one stop shop to correlate multiple suspicious and malicious activities to truly understand the intent and impact. For example, with cloud-native security tools you need at least three to look at cloud activities and determine that there is risk in the environment. Skyhawk does this seamlessly and automatically and shows you all the events that make up the MBI.
- The Attack Sequence: The platform correlates multiple MBIs into the attack sequence. These sequences are continuously evaluated for risk and once a threshold is reached, it is raised to an alert.
- Prevent breaches by stopping incidents: The MBIs and Attack Sequences ensure that your security teams are acting on actual incidents and threats that are compromising your cloud. The alerts in Skyhawk Synthesis require your attention as they are indicative of malicious behavior. This greatly simplifies the prioritization of work for the SOC. The SOC does not need to guess if they are working on the right issues, it is very clear that they are with Skyhawk Synthesis.
Want to learn more? Check out our website: www.skyhawk.security and our free CSPM offering.