Theoretical vs. Actual Cloud Threat Detection: How Skyhawk Discovers Incidents Before They Become Breaches
Today’s security platforms can identify misconfigurations, open ports, unused permissions, and databases exposed to the internet. These are all issues that need to be corrected as they could be exploited to breach your data. The operative word here is could. You do not know if any of these things have happened. Alerts on these issues create panic, with teams working to lock down your environment, hoping that your company will not be in the news.
Hope is not a strategy.
At Skyhawk Security, we know how confusing it is to get potential breach data instead of actual. Companies often confuse the market by calling their alert functionality an ‘attack path’ which sounds a lot like Skyhawk’s Attack Sequence technology. The difference between the two is actually quite significant.
How?
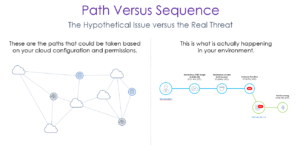
An attack path tells you that if someone compromises a particular permission, they could then compromise an EC2 instance, and then they might exfiltrate data. Knowing how threat actors may gain access to high value assets is only part of the issue. Security teams need to then chase down alerts and try to determine which attack path is used, when. While this may provide some awareness, it is not threat detection.
Skyhawks’ attack sequence shows what is happening in your runtime environment – may, could, might, and possible are not Skyhawk’s focus. Your personalized, contextual attack sequence, based on an ML model specific to your infrastructure, shows with finality which assets, permissions, and data in your environment are on the cusp of a breach. The Skyhawk Synthesis Security Platform finds what we call ‘realerts’ based on a series’ of connected actual events and notifies the security team of issues that require attention. This saves considerable time and greatly reduces false positives.
What are realerts?
The diagram below outlines what we define as a realert. Most incidents or breaches are not a single event, they are a series of events, executed slowly, to enable threat actors to go undetected. Skyhawk sequences anomalous movements and behaviors and constantly reviews the overall risk of the sequence. Once the risk threshold of the sequence has been reached, it is then marked as an alert. This is done before an incident or threat becomes a breach.
Skyhawk’s insight-driven Cloud Threat Detection & Response (CDR) platform dramatically reduces the time security teams spend trying to determine if a theoretical attack path represents an actual breach. Leverage Skyhawk’s security expertise to understand the malicious intent behind behaviors so your team focuses only on actual threats. Armed with this critical information, you can quickly contain the impact of the threat, so it never fully evolves to a breach. Amazingly enough, realerts can be detected in minutes.
Contact us today to start a proof-of-concept and see for yourself!






