Walking around cyber security trade shows, you can’t help but notice how standard pen tester booths are. Pen testers, or penetration testers, simulate an unauthorized attack where they purposely try to infiltrate your network or cloud to uncover security gaps. It’s just like an actual attack made by an ethical hacker you paid for.
Why are such services so in demand? Because the cyber threat landscape exploded in the past few years. Cloud exploitation grew by 95% in 2022 compared to the previous year, and the situation will likely worsen.
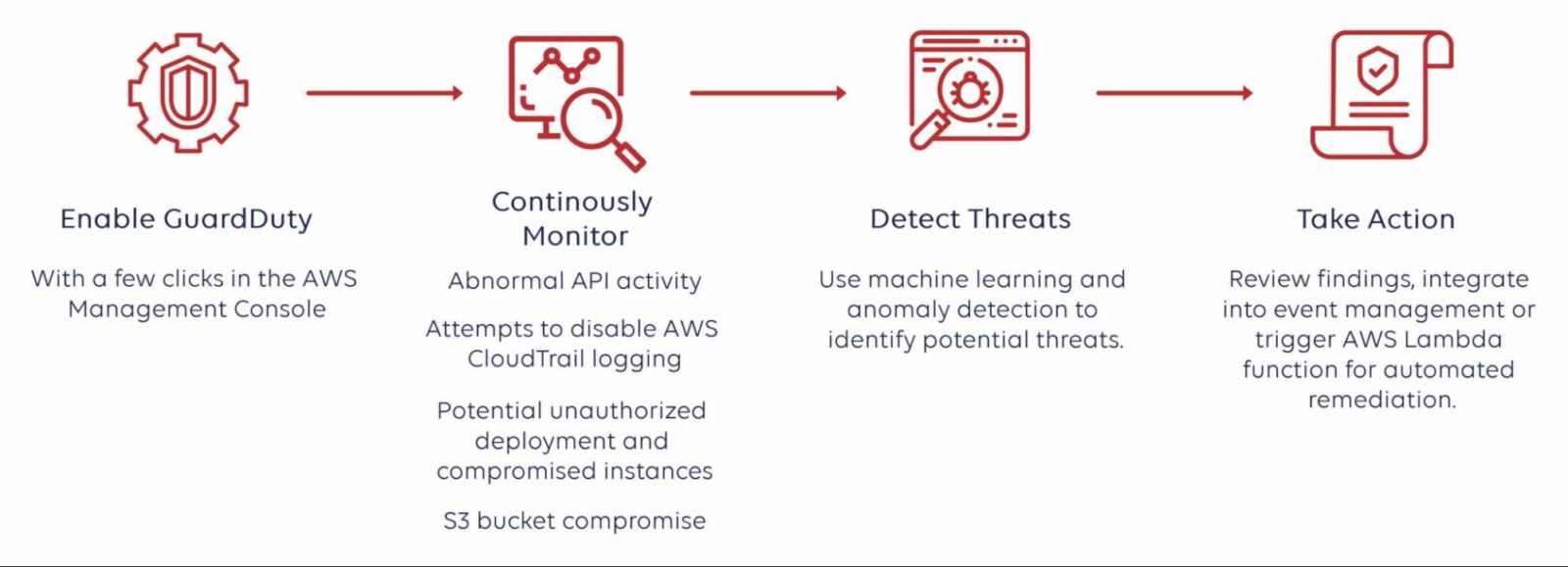
Luckily for AWS users, AWS offers GuardDuty to continuously monitor your AWS accounts, detect threats and automate threat response. This article delves deep into the GuardDuty world, exploring its capabilities, use cases, advantages, and potential gaps.
What is AWS GuardDuty?
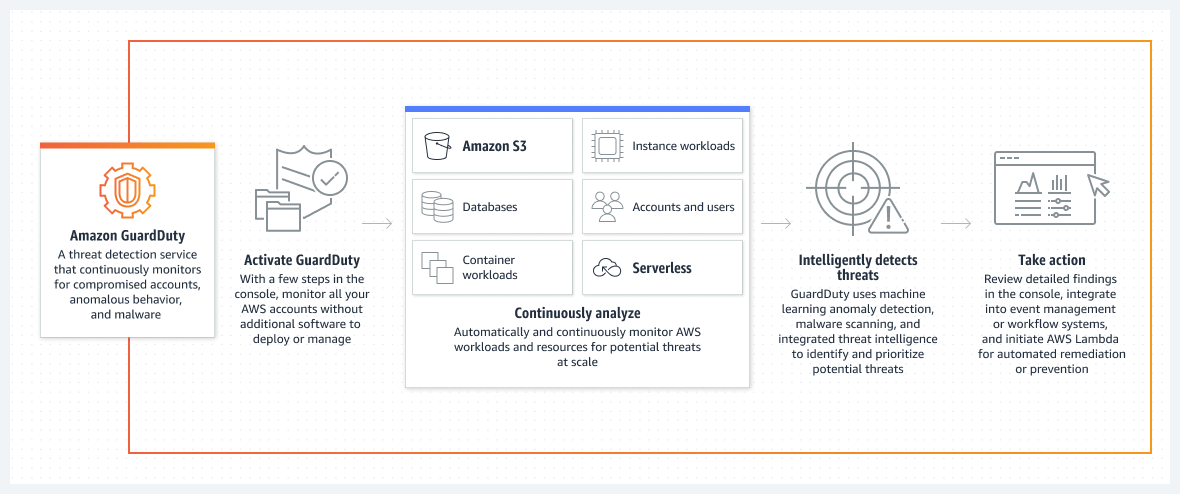
GuardDuty is a real-time threat detection service that constantly monitors your AWS environment. It uses an established baseline and updated continuous threat intelligence (think of a catalog of malevolent IP addresses) to find and respond to threats within your AWS environment.
GuardDuty collects and analyzes data from three sources (AWS CloudTrail Event logs, VPC Flow logs, and DNS logs) to detect unexpected or unwanted behavior, deliver findings, and even offer some immediate, pre-programmed remediation. The tool identifies three types of AWS cloud threats:
- Attacker reconnaissance: Failed login patterns, odd API activity, and port scanning could indicate such action.
- Compromised resources: Cryptojacking, anomalous surges in network traffic, and temporary access to Elastic Compute Cloud (EC2) instances via an external IP address are all potential harbingers for such a compromise.
- Compromised accounts: API calls from an unexpected location, attempts to disable CloudTrail, and unusual instance or infrastructure deployments are examples of possibly compromised accounts.
AWS GuardDuty use cases
Here are a few simple use cases to show what kind of detection you could expect while employing GuardDuty.
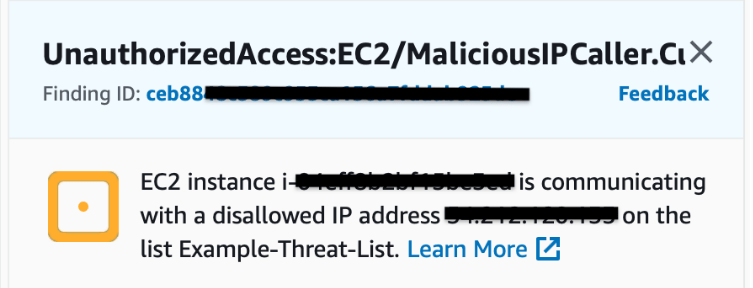
1. Compromised EC2 (Elastic Cloud)
In this use case, GuardDuty finds that an IP address on a threat list is in communication with our EC2 instance. GuardDuty alerts the user to this event:
Using CloudWatch, we can use the event rule to trigger an SNS topic and a Lambda function. The SNS sends an alert email to our designated security personnel, and the Lambda function isolates the compromised instance.
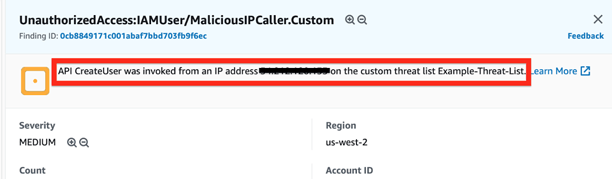
2. Compromised IAM Credentials
In this scenario, a phishing attack has resulted in a compromised AWS account. We suspected the user account was being compromised, so we added it to a threat list in advance – we can use the same IP list from the previous example. The alert looks something like this:
In this case, once we have the compromised access key ID, we can make it ‘inactive’ in the IAM > Users > Security credentials tab.
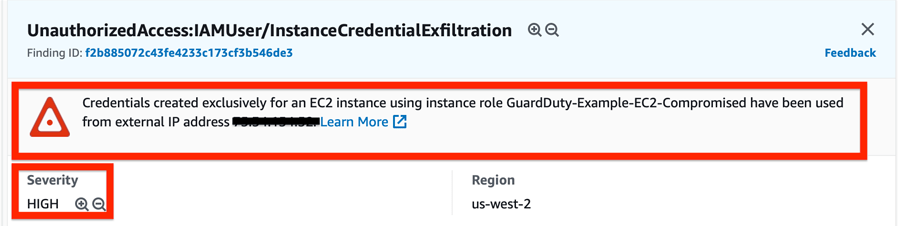
3. IAM Role Credential Exfiltration
An attacker compromises an EC2 instance and exfiltrates the IAM role credentials via the metadata service. The API calls are being done with a CLI user. In this case, GuardDuty will find that credentials were created just for the use of API calls:
Notice how the severity of this alert, as opposed to the other two, is high – this is a live event and should be responded to immediately. Using CloudWatch, we can use the event rule to trigger an SNS topic and a Lambda function. The SNS sends an alert email to our designated security personnel, and the Lambda function attaches an IAM policy to the role, revoking all active sessions. Any further attempts by our attacker to use this role to make API calls will be immediately denied.
There are many other scenarios where having one tool watching your entire AWS infrastructure could be very useful – especially when done continuously. For even tighter security, you can add pre-made lists of problematic IPs or roles and create whatever events or Lambdas you wish for tailor-fitting responses to your perceived threats. All the alerts are in a single place – your GuardDuty findings console, and you can easily access most other relevant remediation locations directly from there.
10 Pros and Cons of AWS GuardDuty
Top 5 pros of AWS GuardDuty
1. Easy deployment
Using your AWS’s Management Console, GuardDuty could be quickly launched for single or multiple accounts. Once deployed, GuardDuty will start monitoring your accounts in close to real-time by examining three primary data sources – AWS CloudTrail Event logs, VPC Flow logs, and DNS logs.
You don’t have to review these logs; they accurately show almost every notable action on your account. Since launching GuardDuty requires no extra tool, you can set it up without interrupting your daily workflow.
2. Easy integration with other AWS tools
Since GuardDuty is an AWS tool, it is closely associated with additional AWS security and logging tools. Regardless of your AWS environment set-up, GuardDuty would know how to interface with it and with whatever tools you have monitoring it.
3. Updated security intelligence
GuardDuty leverages AWS’s threat knowledge base, which is constantly updated with the latest security findings. Context is essential when dealing with security threats, as a known dangerous IP address can escalate a threat from probable to definite. Like other infrastructure, you can trust AWS always to strive to keep its threat intelligence databases as up-to-date as possible.
4. Near real-time threat detection
Using the various logs it ingests, GuardDuty continually analyzes your environment, users, and resource allocation in near to real-time. It would take an entire IT team pouring over these logs constantly even to come close to matching its speed.
5. Cost-effectiveness
GuardDuty is usually more affordable than other security services. It’s a fully managed service. Thus AWS handles infrastructure and upkeep, so you don’t have to. There are no up-front expenses or long-term commitments; you simply pay for what you use.
Top 5 cons of AWS GuardDuty
1. Support for AWS only
GuardDuty works for AWS cloud environments only. Therefore, using other cloud providers or a multi-cloud approach, you will need other threat detection tools to protect all your domains. If you are using other security tools outside of AWS, you probably won’t be able to incorporate them with GuardDuty, which might limit the effectiveness of your security operations. With 98% of companies using multi-cloud infrastructure, this lack of compatibility and extensibility may be an issue.
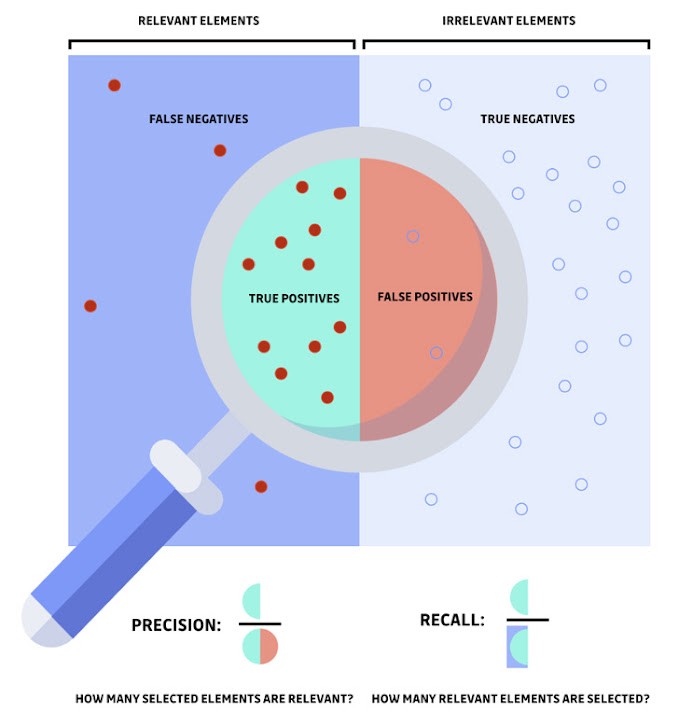
2. False positives
GuardDuty evaluates data to find potential security issues. But occasionally, this can lead to false positives—when perfectly normal activity is marked as suspicious. As a result, security staff may get overburdened with false alarms and fail to recognize genuine threats. Security Information and Event Management (SIEM) tools lack the context to determine whether an attack is really an attack or just unusual activity.
3. Limited remediation
Our use case examples show you can build SNS and Lambda scenarios to deal with various problems. Still, you can only do that for eventualities you can imagine. Most attackers aren’t considerate enough to only use well-established attack patterns and never innovate their tools and practices. Therefore, you may miss some of the more unlikely novel attacks or find no possible remediation in your pre-programmed arsenal.
4. Limited customization
GuardDuty has limited customization options. There is no possibility to build custom rules; instead, the service offers a set of established criteria to identify security issues. If you have unique needs or potential problems, you might find that there are better tools for you than GuardDuty.
5. Dependency on AWS CloudTrail
GuardDuty depends on CloudTrail to collect much of its information. CloudTrail is a service that provides a record of actions taken by a user, role, or AWS service. If there is any activity that doesn’t generate any record, for whatever reason, it is essentially invisible to GuradDuty.
AWS GuardDuty and Skyhawk: a powerful duo
Using machine learning, Skyhawk Synthesis can track ongoing suspicious behavior and aggregate them into Malicious Behaviour Indicators (MBI). Data from GuardDuty is incorporated into the overall attack story that Skyhawk Synthesis has created, showing a complete view of the malicious behaviors in your environment.
- Correlate alerts and improve productivity. Using Skyhawk for threat detection goes beyond anomaly, and event detection to reduce the number of alerts security teams see – typically, our customers have fewer than 20% of the alerts that other tools provide. We aggregate and correlate alerts from GuardDuty and our machine learning models, scoring them to only alert on sequences of behaviors representing real-time threats.
- Context is King. Skyhawk Synthesis connects the dots, providing visibility and simple explanations for correlated, relevant threats in runtime that represent actual incidents. No need to wade through hundreds of log files to understand what alerts mean; Skyhawk provides contextualized evidence so that security analysts can understand the root cause of alerts and resolve them – fast.
- Reduce the cost of data ingestion. When organizations use Amazon GuardDuty with Skyhawk, they do not need to activate the collection of VPC flow logs, making the cost of adding breach prevention from Skyhawk negligible. Synthesis ingests and analyzes information from several AWS security tools and processes this information so that your teams don’t need to.
The intelligent threats of the future
AI is all the rage nowadays, and companies are constantly looking for ways to make their product include at least one AI feature to appease social media and their shareholders. Slightly less obvious is that many malicious actors are already looking into using AI to help them create better malware and penetration tools. The cyber arms race has begun, and if you don’t have some form of AI, you have probably already lost.
Skyhawk Synthesis leverages three levels of machine learning models that are updated daily, ensuring no drift and making it very difficult for threat actors to avoid Skyhawk’s threat detection capabilities. GuardDuty also utilizes ML and AI, ensuring your threat intelligence is as intelligent as possible.
Learn more about how you can discover real alerts here.