Human error is responsible for 82% of data breaches. The figures are similar when it comes to the cloud, with misconfigurations and excessive permissions being the cause of most cloud security threats.
Managing accessibility and permissions within an organization is challenging, especially for large-scale enterprises with hundreds or thousands of users. Even more challenging is doing this while meeting pressing deadlines and striving to be more productive.
Two of the most popular solutions on the market, CIEM (Cloud Infrastructure Entitlement Management) and CSPM (Cloud Security Posture Management), are aimed at helping security and cloud infrastructure teams defend against misconfigurations and excessive permissions to prevent cloud security threats and their devastating consequences.
This article discusses the differences between a CIEM and a CSPM and the advantages of having both tools to protect your data and cloud.
The article will address the following questions:
- What is CIEM?
- How does CIEM work?
- 5 Benefits of CIEM
- What is CSPM?
- How does CSPM work?
- 6 Benefits of CSPM
- When do I need CIEM vs. CSPM?
- CIEM vs. CSPM: A two-tiered approach to cloud security
What is CIEM?
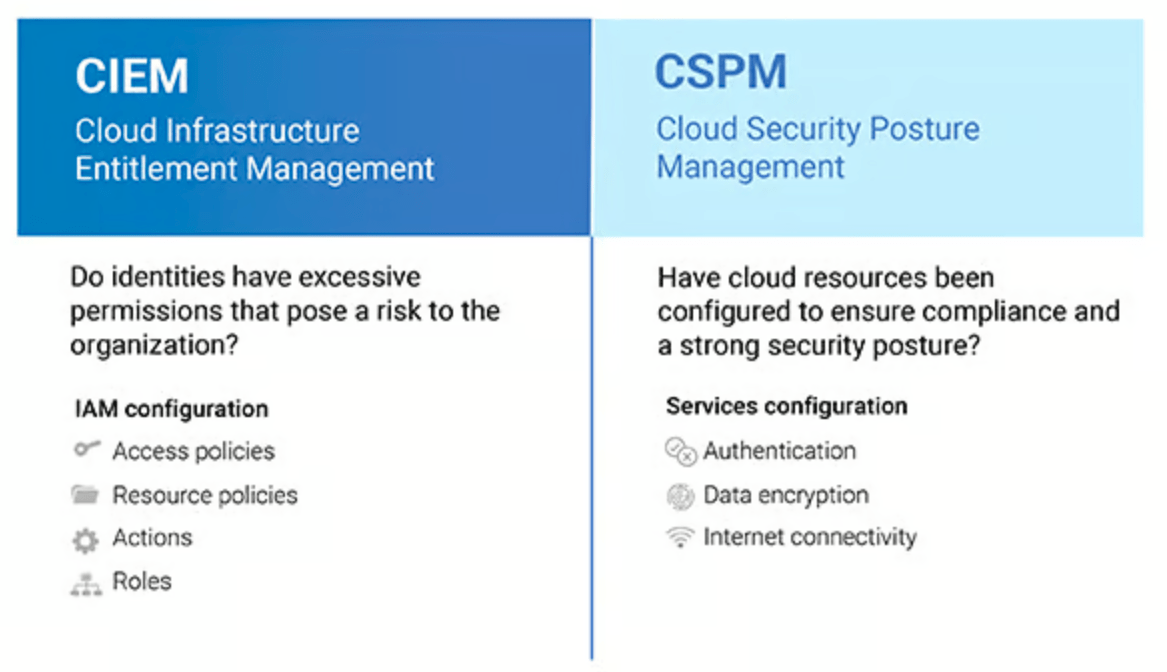
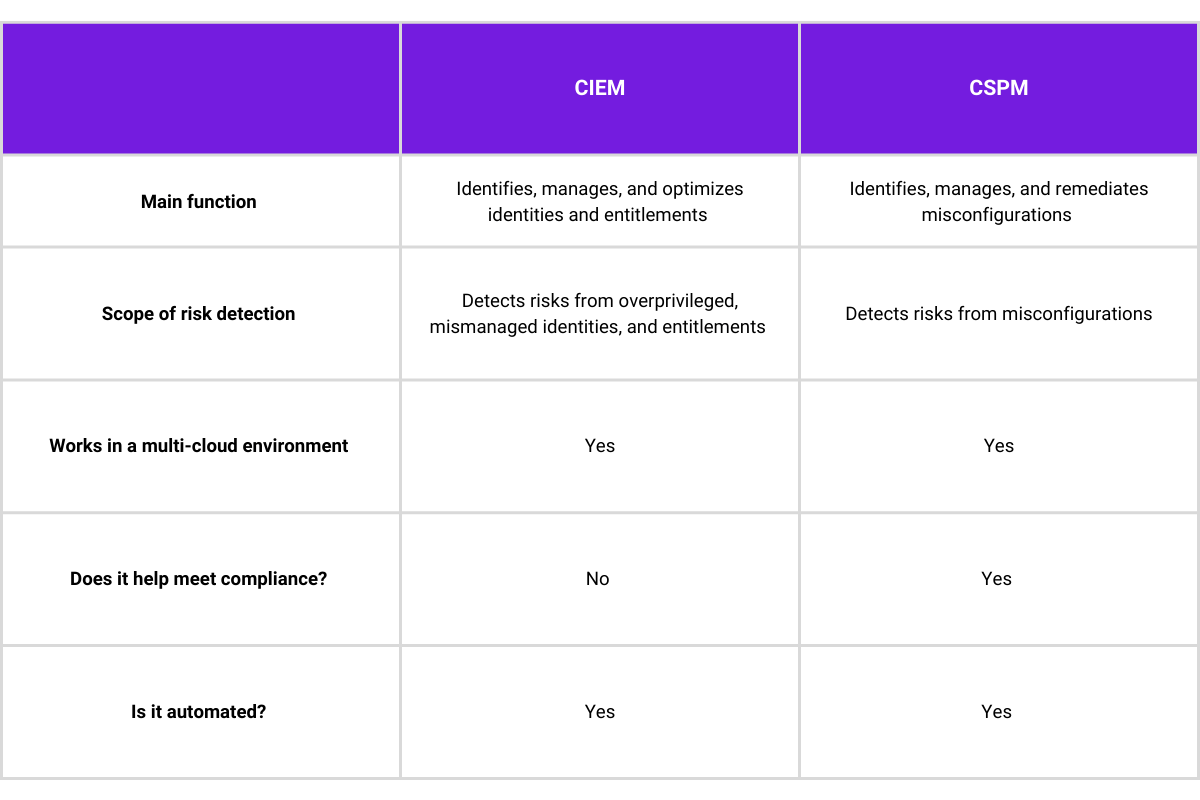
CIEM, or Cloud Infrastructure Entitlement Management, is a cybersecurity solution for managing permissions and access to cloud services.
In recent years, 34% of identity-related breaches involved the compromise of privileged accounts. Organizations look to Cloud Infrastructure Entitlement Management to manage overprivileged permissions in the cloud. If a user has too many permissions, an attacker could get full access to the cloud. Comprehensive CIEM is critical to protect malicious threat actors from exploiting any excess or overprivileged permissions in your organization.
Enterprise-level organizations with multi-cloud environments and hundreds of employees, vendors, and third-party vendors have thousands of identities, each with different permissions, access privileges, or entitlements. And these settings exist for hundreds of services and applications. Managing these policies and entitlements can scale into millions, and it is impossible to do so manually, demanding automated solutions.
Identity Management, also known as IAM (Identity and Access Management), is a framework of policies and technologies to ensure that the right users have appropriate access to technology resources. While this framework does manage policies, it still has its limitations. If a policy isn’t functioning as it should, users may have access to resources when they shouldn’t. You need a CIEM to identify, monitor, and optimize these policies, privileges, and entitlements.
How does CIEM work?
CIEM continuously monitors users’ leveraged privileges and identifies unused and overused privileges. The first step is to remove privileges that are not used to reduce the attack surface. Then, it looks for suspicious usage and may recommend lowering or eliminating their privileges in the IAM service.
It also operates by POLP, or the Principle of Least Privilege, limiting user access to only what is necessary and only for a specific timeframe. This type of access is known as a JIT PAM (Just-in-Time Privileged Access Management).
5 Benefits of CIEM
CIEM reduces your organization’s attack surface and strengthens its security posture with several tools that allow you to
- Gain better visibility of entitlements and data access risks through automated tracking and modification of identities and entitlements.
- Identify completely unused permissions, thus reducing the attack surface without compromising productivity.
- Get alerts that automatically detect behavioral anomalies, such as the sudden creation of new permissions.
- Meet governance and compliance more easily.
- Ensure granular and dynamic monitoring and configuration of entitlements.
- Remediate misconfigurations and detect the ability to bypass privileges.
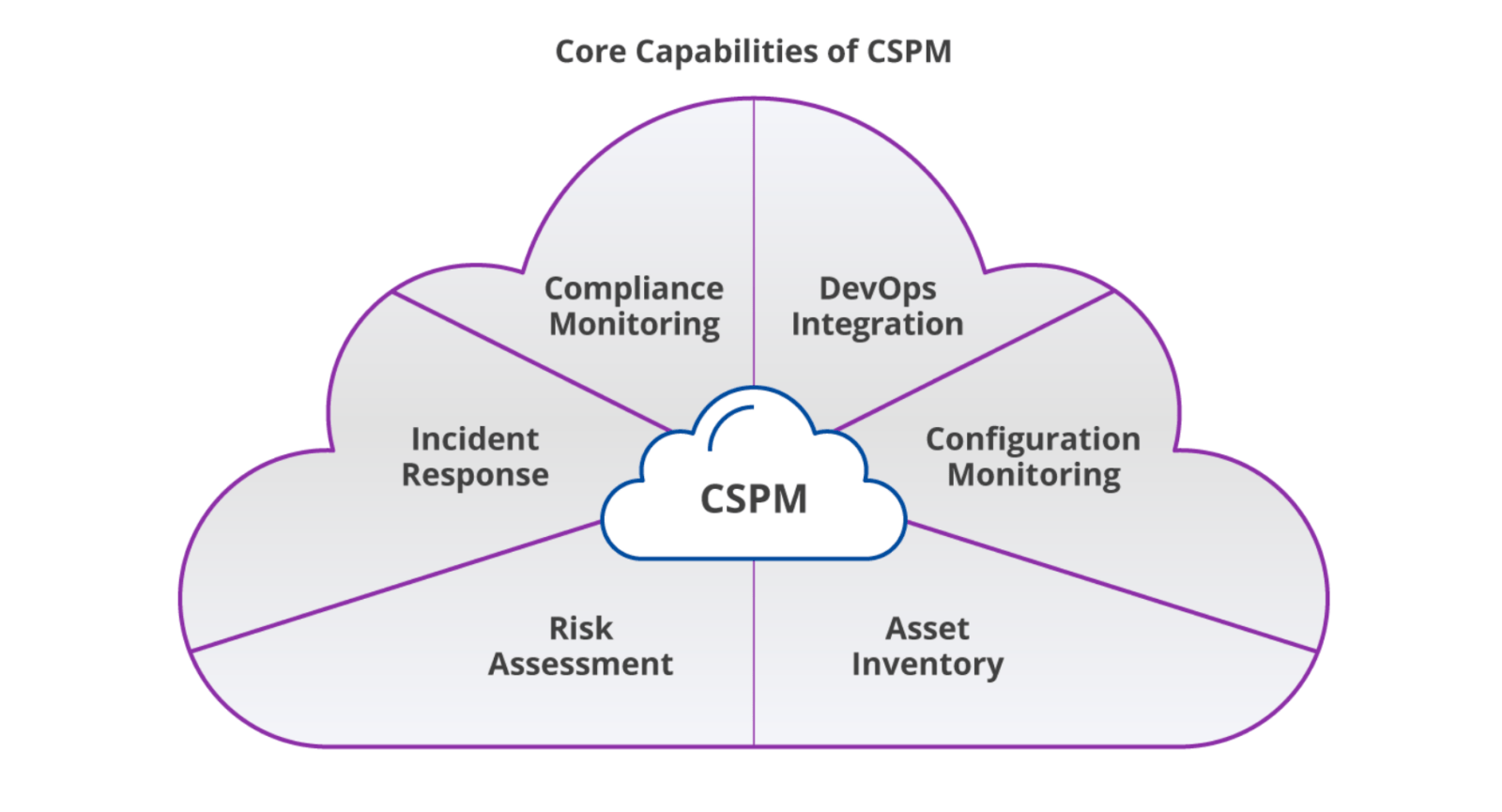
What is CSPM?
CSPM, or Cloud Security Posture Management, is the process of securing cloud assets and infrastructure by monitoring misconfigurations and vulnerabilities.
According to IBM’s Cost of a Data Breach Report, cloud misconfigurations account for 15% of the initial attack vectors in security breaches, making them the third-largest attack vector for data breaches.
While CSPM tools are broader in scope than CIEMs, they track, monitor, manage, and secure your cloud-based applications and data. They do this by identifying the assets in multi-cloud environments and assessing their risk from misconfigurations. The overall goal is to proactively fix misconfigurations to protect against data leaks in the cloud. This approach makes it much easier to identify and correct potential configuration risks and vulnerabilities and meet current regulatory compliance standards.
How does CSPM work?
CSPM monitors any changes in your cloud environment since initial deployment, identifies misconfigurations that could make it easier for attackers to get into the environment, and discovers the best mitigation strategies necessary to strengthen your security posture.
Although CSPM tools detect and remediate misconfigurations in the cloud, they may be limited to a particular cloud environment or service. For example, some CSPM tools may only detect misconfigurations in specific cloud environments (e.g., Azure and not AWS, or vice versa).
Most advanced CSPMs have similar features:
- Identification of cloud workloads and services.
- Detection and automatic remediation of misconfigurations.
- Alert notification when a change to the cloud environment, host, or service poses a risk.
- Verification that operational activities are at optimal performance.
6 Benefits of CSPM
CSPMs reduce the risk of data breaches by securing the cloud environment and making it easier to manage multi-cloud accounts. They enable you to:
- Meet security frameworks such as NIST and ensure compliance with internal and external compliance regulations such as SOC, HIPAA, and PCI DSS.
- Identify security risks that malicious threat actors can exploit, such as over permissions.
- Continuously monitor your cloud environment for ongoing threat detection.
- Establish a baseline for security configurations.
- Assess risk to your data.
- Get granular controls while consistently automating other tasks and enforcing security policies.
When do I need CIEM vs. CSPM?
The short answer is that you’ll need both.
Organizations that use multi-cloud environments need CIEM and CSPM solutions because each solution focuses on different security issues. CIEM reduces security risk from mismanaged permissions and entitlements, whereas CSPM focuses on identifying and remediating misconfigurations and helping organizations meet compliance guidelines.
Simply put, CIEM continuously checks and verifies permissions to prevent credential theft. Although cloud providers have native identity management solutions, these solutions aren’t available for multi-cloud environments. Solutions such as IGA (Identity Governance and administration) and PAM (Privilege Access Management) don’t offer granular and dynamic controls to manage identities and entitlements at scale. If you have hundreds or thousands of users and function in a multi-cloud environment, you’ll need a CIEM solution.
CSPM, on the other hand, offers a security solution with a broader scope. It continuously checks the configuration of the cloud that the applications are leveraging. For instance, it looks at whether RDS is encrypted and what protocols are used to measure and identify risks.
It also verifies that data configurations meet various compliance benchmarks. Organizations using multi-cloud environments have thousands of configuration options that can pose a security risk. Even more challenging is that these configurations are dynamic and require continuous monitoring – which is what a CSPM solution offers.
CIEM vs. CSPM: A two-tiered approach to cloud security
Only a combination of the CIEM and CSPM solutions will deliver strong protection of your permissions and entitlements, detection and remediation of misconfigurations, and the ability to meet regulatory compliance. Skyhawk Security offers CIEM and CSPM solutions to help SOC teams dramatically increase their productivity and know which exposures, permission, and compliance issues to address first. Want free compliance verification, governance enforcement, and misconfiguration detection? Get Skyhawk Security’s free CSPM solution today.