Earlier this spring, the Google Cloud team talked about how AI can help organizations close the talent gap. AI and ML are great tools for any security team to use to help augment staffing issues while improving threat detection to prevent breaches. Skyhawk Security also leverages AI and ML in the Skyhawk Synthesis Security Platform and can further help organizations secure their environment, detect threats, and prevent breaches.
- The first data point: 84% of respondents said that they are “fairly concerned” or “very concerned” that their organization might be missing real threats or incidents because of the volume of alerts and data that they must respond to and analyze.This plays right into Skyhawk’s wheelhouse, and we use machine learning with artificial intelligence to solve it.
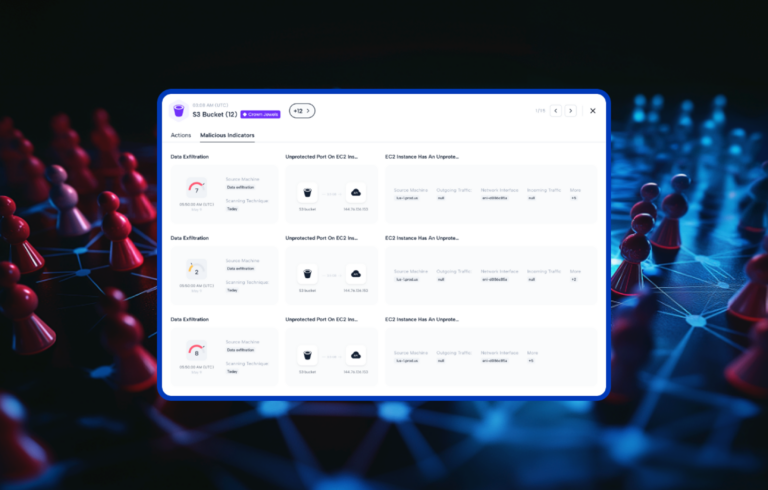
- First, machine learning models are created at several layers within the cloud environment to identify truly malicious behaviors versus just anomalies. These many events are correlated into malicious behavior indicators, which are then mapped into an attack sequence. These are realerts.
- Second, our integration with Generative AI further enhances threat detection by evaluating the risk profile of the attack sequence to determine faster if this is a malicious behavior executed by a threat actor and requires attention fast.
- These two elements working together, eliminate alert fatigue as the security team is only responding to realerts.
- In terms of minding the talent gap, Skyhawk Security once again solves this issue in two ways.
- First, the Security Advisor makes security information more accessible with the ability to explain the attack sequence in simple text. Security Advisor also offers remediation recommendations, so more junior users can leverage this information and create a remediation plan that a more senior security analyst can review, instead of creating. This gives the security analyst more time to focus on other security issues.
- Second, our Generative AI framework “mimics” human researchers, which reduces false positives and negatives, and as a result spares our clients expensive resources. Related to the attack sequence above, security analysts are responding to realerts and not wasting their time.
- Finally, Skyhawk Synthesis constantly learns the trending threats and adding them to our threat intelligence that is addressed by our threat detection and breach prevention. The only difference between this third point and the first two is that it is in beta and not yet generally available. This is also the product of integration with large language models and Generative AI and another benefit that can ease the burden of security teams.
If you are interested in learning more, check out our whitepaper: The Three Common Use Cases for Cloud Threats Detection, or contact us today!