Although automated security tools detect 80% of security threats to an organization, the remaining 20% are often the most sophisticated and damaging to your business. With each global data breach costing an organization over $4 million yearly, threat-hunting tools that offer comprehensive threat coverage are a must-have for your security team.
This article compares the top threat-hunting tools for 2023, so you’ll have the information you need to select the right one for your organization.
What is threat-hunting?
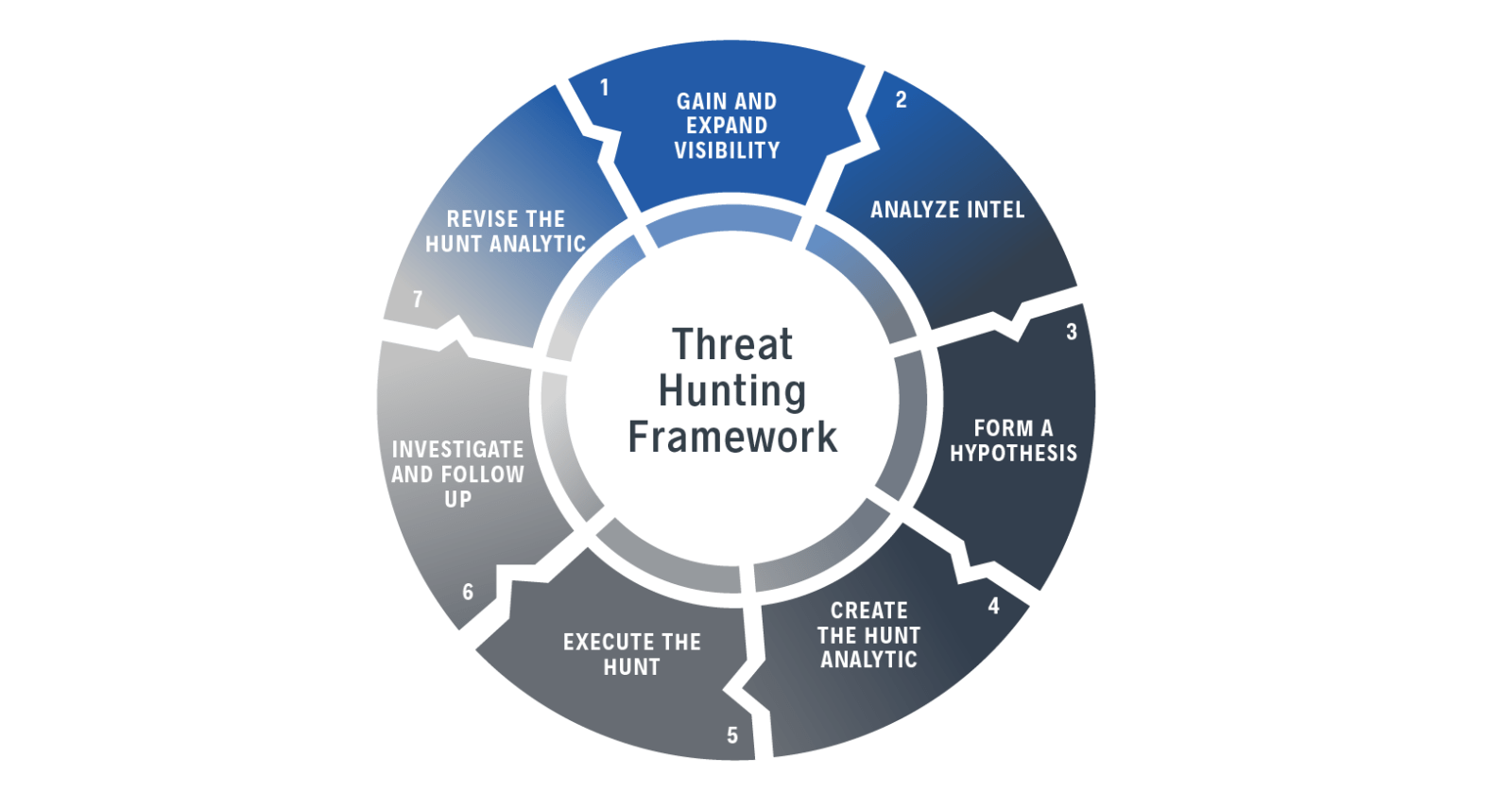
Threat-hunting is a proactive approach to identifying security threats in a system before they lead to a breach with irreparable consequences. It complements automated threat detection and intelligence tools to check for threats or hidden malware that may have been missed.
Attackers may be inside a network for months, flying under the radar before they suddenly attack. Meanwhile, they are finding sensitive data and moving laterally within your environment. A reactive, “ad-hoc” approach to finding suspicious activity is not enough because, by the time you detect an attack, it might be too late to remediate. Threat-hunting works based on the assumption that there is an attack, continuously monitoring activities and traffic within a system.
5 Types of threat-hunting tools
Threat-hunting tools are classified into a few main categories:
- Security Monitoring – Includes tools such as firewalls, antivirus, and endpoint security solutions.
- Security Information and Event Management (SIEM) systems –These tools turn raw data into actionable insights that help security teams detect security threats nearly in real time. However, note that SIEMs are rule-based, and if you patch or upgrade something, such rules can break.
- Behavior Analytics – Visual reports use statistics and intelligence to detect correlations and patterns.
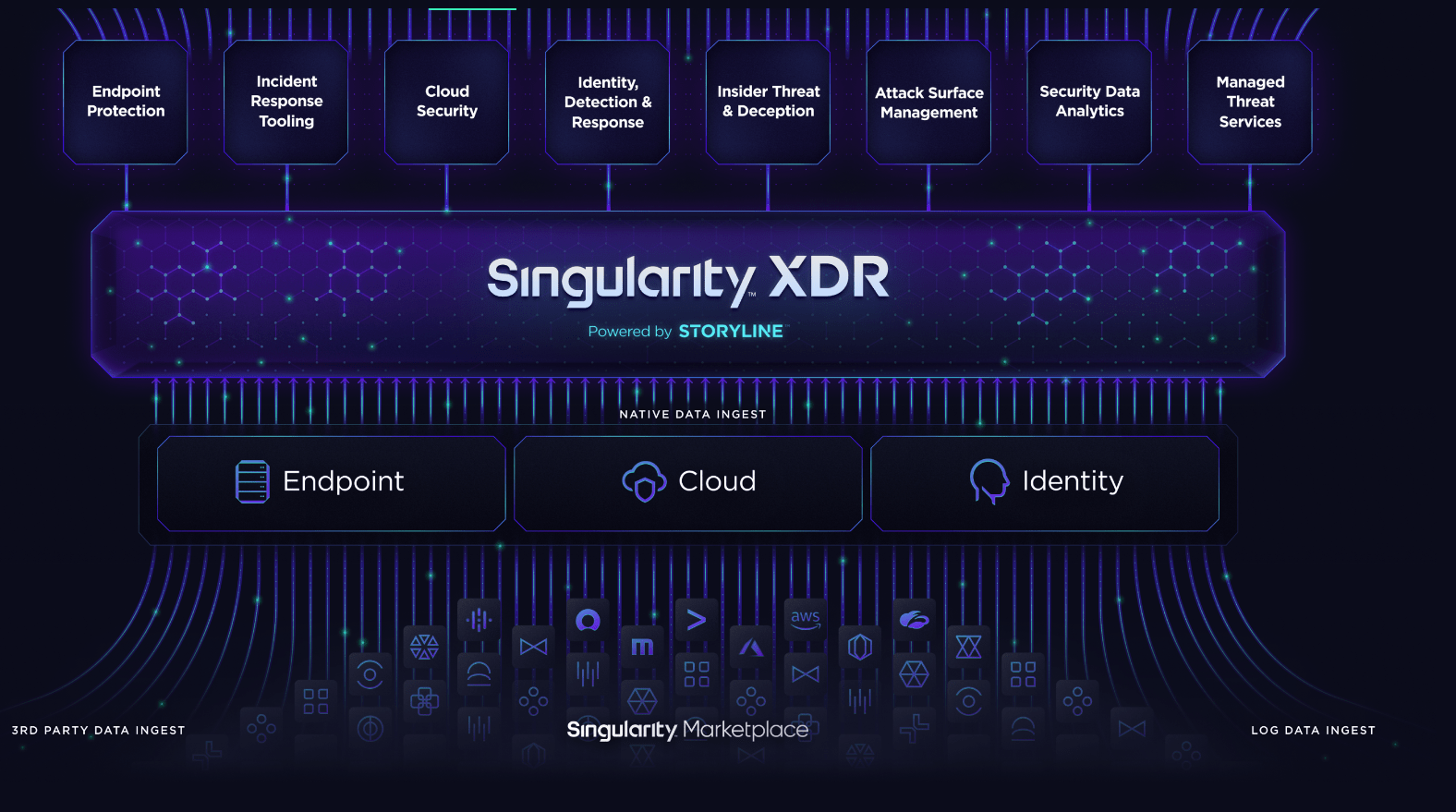
- Extended Detection and Response (XDR) – Enables proactive prevention against cyber threats through unified and integrated visibility and analytics across an organization’s assets.
- Network Detection and Response (NDR) – Detects cyber threats using artificial intelligence (AI), machine learning (ML), and data analysis.
- Cloud Detection and Response (CDR) – Identifies threats specific to cloud infrastructure and applications through collection and analysis of cloud logs and telemetry.
Benefits of threat-hunting tools
Threat-hunting tools provide the opportunity to have a proactive approach rather than a reactive one to security. As a result, it strengthens your organization’s security defenses. The benefits of threat-hunting include:
- Proactively identifying security risks
- Reducing investigation time to detect attacks
- Giving analysts a better overall view of the state of the organization’s security
- Reducing false positives and improving SOC efficiency
The must-have features in threat-hunting tools
So you know the benefits of adding a threat-hunting tool to your security toolkit, and now what? Choosing a threat-hunting tool that works for you is the challenging part. While you need to take into consideration your company’s security needs, there are some critical features in threat-hunting tools you should look out for:
Data aggregation
The more data a threat-hunting tool gathers, the more able it is to accurately predict trends, prioritize and remediate vulnerabilities, and deliver better security.
Automated response
Security teams can only avoid the increasing number of threats they face and protect the network from attacks with automated responses.
Threat Hunting Cloud Features to Look for:
Runtime Observability
Analyzes cloud activities and traffic to prioritize and focus on malicious behaviors that require an immediate response.
CSPM and CIEM
Leverage input from CSPM (Cloud Security Posture Management) and CIEM (Cloud Infrastructure and Entitlement Management) to better contextualize the user behavior to understand if there are anomalous activities in your cloud or just one-offs.
Top 10 threat-hunting tools for InfoSec Practitioners in 2023
Many tools are available in the market, so we did some heavy work for you by selecting just ten. Without further ado, these are the top 10 threat-hunting tools for 2023:
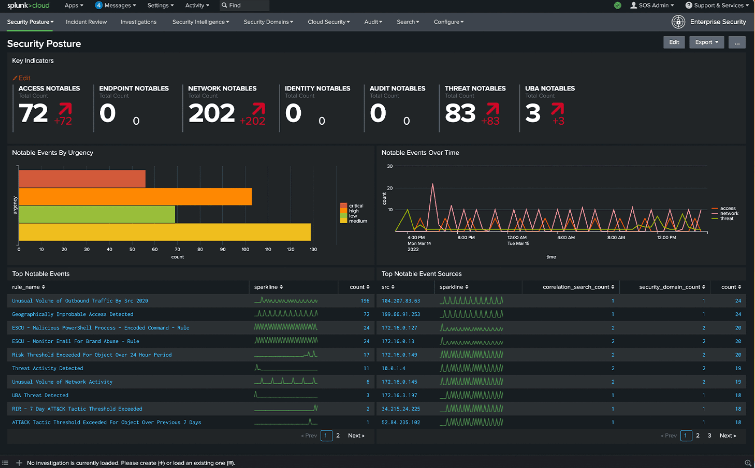
1. Splunk Enterprise Security
Splunk Enterprise Security is a security information and event management (SIEM) product. Its customizable dashboard delivers data-driven insights to protect businesses and mitigate security risks.
Main features:
- Threat topology – Maps all the associated risks and threat objects to understand the size and scope of a security incident fully.
- MITRE ATT&CK Framework Matrix – Enables security teams to understand incidents in context better.
- Security posture dashboard – Delivers insight into real-time events for visibility across your organization.
Best for Monitoring and searching through big data.
“Splunk ES continuously monitors our system for potential threats and alerts us in real-time so that we can prevent the threats before they mess up our system. I like its access anomalies dashboard, which allows us to identify any breach and suspicious activity from users.”
2. Skyhawk Synthesis
Skyhawk security is a complete cloud security solution offering Cloud Threat Detection and Response (CDR), Cloud Infrastructure and Entitlement Management (CIEM), and Cloud Security Posture Management (CSPM). While it may not be considered a classic threat-hunting tool, it offers key threat detection capabilities to protect your cloud infrastructure. It delivers both aspects of a comprehensive cloud security strategy – prevention and detection.
Main features:
- Identified Misconfigurations: Standard capabilities to identify and eliminate misconfigurations that threat actors can exploit to penetrate your cloud.
- Reduce the attack surface: Identifies unused permissions so they can be shut down, reducing opportunities for threat actors.
- Malicious Behavior Indicators (MBIs) – Activities that have been identified as risky behaviors that require an investigation and may pose a threat to your business based on our own AI and ML modeling of what is normal for your cloud
- Realalerts – Focuses on activities that are an impending threat to your cloud that could imminently cause to a breach. Realerts are unlike alerts from other tools. These are not one-offs or anomalies, these are indicative of a real incident.
- Runtime observability – Monitors activities in the runtime and uses the configurations and permissions to provide additional context to discover if the business is being exploited or the behavior is just an anomaly.
- Cloud Security Posture Management (CSPM): Free identification of cloud misconfigurations and compliance and governance management.
- Cloud Infrastructure and Entitlement Management (CIEM): Automation of the management of user permissions to easily implement a zero trust approach across cloud and multi-cloud environments.
- Real-time remediation to close any incidents automatically.
Best for Customers of Amazon AWS, Microsoft Azure and Google GCP clouds.
“Reputation and security are pillars for us. We configured the product in 5 minutes, and after only 24 hours, we were able to obtain the first insights useful to tune our infrastructure. Through the product, we can be notified if something changes and remediate quickly.”
3. Cisco Umbrella
Cisco Umbrella is a cloud security solution that detects current and emerging threats. It processes over 600 billion internet requests per day and protects against phishing, malware, and ransomware attacks.
Main features:
- Secure engine gateway (SWG) – The SWG inspects and controls traffic using cloud-native capabilities to reduce risk. It includes visibility into web traffic, antivirus and advanced malware protection, decryption, sandboxing, granular app activity, and content control.
- DNS-layered security – Blocks malicious domains, IP addresses, and cloud applications before organizations connect to the internet.
- Cloud-delivered firewall- Reduces complexity and improves security with increasing remote locations and SaaS usage.
Best for Cloud-delivered threat intelligence and detection.
“We like that the interface is very intuitive, and the L7 firewall can block many spurious and non-approved applications and peer-to-peer file sharing and torrenting from happening in the office or on any office computers.”
4. Memcyco
Memcyco has a threat-hunting tool for specific threats – domain spoofing. Its Proof-of-Source Authenticity Suite protects businesses and their clients from real-time fraud and offers brand impersonation prevention.
Main features:
- Digital brand watermark – Authenticates your website for every visitor to ensure the website they visit is secure and safe.
- Brandjacking Detection and Prevention – Offers real-time protection at the point of impact and detection of plans for an attack before they occur.
- End-user Brandjacking Protection – Real-time customer fraud prevention to alert users before they enter spoofed sites.
Best for Domain and website protection.
“We are very satisfied with Memcyco and recommend it fully. It has finally provided us with a solution to plug a big gap in our cyber security needs. Our students and professors can now browse, upload, and share on our sites, fully assured that they are in their desired place on the web. We are excited to see what other capabilities Memcyco will add to its suite and what other innovative features it will introduce.”
5. Spectral
Spectral defends against exposed API keys, tokens, credentials, and high-risk security misconfigurations in code, assets, and infrastructure. Its hybrid scanning engine acts as a control plane over source code and other developer assets.
Main features:
- Integrate with your continuous integration (CI) – This includes support for Jenkins, Azure, and others.
- Monitor out-of-sight assets – Includes codebases, logs, and other sensitive intellectual property that may have unintentionally been exposed in public-facing repositories.
- Shift-left log shipping integration – Seamlessly integrates into your log shipping to protect the organization before sensitive data leaves the perimeter.
Best for: Developers, DevOps, and security teams.
“We’ve solved the issue of having zero visibility into our ADO environment with SpectralOps. Integrates easily into ADO, allowing us to track down exposures we previously had no knowledge about.”
6. Cybereason
Cybereason is an XDR platform that detects malicious activity automatically, ending attacks at the endpoint, in the cloud, and across the entire enterprise ecosystem.
Main features:
- Next-gen antivirus and antivirus (NGAV and AV) – Combines signature-based, behavioral, and machine-learning approaches to end threats in real-time.
- Anti-Ransomware – Automatically detect and block unknown, fileless, and MBR-based ransomware strains.
- Endpoint Detection and Response (EDR) – Automates tasks to make it easier for a SOC team to understand the impact of a security threat.
- Managed Detection and Response (MDR) – Continuously delivers proactive protection and remediation.
Best for Ransomware protection.
“Cybereason is a great resource for companies that need to stay protected from ransomware. The Cybereason platform combines EDR, next-gen antivirus, and proactive threat-hunting to deliver context-rich analysis. The platform is built to be self-learning and more accurate as time goes on. This product is great for companies that are new to cybersecurity.”
7. Secureworks
Secureworks Taegis ManagedXDR offers continuous threat detection, investigation, and response. The services also include 24/7 access to its security analysts.
Main features:
- Endpoint Detection and Response (EDR) + Extended Detection and Response – Near real-time detection and response via native support of Windows, MacOS, and Linux to detect endpoint compromises earlier.
- Vulnerability management – Automated vulnerability management that improves through self-learning AI capabilities.
- Intrusion Detection and Protection System (IDPS) – This proprietary system includes network intelligence, threat intelligence, device management, and support.
Best for: Threat Intelligence.
“Taegis XDR takes a giant load off of my plate. Anytime there is an issue, an investigation takes place. It makes an infosec guy feel much more comfortable knowing that we’re being looked out for, even when we can’t do it ourselves.”
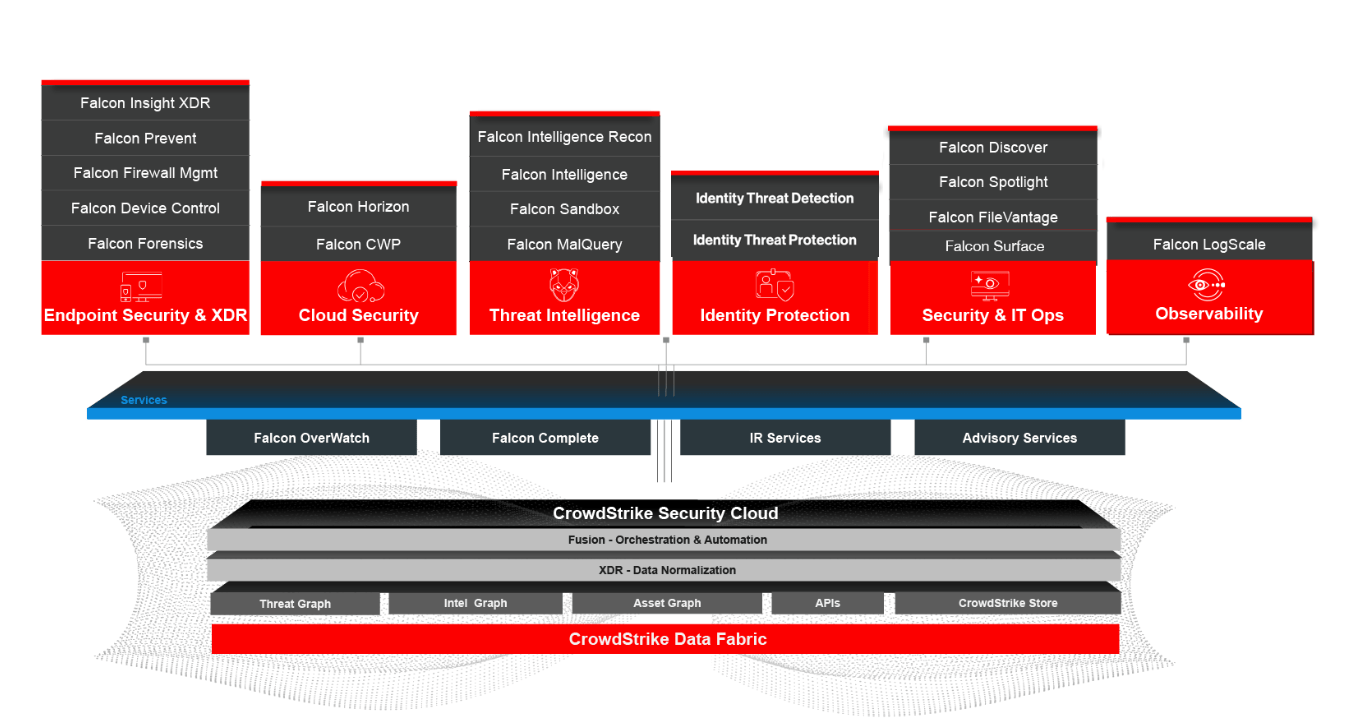
8. Crowdstrike
Crowdstrike is a cloud workload and endpoint protection solution that offers antivirus security solutions. It focuses on protecting endpoints, cloud workloads, and identity on data.
Main features:
- Identify protection – Delivers comprehensive protection against identify-based attacks in real-time.
- Security and IT operations – This includes IT hygiene, vulnerability management, and patching combined with malware searching and sandbox analysis to provide security teams with deep context and predictive capabilities.
Best for: Endpoint detection and response (EDR).
“By working in Crowdstrike, we can easily understand TTPs and how to respond/react to them. The process tree diagram helps a lot in understanding the alert. It gives more inside and meaningful information than any other EDR solution.”
9. SentinelOne
SentinelOne is an autonomous security solution for cloud, endpoint, and security environments that protects organizations’ endpoints from known and unknown threats.
Main features:
- Analytics – The platform allows unstructured, structured, and semi-structured data to be ingested in real-time from any product or platform to enable a single source for prioritized alerts.
- Detection and Response – The platform uses the MITRE ATT&CK framework to accelerate threat-hunting and make investigation easier.
- Integrated threat intelligence – Detection and enrichment with third-party sources for more accurate risk scoring of IOCs such as hashes, vulnerabilities, and domains.
Best for: Endpoint security.
“As a small business with no in-house IT department, achieving NIST/CMMC compliance for cybersecurity seemed like an impossible task. Utilizing SentinelOne helps us reach compliance on so many of our controls.”
10.VMware Carbon Black
VMware Carbon Black delivers endpoint protection, thwarting attacks by analyzing system events to identify suspicious activity, automating investigation workflows, and preventing attackers from malicious use of legitimate tools.
Main features:
- Next-gen antivirus and behavioral Endpoint Detection and Response (EDR) – Continuously analyze attacker behavior patterns to identify and proactively respond to known and unknown attacks.
- Managed detection – A security team of expert analysts to deliver context and validation into root causes and monthly reporting.
- Audit and remediation – Real-time assessment of the current security state to maximize the security of an organization’s devices.
Best for: Endpoint protection.
“I appreciate the instant malware search abilities in the Admin portal. It allows you to click a link that contains all the threat vectors and immediately scans your entire network for the threat. It also has an in-depth investigation section that you can use to track the history of a file to determine how it got into your network.”
A proactive approach to detecting security threats
New types of security threats unfold every day. On top of that, your SOC team is overwhelmed with false positives that take too much of their time and aren’t a real threat. This shouldn’t be the case. Advanced threat-hunting tools such as Skyhawk can show you the complete picture of an attack, giving you full runtime visibility to understand your attacker’s journey and prevent real threats, almost in real-time. Want to learn more about Skyhawk’s runtime security? Get a free CSPM here.